Hackers target bank clients in Czechia, Hungary and Georgia in novel phishing campaign
Hackers set up malicious banking applications that were nearly identical to legitimate European ones in an effort to steal user data in an elaborate phishing scheme, according to new research.
These malicious apps were installed on Android and iOS devices from third-party websites, bypassing traditional security measures that warn users about the installation of unknown programs, according to a new report from Slovakia-based cybersecurity firm ESET.
The campaign, which began in November last year, was carried out by two threat actors who used “drastically different” infrastructures. However, researchers have not attributed the attacks to specific hacker groups.
Among the known victims of these attacks were a prominent Czech bank, which was not named in the report, as well as the Hungarian OTP Bank and the Georgian TBC Bank.
To gain access to victims' devices, the hackers targeted them with automated voice calls, SMS messages and social media advertisements, tricking users into installing malicious banking apps. To appear more credible, the hackers even created a high-quality phishing page that imitated the official Google Play Store, although the apps were never available on the actual store.
The apps installed on the targeted devices were identified as progressive web applications (PWAs), which behave like real mobile apps and allow threat actors to access the microphone, geolocation, camera and other supported browser functions.
“PWAs are essentially websites bundled into what feels like a standalone application,” the researchers explained. The apps targeted both Android and iOS users and were not recognized as “potentially harmful” by the operating systems, they said.Images
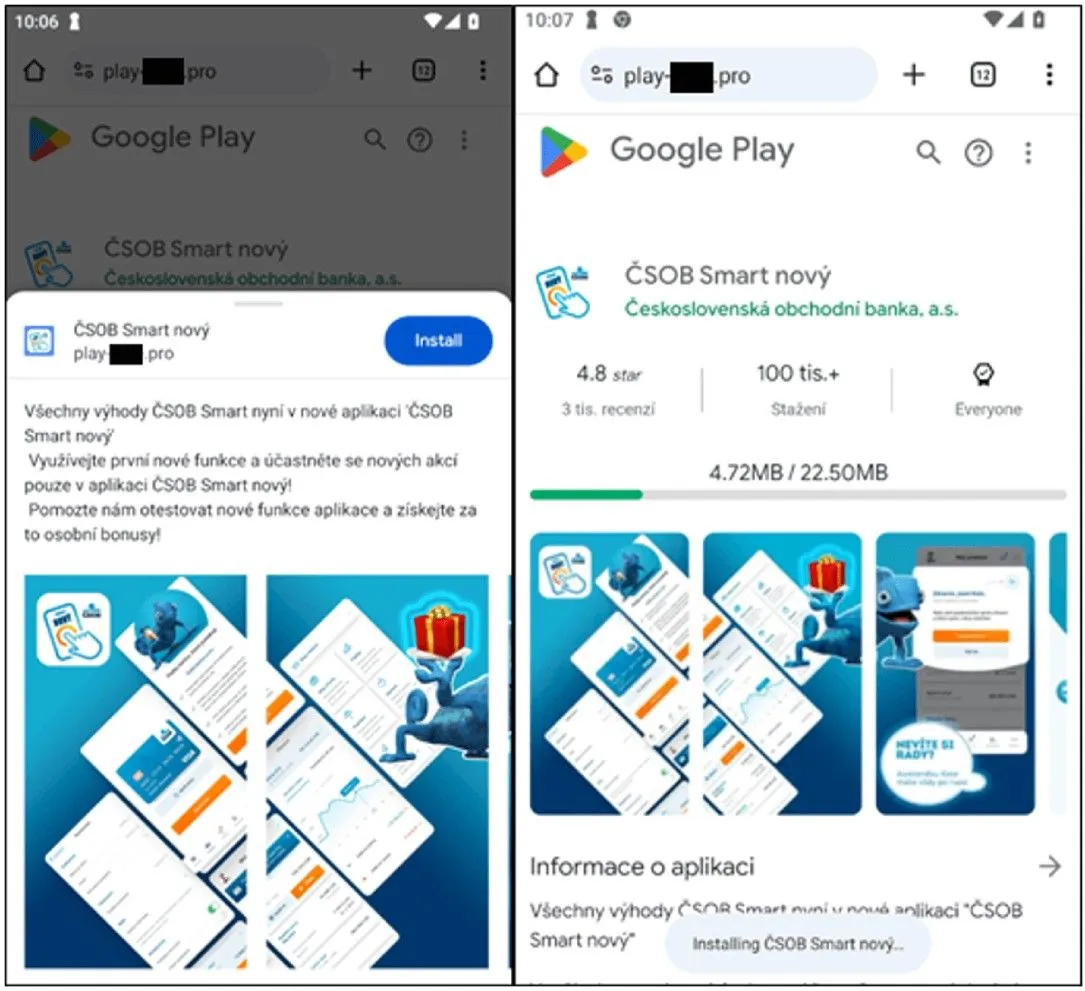
The installation prompt imitated Google Play animations. Image: ESET
The phishing websites targeting iOS users instructed victims to add a PWA to their home screens, while on Android devices, the malicious app was installed after users confirmed custom pop-ups in the browser.
After installation, victims were prompted to submit their internet banking credentials to access their accounts via the new mobile banking apps, which were almost “indistinguishable” from the legitimate apps they mimicked. All submitted information was sent to the attackers' servers.
According to ESET, all sensitive information uncovered during the research was directed to the affected banks for processing. The researchers also claimed to have negotiated the takedowns of multiple phishing domains and hacker-controlled servers.
A similar PWA campaign was discovered in Poland last July, when hackers attempted to trick users into installing a copycat of a Polish bank’s app without having to use the Google Play Store.
“We expect more copycat applications to be created and distributed, as it is difficult to distinguish legitimate apps from phishing ones after installation,” ESET said.
Daryna Antoniuk
is a reporter for Recorded Future News based in Ukraine. She writes about cybersecurity startups, cyberattacks in Eastern Europe and the state of the cyberwar between Ukraine and Russia. She previously was a tech reporter for Forbes Ukraine. Her work has also been published at Sifted, The Kyiv Independent and The Kyiv Post.



