Hacker selling access to 50 vulnerable networks through Atlassian vulnerability
A hacker is selling access to 50 vulnerable networks on a cybercriminal forum after breaking into systems through the recently-discovered Atlassian Confluence zero-day.
The Rapid7 Threat Intelligence team told The Record that it found an access broker on the Russian-language forum XSS selling root access to 50 vulnerable networks – all allegedly within the United States.
Erick Galinkin, principal AI Researcher at Rapid7, said the access was gained through CVE-2022-26134, a widely-discussed unauthenticated remote code execution vulnerability. A patch for the bug was released earlier this month after the zero-day was discovered in May.
Galinkin explained that Rapid7 has seen an uptick in patching but noted that the sale underscores the critical need to patch and protect internet-facing servers specifically.
He shared a screenshot of the XSS post, which had the listed company names redacted.
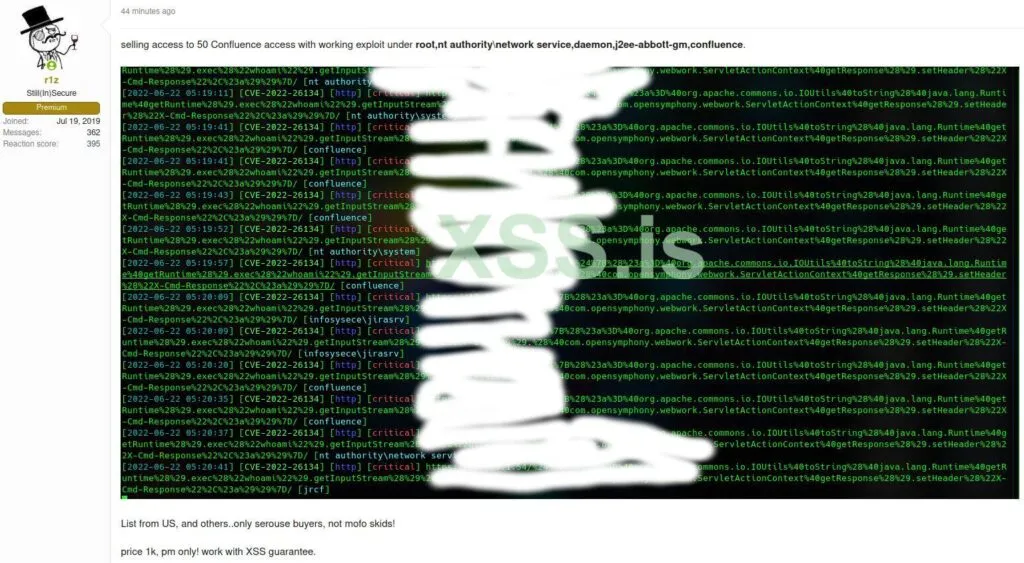
The broker selling access to the 50 networks also claims to have a list of 10,000 additional vulnerable but unexploited machines that they are also willing to sell.
“Our telemetry suggests that the 10,000 number is high, but the seller has a good reputation on the forum and so we are inclined to believe their claims,” Galinkin said.
“Organizations should also analyze their environment to determine if there was an earlier compromise."
Galinkin and other analysts at Rapid7 are working to identify and notify the 50 companies directly.
He recommended that companies put their Confluence servers behind a VPN as soon as possible to limit exposure and to patch the Confluence bug as soon as possible. Organizations should also look for signs that a successful compromise has already occurred.
“The thing that has made this particularly attractive as a target is that the affected application is often internet-facing, since it is used by employees across a company, and sometimes needs to be accessible to contractors and external partners. Ideally, it should be protected at least behind a VPN,” Galinkin explained.
“I definitely anticipate forum posts like this to be used by ransomware groups, and there is good reason to believe ransomware groups are already using access brokers for significant numbers of these types of attacks. Nation state actors may use these access brokers, but it's harder to assess that with any meaningful level of confidence.”
Last week, Microsoft said ransomware groups and nation-state actors have already begun exploiting the vulnerability and some Atlassian users have come forward to say they were attacked.
Multiple adversaries and nation-state actors, including DEV-0401 and DEV-0234, are taking advantage of the Atlassian Confluence RCE vulnerability CVE-2022-26134. We urge customers to upgrade to the latest version or apply recommended mitigations: https://t.co/C3CykQgrOJ
— Microsoft Security Intelligence (@MsftSecIntel) June 11, 2022
At least one victim took to Twitter to note that they were hit with the Cerber2021 ransomware through the Atlassian bug.
The company that discovered the vulnerability, Volexity, said it has also seen state-backed hackers in China exploiting it.
Censys researchers said they found around 9,325 services across 8,347 distinct hosts running some version of Atlassian Confluence earlier this month.
“Of those services, most Confluence versions we identified were v7.13.0 (1,137 hosts), v7.13.2 (690 hosts), and v7.13.5 (429 hosts); and if the advisory is accurate, all of these versions are susceptible to this new attack,” said Mark Ellzey, senior security researcher at Censys.
The Censys dashboard shows most instances are in the U.S., China and Germany, with each country having at least 1,000 vulnerable hosts.
Barracuda researcher Tushar Richabadas reported a large number of attempts to exploit the bug this week, with notable spikes around June 13.
"The exploit attempts range from benign reconnaissance to some relatively complex attempts to infect systems with DDoS botnet malware and cryptominers," Richabadas said.
"Exploitation attempts primarily originated from IP addresses in Russia, followed by the U.S., India, Netherlands, and Germany. As seen in previous research, the attacks seen originating from U.S. IP addresses are primarily from cloud providers. Similarly, for Germany, most attacks were from hosting providers."

Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



