Hackers target Chinese language speakers with FatalRAT malware
Chinese-speaking users are being targeted with FatalRAT malware, spread via fake websites of popular apps, new research has found.
First discovered in August 2021, FatalRat malware can capture keystrokes, change a victim’s screen resolution, download and execute files, and steal or delete data stored in browsers.
So far, the researchers from cybersecurity company ESET have not attributed this campaign to any known hacker group, and the attackers’ goal is also not clear. They may be stealing information like web credentials to sell on underground forums or to use in other criminal campaigns.
Most of the attacks were observed between August 2022 and January 2023, targeting users in Taiwan, China and Hong Kong. A small number of cases were also recorded in Malaysia, Japan, the Philippines, Thailand, Singapore, Indonesia, and Myanmar.
Malicious websites
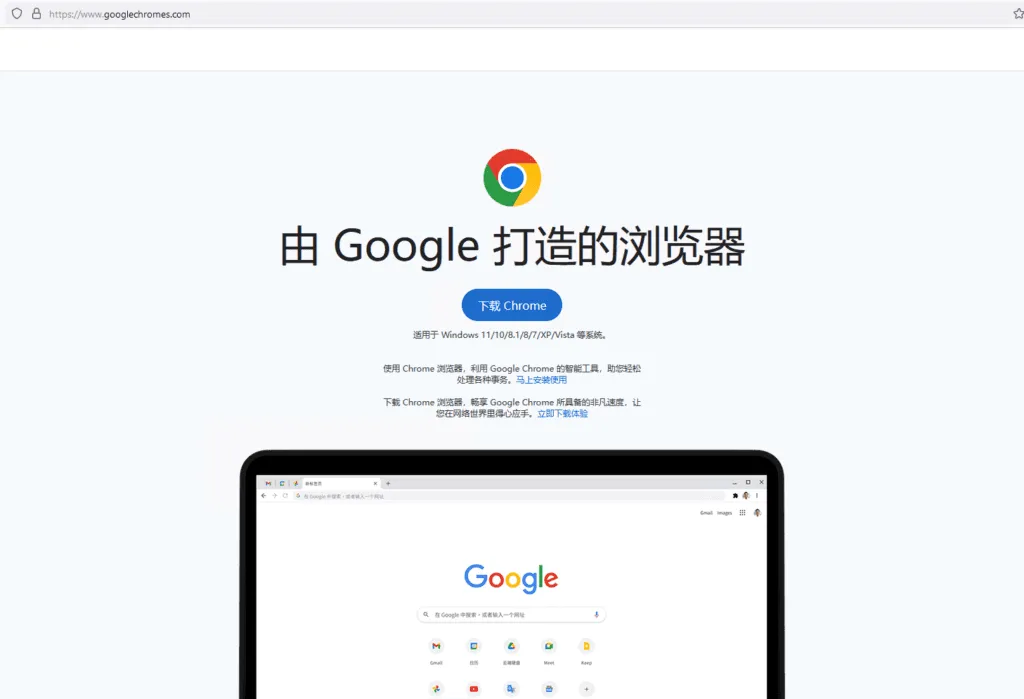
Hackers distributed the malware through fake websites of popular apps, including Google Chrome, Firefox, Telegram, WhatsApp, Signal and Skype. Some of the sites offered fake Chinese language versions of software that is not available in China, such as Telegram.
To lure users to a malicious website, hackers promoted them in Google search results. ESET said it reported these ads to Google and they were removed.
The attackers tried to make the domain names of the fake websites resemble the real names.
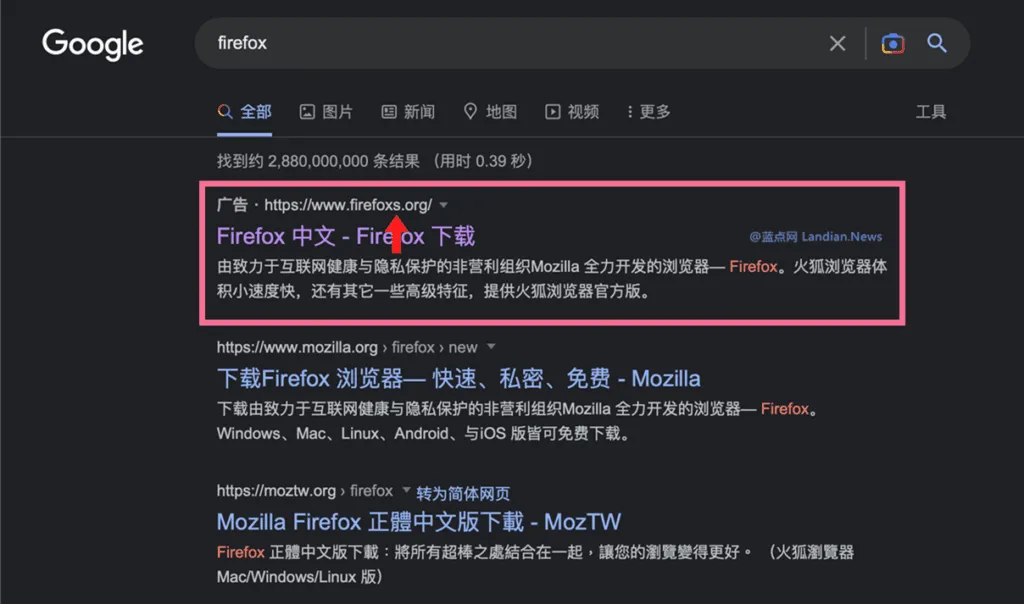
Malicious websites also looked identical to legitimate ones, with some translated into Chinese.
Malicious installers
The trojanized installers downloaded from the fake websites installed the real application on the user’s device to avoid detection. These installers were digitally signed .MSI files created with the free Windows installer tool.
The malicious installers dropped and executed the loader, as well as files needed to run the FatalRAT malware.
The FatalRAT version used in this campaign “is very similar” to the one documented in 2021.
The malware’s previous version was distributed through forums and Telegram channels and hidden in malicious links leading to fake software or media articles.
It used obfuscation techniques and antivirus evasion and could run several tests before fully infecting a system, checking for the existence of multiple virtual machine products, disk space, or the number of physical processors.
Given the broad range of users targeted in the most recent campaign, and the fact the malware could manipulate data from different browsers, the attack could have affected anyone, according to ESET.
Daryna Antoniuk
is a reporter for Recorded Future News based in Ukraine. She writes about cybersecurity startups, cyberattacks in Eastern Europe and the state of the cyberwar between Ukraine and Russia. She previously was a tech reporter for Forbes Ukraine. Her work has also been published at Sifted, The Kyiv Independent and The Kyiv Post.

