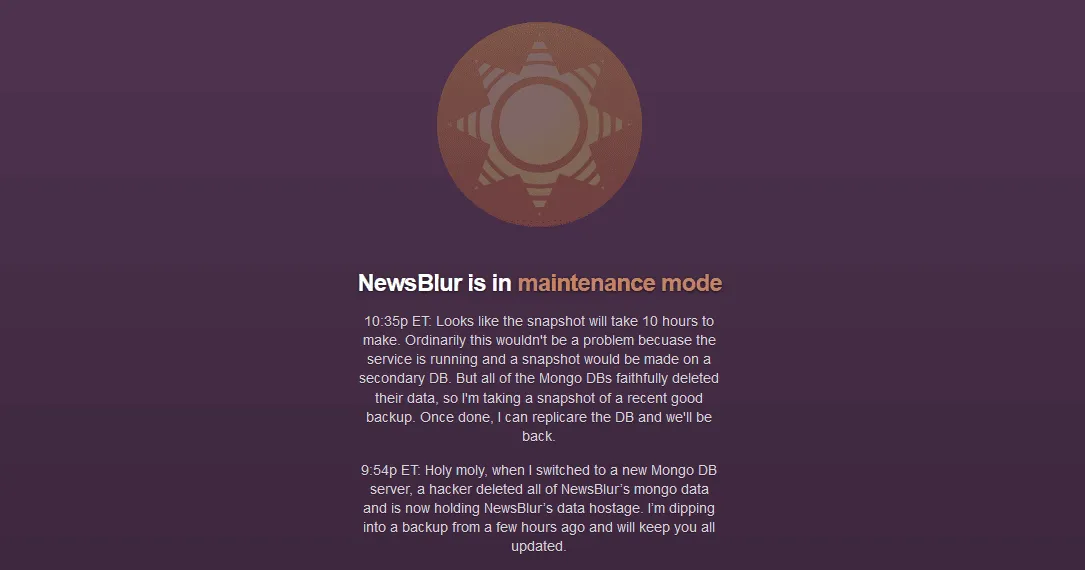
Hacker wipes database of NewsBlur RSS reader
A hacker has wiped the database of NewsBlur, a popular web-based RSS reader, and demanded a ransom payment from the company in exchange for access to its original data.
The incident, which took place earlier today, has already been resolved after the NewsBlur staff restored to a previous backup they had on hand by chance.
According to a message the company had on its website homepage, the attack impacted NewsBlur's MongoDB servers, which were one of five database technologies the company was using for its service.
Firewall bug exposed database online
NewsBlur founder Samuel Clay blamed the attack and database wipe on a firewall bug that occurred during a planned database migration.
"About two hours before [the attack] happened, I switched the MongoDB cluster over to the new servers," Clay said in a HackerNews thread.
"Turns out the ufw firewall I enabled and diligently kept on a strict allowlist with only my internal servers didn't work on a new server because of Docker," he added.
"When I containerized MongoDB, Docker helpfully inserted an allow rule into iptables, opening up MongoDB to the world."
"So while my firewall was 'active,' doing a `sudo iptables -L | grep 27017` showed that MongoDB was open the world."
Clay believes this allowed the hacker to gain access to the server, wipe its content, and leave a ransom note behind.
The NewsBlur founder said it took the attacker only three hours to find the MongoDB database once it was accidentally exposed online.
Clay said NewsBlur was able to recover from the attack because they still had a copy of the original MongoDB database that they were trying to replace during the current migration process.
Old "MongoDB apocalypse" attacks strike again
The attack appears to have been automated and part of a trend that started back in late 2016, when multiple threat actors began wiping MongoDB servers and asking for ransoms from server owners who left their MongoDB instances exposed online without a password.
While threat actors claimed they made copies of the deleted data, in most cases, they were bluffing, hoping to trick victims into paying small ransom demands that usually ranged from $200 to $2,000.
These attacks have continued through the years and are still active today, although at a much smaller scale than the initial 2016-2017 attacks.
According to internet scans performed by the Shadowserver Foundation, there are almost 80,000 MongoDB servers accessible online, with more than 16,000 accessible without a password.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.