Hackers exploiting vulnerability affecting Zoho ManageEngine products: Rapid7
Researchers at cybersecurity firm Rapid7 have observed exploitation of a vulnerability affecting two dozen ManageEngine products from software company Zoho.
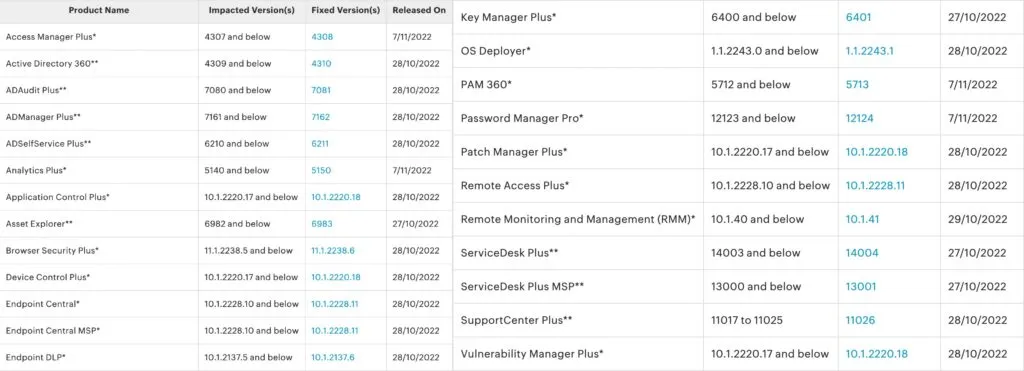
The bug – CVE-2022-47966 – was patched in waves starting on October 27, with the last product receiving a patch on November 7.
Discovered by a researcher from Viettel Cyber Security, the vulnerability allows an unauthenticated adversary to execute code on a system.
On Thursday, experts from the Horizon3.ai Attack Team published a proof of concept and said it was “low in complexity and easy to exploit.” Horizon3.ai initially said it had not seen exploitation of the bug in the wild based on data from cybersecurity company GreyNoise.
Our technical deep-dive of the recent #ManageEngine Pre-Auth RCE CVE-2022-47966.
— Horizon3 Attack Team (@Horizon3Attack) January 19, 2023
POC exploit included for xmlsec <= 1.4.1. Other versions also exploitable.https://t.co/mcStCEws6h
But on Thursday afternoon Rapid7 published its own blog post saying it was responding to “various compromises arising from the exploitation of CVE-2022-47966.”
“Organizations using any of the affected products listed in ManageEngine’s advisory should update immediately and review unpatched systems for signs of compromise, as exploit code is publicly available and exploitation has already begun,” the researchers said, adding that they saw exploitation as early as January 18.
The ManageEngine IT service management solutions suite is used by hundreds of organizations – including nine of every 10 Fortune 100 organizations – for IT infrastructure, networks, servers, applications, endpoints and more.
The exploit only works if Security Assertion Markup Language (SAML) single-sign-on has been previously enabled.
Horizon3.ai said organizations that use SAML tend to be larger and more mature, and are likely to be higher value targets for attackers.
“Its primary role in online security is enabling access to multiple web applications using a single set of login credentials,” Horizon3.ai researchers said.
Eric Fredrickson, head of attack engineering at Horizon3.ai, said data from Shodan shows that there are likely more than 1,000 instances of ManageEngine products exposed to the internet with SAML currently enabled.
“Looking just at the ServerDesk Plus and Endpoint Central products, the Horizon3.ai Attack Team found: 5,255 exposed instances of ServiceDesk Plus, of which 509 have SAML enabled, and 3,105 exposed instances of Endpoint Central, of which 345 have SAML enabled,” Fredrickson said.
“In a worst case scenario, an attacker would gain complete control of the system running the vulnerable ManageEngine project. From there, an attacker can pivot to other machines in the network, dump credentials, and deploy malware/ransomware.”
Horizon3.ai exploit developer James Horseman added that the bug is a result of using an outdated version of Apache Santuario – a tool used for security.
There have been several Zoho ManageEngine vulnerabilities exploited over the last two years.
The Red Cross was hacked through CVE-2021-40539 and a state-sponsored group used the same bug to target the Port of Houston. The German government also warned last year of Chinese state-sponsored groups using the bug to target businesses in the country.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



