IDEMIA fixes vulnerability that can allow threat actors to open doors remotely
IDEMIA, one of the largest vendors of biometrics authentication solutions, has fixed last week a series of security flaws, including a major vulnerability that would have allowed threat actors to hijack devices and open doors remotely.
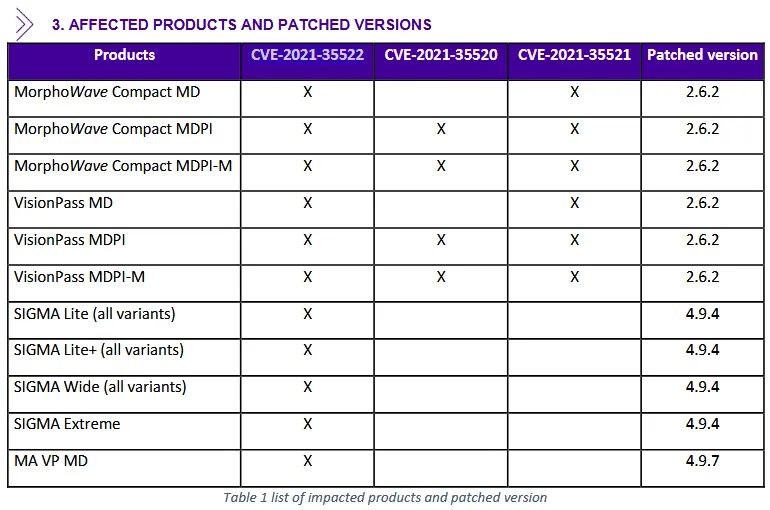
Tracked as CVE-2021-35522, the vulnerability impacted IDEMIA devices like VisionPass facial recognition devices, SIGMA fingerprint terminals, and MorphoWave and MorphoAccess vein and fingerprint authentication solutions.
The bug, found by Russian security firm Positive Technologies, was considered incredibly dangerous and received a "critical" rating and a severity score of 9.8/10 on the CVSSv3 scale.
Described as a buffer overflow in the Thrift protocol network packet design, the bug can allow threat actors with LAN or WAN access to an unpatched device to take over its firmware and control its features.
"Exploitation of this vulnerability allows attackers to bypass the biometric identification provided by the IDEMIA devices listed above," said Vladimir Nazarov, Head of ICS Security, Positive Technologies. "As a result, criminals can, for example, remotely open doors controlled by the device and enter secured areas."
IDEMIA released patches last week [PDF], including two fixes for two other issues Nazarov's team found but were not as dangerous.
"As technology evolves fast, it is normal for a software to be updated on a regular basis to respond to new risks and constraints and strengthen user security," an IDEMIA spokesperson told The Record in an email earlier today.
"As soon as we have identified the failure in the solution, all necessary corrective technical measures have been taken immediately and have been communicated to our users."
"In the process of doing so, we worked hand-in-hand with Positive Technologies," IDEMIA added.
The French company is now urging its customers to apply the firmware patches and prevent abuse of this vulnerability for intrusions into protected premises.
According to IDEMIA's website, its devices are often used in corporate headquarters, airports, banks, data centers
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



