Popular IBM file transfer tool vulnerable to cyberattacks, CISA says
The IBM Aspera Faspex file transfer tool used by dozens of large organizations and businesses has a serious bug that malicious hackers are actively exploiting, according to the Cybersecurity and Infrastructure Security Agency (CISA).
CISA added the bug — named CVE-2022-47986 — to its catalog of known exploited vulnerabilities this week alongside two other bugs affecting business communication platform Mitel.
The agency said the IBM vulnerability poses “significant risks to the federal enterprise.” CISA directs its alerts at the federal government, but they often apply widely to the private sector as well.
The announcement follows several warnings from security researchers over the last month. IBM issued a patch on January 18.
Federal civilian agencies have until March 14 to patch the bug, which carries a CVSS score of 9.8 out of 10.
Bud Broomhead, CEO of cybersecurity company Viakoo, said Aspera is so widely used that it won an Emmy in 2014 for enabling faster media production workflows because it allowed companies to send large video files quickly.
For any company transferring large datasets — like genomics and biomedical research, media production, military signals intelligence, or financial services — Aspera was likely the go-to solution for many years, Broomhead explained.
Broomhead added that the vulnerability is easy to exploit and allows a remote attacker to take actions on a system without having to get around network authentication processes.
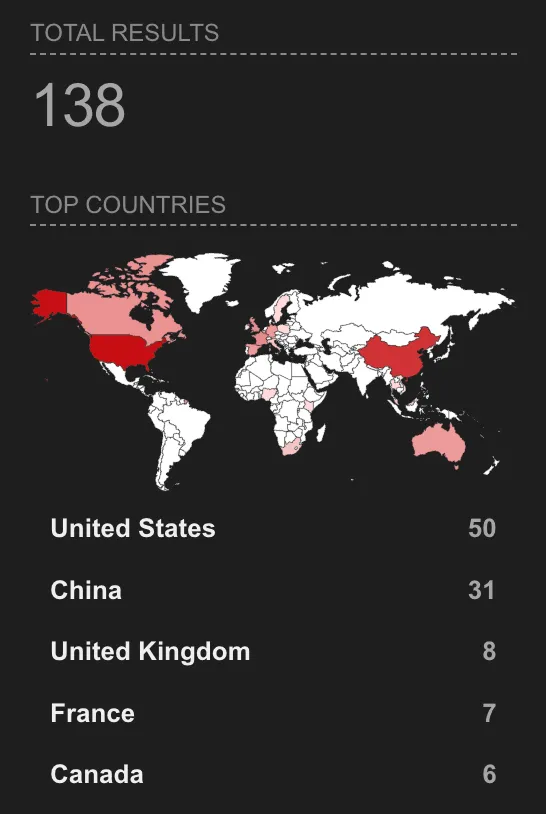
A search on internet scanning tool Shodan shows 138 Aspera Faspex instances exposed to the internet. Cybersecurity firm ShadowServer also confirmed that it has seen exploitation attempts since IBM published the patch.
Security company AssetNote said it notified IBM of the vulnerability on October 6 and waited a week after the patch was released before posting the exploit code on its blog.
Nucleus Security’s Ryan Cribelar said the tool is used by large companies to transfer large files or large data sets quickly and securely over long distances.
“It is used by all sorts of industries from finance to healthcare to government. It is a popular IBM product, so you can assume a large customer base purely from how long the product has been around, and the fact that shops usually use multiple IBM products if they are using one,” he said.
The bug is enticing to attackers for at least two reasons, Cribelar said.
"It might live on a device that doesn't get as consistent scanning coverage as other devices, and the maintaining of the device — and who is responsible — could easily get lost over time as vulnerability management programs change in-house," he said. "These two factors can allow for the vulnerability to have a longer lifetime on the device."
Cribelar added that the vulnerable software is typically found in the outer perimeter of networks, making it a valuable portal for hackers to gain persistence in a victim's system without the likelihood of being discovered quickly.
It's latest file transfer tool to be exploited following the widespread attacks on the GoAnywhere MFT file-transfer product last week that caused a breach at one of the largest healthcare providers in the U.S. affecting more than 1 million people.
The Clop ransomware group told BleepingComputer that it hacked into more than 130 organizations through the GoAnywhere vulnerability.
Vulnerabilities affecting another file transfer provider, Accellion, were used repeatedly to target financial institutions, government agencies, universities and corporations in 2021.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.

