Brazil-based botnet targets Spanish-speakers across Americas, Cisco says
Hackers suspected to be living in Brazil are using a previously unidentified botnet called to target the email inboxes of Spanish speakers across the Americas.
Researchers from Cisco’s Talos security team said the botnet, called “Horabot,” delivers a banking trojan and spam tool onto victim machines in a campaign that has been running since at least November 2020.
The attackers are mainly interested in using the tool to steal victim credentials and financial data, as well as to send phishing emails to all of the validated email IDs in a victim’s mailbox to spread the infection. A botnet is a group of computers that have been infected by malware, allowing a hacker to control them all.
This botnet is noteworthy in that it allows the hackers to take control of a victim’s Microsoft Outlook mailbox, exfiltrate every contact’s email address and send phishing emails in bulk with malicious HTML attachments, from within the organization’s own email servers. The attackers are using this technique to minimize the chances of their phishing infrastructure being tracked, the researchers explained.
“This is an effective social engineering technique that aids in compromising the victims, as the emails would have been sent from a known email address and delivered through a legitimate email server of legitimate organizations,” Cisco Talos threat researcher Chetan Raghuprasad told Recorded Future News.
“Such email addresses or email servers are usually whitelisted and pass through the Sender policy framework (SPF) checks at the recipient’s organization’s email servers. Also, it will become difficult for the defenders to track the attacker’s phishing infrastructure and block such emails.”
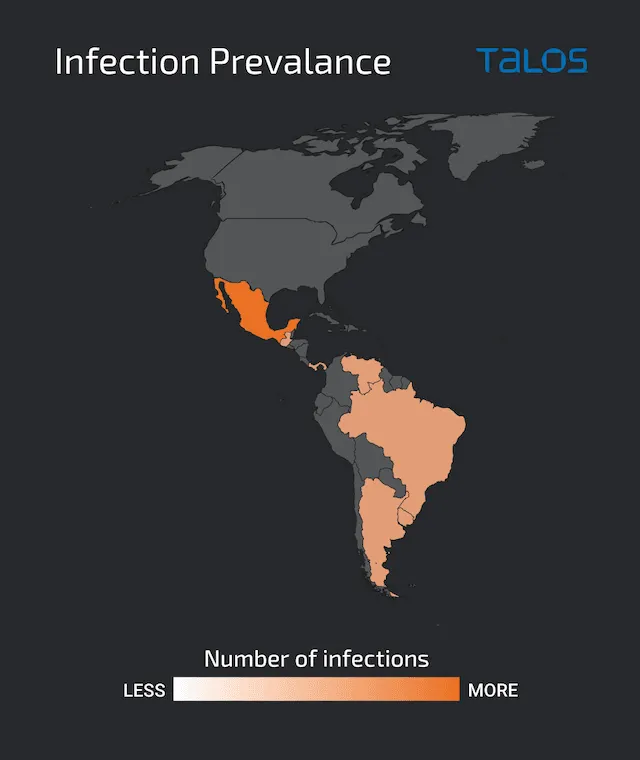
In a report released this week, Cisco researchers said the hackers “may be located in Brazil” because the domain registered to host the attackers tools and exfiltrated data was associated with someone based there.
Cisco said the domain name “resembled the legitimate Mexican Tax Agency domain, a tactic the attacker likely adopted to disguise malicious traffic.”
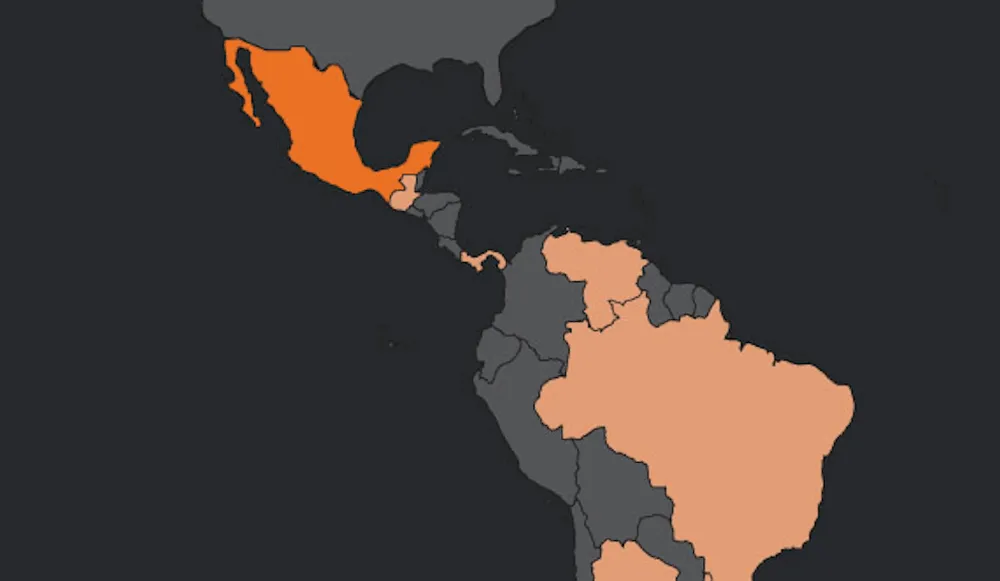
The campaign is mostly targeting people in Mexico, but the researchers have also seen infections in Uruguay, Brazil, Venezuela, Argentina, Guatemala and Panama.
The phishing emails analyzed by the researchers indicate that the gang is targeting organizations in several different business sectors including accounting, construction, engineering, investment and wholesale distribution.
The banking malware associated with the campaign collects a victim’s login credentials for various online accounts, information on their operating system and even certain keystrokes.
The researchers noted that the trojan also can steal the kind of one-time security codes or soft tokens typically used by online banking applications to verify users.
In addition to outlook, the spam tool was seen compromising Yahoo and Gmail webmail accounts, enabling the threat actor to take control of those mailboxes, exfiltrate their contacts’ email addresses, and send spam emails.
The infrastructure used by the attackers was registered in November 2020, indicating a possible date for when the campaign began.
A Spanish tax email
Cisco said most of the infections began with an income-tax themed phishing email written in Spanish.
The email purports to be a tax receipt notification and urges victims to open the attached malicious HTML file.
When opened, the HTML file attachment launches an embedded URL in the victim’s browser that redirects them to another malicious HTML file. Victims are then prompted to click and embedded link that downloads a RAR file.
If the RAR file is opened, several files are downloaded causing the machine to restart after 10 seconds. At least one of the malicious files is made to look legitimate by using the Internet Explorer icon.
“Talos found that the payloads employed by the attacker in this campaign are designed to steal sensitive information, evade detection and disseminate additional phishing emails to the victim’s contacts,” the researchers said.
“The banking trojan targets the victim’s sensitive information, such as login credentials and financial transaction security codes, and logs keystrokes and manipulates the victim machine’s clipboard data. The trojan also has anti-analysis and anti-detection capabilities to evade the sandbox and virtual environments.”
The researchers noted that the banking module “uses similar techniques as Brazilian banking trojans reported by other security researchers at ESET and Check Point in the past.”
The trojan even has remote desktop management capabilities, allowing hackers to create and delete directories, download files and more.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.