Google's Project Zero updates vulnerability disclosure rules to add patch cushion
The Google Project Zero security team has updated its vulnerability disclosure guidelines today to add a cushion of 30 days to some security bug disclosures, so end-users have enough time to patch software and prevent attackers from weaponizing bugs.
Today's changes are of particular importance because a large part of the cybersecurity community has adopted Project Zero's rules as the unofficial methodology for disclosing a security bug to software vendors and then to the general public.
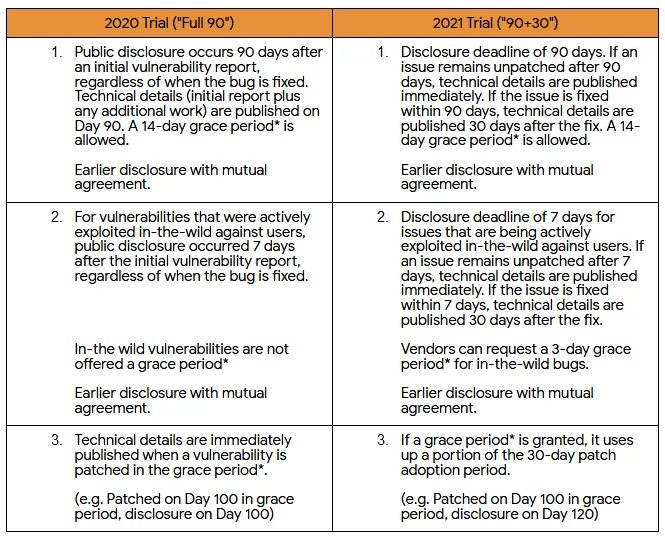
Prior to today, Google Project Zero researchers would give software vendors 90 days to fix a security bug. When the bug was patched, or at the end of the 90 days time window, Google researchers would publish details about the bug online (on their bug tracker).
Starting today, Project Zero says it will wait 30 days before publishing any details about the bug.
The reasoning behind the extra time window is to allow users of the affected products time to update their software, an operation that can usually take days or weeks in some complex corporate networks.
The goal of our 2021 policy update is to make the patch adoption timeline an explicit part of our vulnerability disclosure policy. Vendors will now have 90 days for patch development, and an additional 30 days for patch adoption.
Tim Willis, Project Zero
Project Zero team lead Tim Willis said companies had complained in the past about the lack of a cushion for users to apply the patches.
Past bug details published by Project Zero researchers would usually include in-depth technical explanations of how vulnerabilities worked and would often also include proof-of-concept code. Albeit the demo exploit code was nerfed, it often also provide a basic wireframe for building more advanced exploits.
Ironically, while Project Zero wasn't providing time cushions for other companies, the Chrome team was using one and would never publish details about its security fixes for this very same reason — to prevent attackers from weaponizing fixed Chrome bugs and attack users who had yet to update their browser.
The 30-day cushion also applies to zero-day disclosures
In addition, Willis said the 30-day time cushion would also apply for zero-day vulnerabilities and not just regular bugs. Previously, Project Zero would give companies seven calendar days to patch any actively exploited vulnerability (a zero-day) before they would publish details about the bug online.
Starting 2021, Willis said Project Zero researchers would apply the same 30-day cushion for zero-days and would even be willing to add another three days to the original seven-day disclosure deadline to give companies more time to create a patch, in some rare circumstances.
Plans for next year's disclosure rules updates include modifying the disclosure windows from 90+30 days to something like 84+28, time periods divisible by seven, so disclosure deadlines won't accidentally fall on weekends — when IT staff aren't usually ready to deploy emergency security patches to internal networks.
Willis said that today's changes are most likely to anger cyber-security teams and network defenders who relied on the Project Zero bug details to create detection rules for possible exploitation attempts. Wilis recommended that security firms and other defenders reach out to affected vendors for "actionable technical details."
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



