Hundreds of WordPress sites defaced in fake ransomware attacks
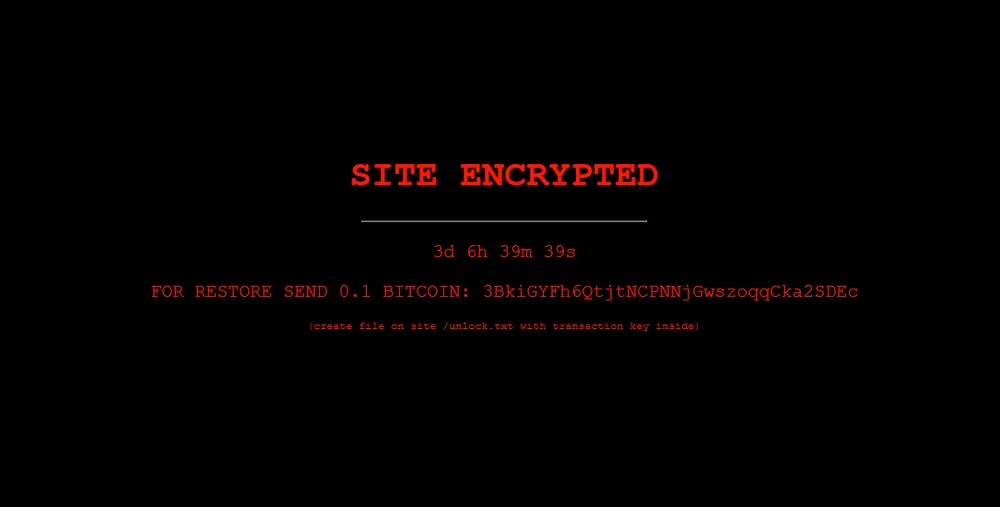
Hundreds of WordPress sites have been defaced over the weekend with a message claiming that the site's data was encrypted in what security firm Sucuri has described as "fake ransomware."
In a copy of the message—included above—the attackers request 0.1 bitcoins (~$6,100) to unlock the affected websites.
So far, the campaign has hit at least 300 sites, according to a Google search result for the text included in the ransom note.
But at a closer look, the ransom message only appears on a few selected pages of a site's domain and not the entire website, which explains why nobody has paid the ransom demand so far.
Furthermore, pages that were cached in Google search results as impacted appear to have been cleaned in the meantime, suggesting site owners had no difficulty in restoring their sites.
Examinations carried out by The Record on sites that are still showing the message also found no signs of any form of encryption or error that would prevent users from using the rest of the website. Sucuri said the ransom message had been generated by exploiting a vulnerability in a WordPress plugin named Directorist that was already installed on the affected sites.
Based on the current evidence, the attack appears to be a form of "scareware" meant to frighten non-technical website owners into paying the ransom demand, but one that has failed thus far.
But even if the scenario that the attackers would have managed to encrypt a site's data, ransomware attacks against websites have rarely succeeded in the past. This is because most site owners have the ability to restore their sites from backups, replacing the encrypted files with clean versions with the push of a button from the web hosting control panels.
Past incidents where ransomware was leveraged against websites but eventually failed include cases such as:
- Linux.Encoder.1 - the first known Linux-based ransomware targeted web servers back in November 2015.
- CTB-Locker (web version) - targeted PHP sites in February 2016.
- KimcilWare - targeted Magento online stores in March 2016.
- Unnamed ransomware - targeted Drupal sites using an SQL injection vulnerability in May 2016.
- Heimdall - code released on GitHub was abused to ransom PHP sites in November 2016.
- EV Ransomware - targeted WordPress sites in August 2017.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.