Hackers stole Puma source code, no customer data, company says
Hackers have stolen information from sportswear maker Puma and are currently trying to extort the German company into paying a ransom demand, threatening to release the stolen files on a dark web portal specialized in the leaking and selling of stolen information.
The entry advertising the Puma data was added on the site more than two weeks ago, at the end of August, The Record has learned.
"It was a PUMA source code for an internal application, which was leaked," Robert-Jan Bartunek, head for Puma's corporate communications, told The Record last week.
"No consumer or employee data was affected," Bartunek added.

The hackers claim to be in possession of more than 1 GB of Puma data.
To prove their claims, the threat actors leaked some sample files, which, based on their structure, suggest the attackers might have been obtained Puma's data from a Git source code repository.
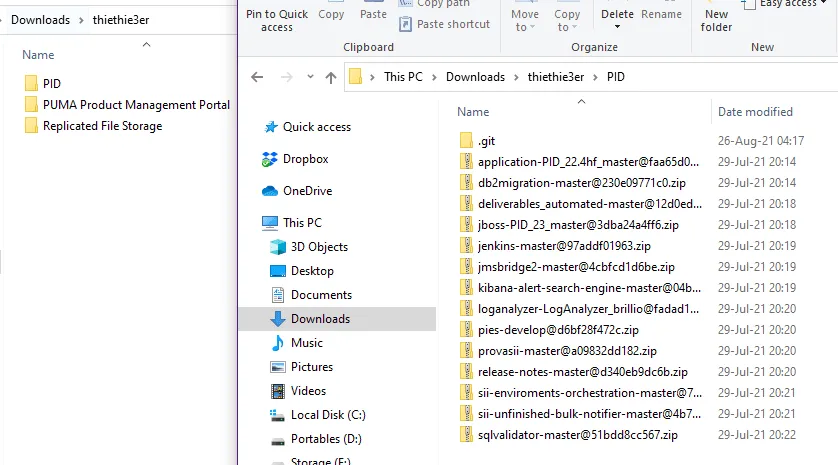
The data is currently listed on a dark web portal named Marketo. Launched in April this year, the site operates in a simplistic fashion.
At first, site administrators list upcoming victims and then add some sort of proof (usually a small downloadable archive) that they breached their network.
If the victimized company does not cooperate with the hackers, their data is leaked on the site, either as a free download or for exclusive VIP members.
The site claims to list data provided by multiple hacking groups and that it does not work with ransomware gangs.
"Right now, I can say that Puma haven't contacted us yet," the administrator of the dark web leak portal told The Record in a conversation last week.
"The rest of the data would be released if Puma will decline the negotiations," they added.
Other names listed on the site currently include the likes of Siemens Gamesa, Kawasaki, Fujitsu, and more than 20 others. In a statement to ZDNet's Jonathan Greig, Fujitsu said last week that the data listed on Marketo was not connected to a cyberattack on its network, suggesting it might have been obtained from a third party.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.


