Google unmasks two-year-old phishing & malware campaign targeting YouTube users
Almost two years after a wave of complaints flooded Google's support forums about YouTube accounts getting hijacked even if users had two-factor authentication enabled, Google's security team has finally tracked down the root cause of these attacks.
In a report published today, the Google Threat Analysis Group (TAG) attributed these incidents to "a group of hackers recruited in a Russian-speaking forum."
TAG said the hackers operated by reaching out to victims via email with various types of business opportunities.
YouTubers were typically lured with potential sponsorship deals. Victims were asked to install and test various applications and then publish a review.
Apps typically used in these schemes involved antivirus software, VPN clients, music players, photo editors, PC optimizers, or online games.
But unbeknownst to the targets, the hackers hid malware inside the apps. Once the YouTube creators received and installed the demo app, the installer would drop malware on their devices, malware which would extract login credentials and authentication cookies from their browsers and send the stolen data to a remote server.
The hackers would then use the authentication cookies to access a YouTuber's account —bypassing the need to enter a two-factor authentication (2FA) token— and move to change passwords and the account's recovery email and phone numbers.
With the victims locked out of their accounts, the hackers would typically sell the hijacked YouTube channel on underground marketplaces for stolen identities.
Hacked accounts sold on Trade Groups even to this day
But independently from Google TAG, this reporter has also followed these attacks since November 2019, and after a flood of complaints on Google's support forum [1, 2, 3, 4, 5] suggested that the incident described in the tweet was not an isolated case.
At the time, we tracked the stolen account of MarcoStyle, a US-based gamer, to a Russian website named Trade Groups.
Founded in 2013, the website claims to operate an Amazon-like market where users can register and then sell any of their social media accounts.
But despite the attempt of building a legitimate facade, things were not as they appeared. Besides MarcoStyle's stolen account, the Trade Groups website also hosted several users who were selling hundreds of accounts on a daily basis, a clear sign that they were not the legitimate owners of those profiles.
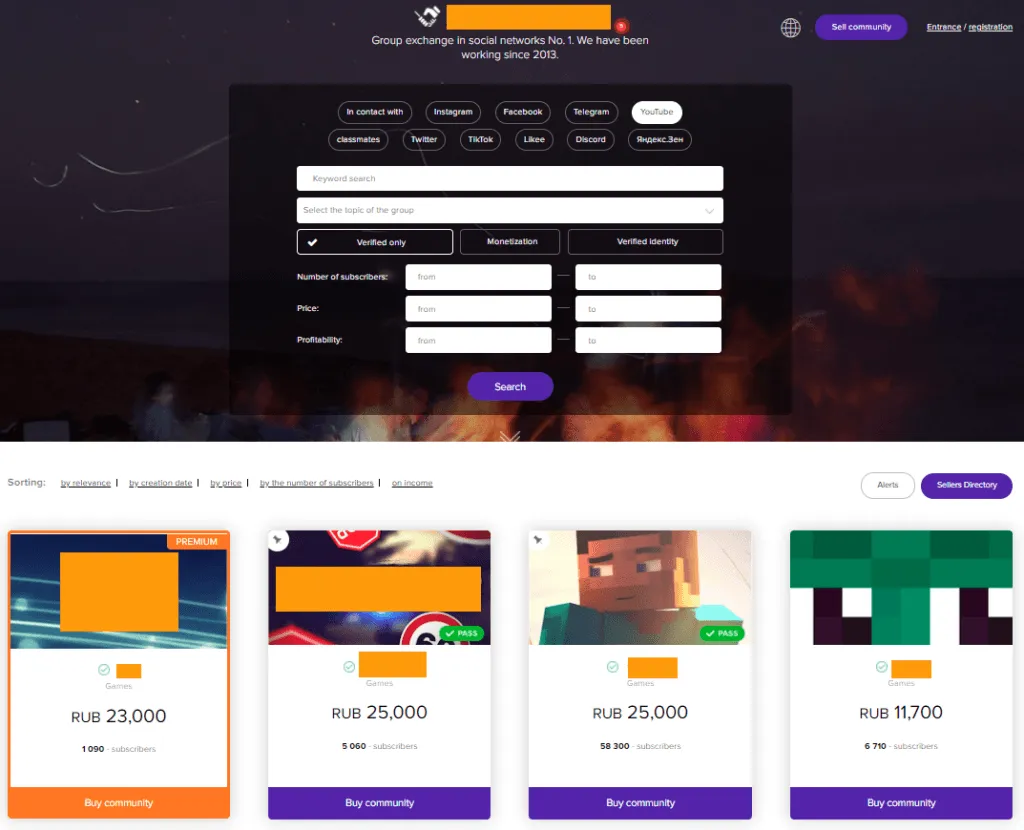
Since November 2019, this reporter has randomly contacted users that had their social media profiles, and especially YouTube and Instagram accounts listed on the site.
In phone and email interviews with more than 20 victims, we heard the exact same scenario described in Google's report today.
For example, MarcoStyle said he was approached with an offer to test and review a new game optimization tool called Orio.
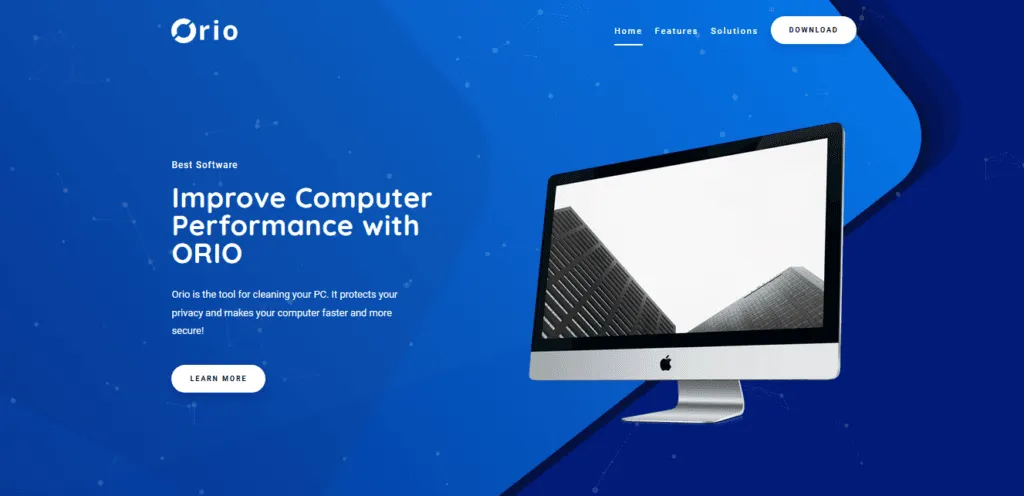
"As soon as I installed it, I knew something was wrong," MarcoStyle said in an interview via Discord in November 2019. "I knew I had 2FA turned on, but still lost access to the account."
"The person who emailed me never replied, then a few days later someone told me the account was for sale online," he added.
In December 2019, a Romanian fashion vlogger who we'll reference only by her initials F.A. went through something similar. She was approached and asked to install an app to connect to an ad agency's backend in preparation for a future collaboration.
Instead, she had her YouTube, Facebook, and Instagram accounts taken from her. F.A. never regained control over her YouTube account, which had amassed roughly 1k followers by that point. Soon after, she dropped her attempts at forging a career as a vlogger, unwilling to start from scratch with a new account.
We also spoke with L.L., a Polish gamer who managed to build a channel of more than 12k followers. We found him via a non-Gmail email address that was still present in his YouTube account's About section that the hackers forgot to remove.
In an email, L.L said he lost control over his account after he received an email from someone posing as a representative for a gaming company.
Days later, his account was on Trade Groups, for sale for only 25,000 rubles (~$350).
The most recent YouTube creator we spoke to was a Russian gamer named San4esGG, which also lost his account as part of this campaign. At the end of August, he still hadn't been able to recover their account despite filing a request with Google.
Most accounts were returned to their original owners
Throughout the past two years, this reporter also attempted to track how these accounts were misused.
Some accounts were permanently rebranded and had new owners, but most of the accounts listed on Trade Groups usually found their way back into their original owner's hands, with some faster than others.
However, it appeared that buyers typically knew what they were getting when buying accounts via Trade Groups —namely, hacked accounts that were bound to be returned to their old owners within days or weeks.
Using YouTube's mobile notification system, we put some of the hacked accounts under surveillance. Quite a few of the accounts we followed were used to host short live streams that peddled cryptocurrency scams —similarly to what Google also found in its own investigation.
"The channel name, profile picture and content were all replaced with cryptocurrency branding to impersonate large tech or cryptocurrency exchange firms. The attacker live-streamed videos promising cryptocurrency giveaways in exchange for an initial contribution," said Ashley Shen, a member of Google TAG.
Scams this reporter has tracked throughout 2020 involved schemes where the accounts were rebranded with the identities of Bill Gales, Elon Musk, or Linus Torvalds, all of which promoted some sort of cryptocurrency Ponzi scheme.
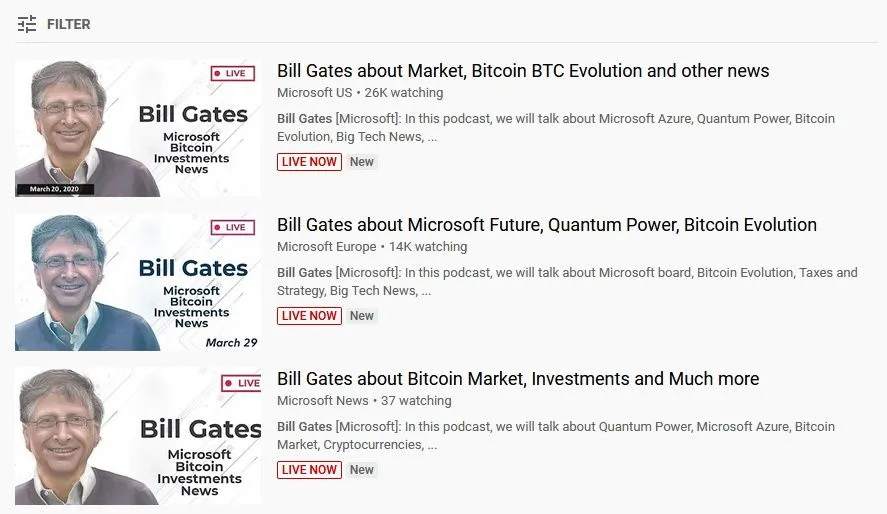
Google: More than 4,000 YouTube creator accounts were hijacked
Today, Google said that it identified more than 15,000 email accounts used by this group to reach out and communicate with victims and 1,011 websites that hosted malware-infected apps.
Some of the websites impersonated legitimate software sites, such as Luminar, Cisco VPN, games on Steam, and some were generated using online templates.
Ashley Shen, Google TAG analyst
Malware typically used by the hackers included an assortment of infostealer strains, such as RedLine, Vidar, Predator The Thief, Nexus stealer, Azorult, Raccoon, Grand Stealer, Vikro Stealer, Masad, and Kantal, all sold on underground hacking forums. Open-source malware, available on GitHub, such as AdamantiumThief and Sorano, was also used in some attacks as well, Shen added.
Shen said that to this date, Google had restored more than 4,000 YouTube creator accounts hacked by this group.
Unfortunately, the Google researcher said that they are also losing visibility into these operations as the threat actors are increasingly moving conversations from emails to third-party instant messaging apps, where Google can't scan, block, or alert victims of any suspicious links.
As for who's behind these attacks, Google said that this matter is for the FBI, which they have also notified.
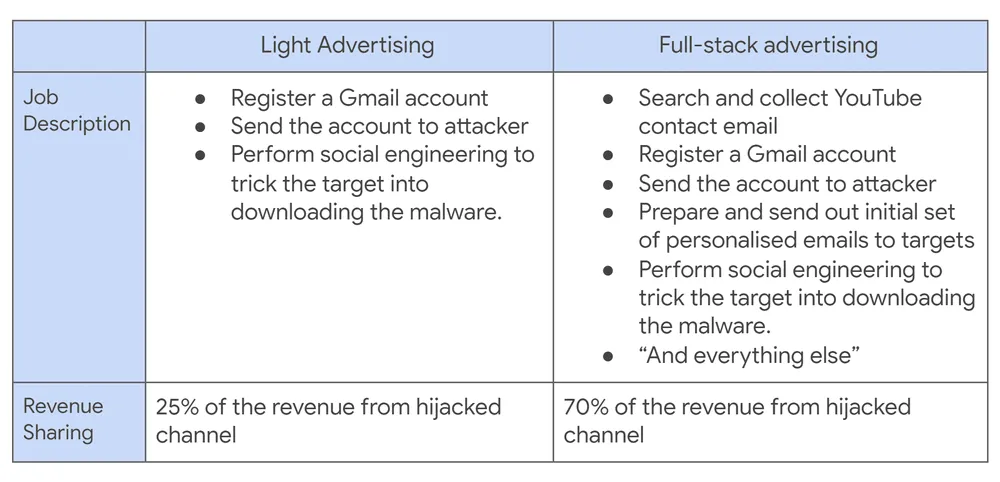
Additionally, Shen said Google also tracked down the forums where the group behind these attacks recruited the partners to perform the phishing and social engineering attacks.
According to a series of ads, partners were offered cuts of either 25% or 75% of the stolen account's re-sale prices depending on their level of involvement and the complexity of the phish. According to prices listed on Trade Groups, accounts sold on the site typically went for prices ranging from $20 to $10,000.
All in all, Google said that it has learned from this campaign and has now improved Gmail's security defenses, lessons it has also integrated into its browser's Safe Browsing system as well.
The administrators of the Trade Groups portal did not return requests for comment sent by this reporter via their website on two occasions.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.


