Google tool for e-commerce sites being abused by hackers stealing card data, personal info
Hackers are abusing Google’s Tag Manager (GTM) containers to install malicious e-skimmers that steal payment card data and personally identifiable information of shoppers on e-commerce sites, according to a new report from Recorded Future.
Thousands of e-commerce sites use Google Tag Manager containers for data on website usage metrics, customer tracking and marketing purposes.
But Recorded Future experts have found three significant variants of malicious scripts that cybercriminals are hiding within GTM containers that allow them to exfiltrate the personal information of shoppers.
“As of this writing, over 165,000 payment card records attributed to victims of GTM container abuse attacks have been posted to dark web carding shops,” the researchers said. “The total number of payment cards compromised via GTM-based e-skimmers is likely higher.” The Record is an editorially independent unit of Recorded Future.
The researchers found 569 e-commerce domains infected with e-skimmers. According to the report, 314 were confirmed to have been infected by a GTM-based e-skimmer variant while 255 had infections that exfiltrated stolen data to malicious domains associated with GTM abuse.
Nearly 90 of these e-commerce domains were still infected as of August 25 and on average, researchers found it took more than three months for the infections to be remediated.
Stas Alforov, director of fraud research at Recorded Future, said that based on dark web chatter, the abuse of GTM goes back as far as 2018 and was used by a variety of cybercriminals.
“We first highlighted the use of GTM in a report in 2021, and it has continued to be in active use to this date, in some cases still using the same malicious GTM buckets made public last year,” Alforov said. “Thus we believe that the use of GTM will remain unchanged unless Google remediates it by implementing active scanning for skimmer payloads inside the GTM-hosted buckets.”
Google did not respond to requests for comment, but in 2016 the company launched automated malware detection for GTM containers to combat abuse. That effort was quickly circumvented by hackers, who evolved their efforts to install cryptojackers, according to The Register.
Cybersecurity firm Sucuri also previously found “rogue” advertisements placed on websites through alleged abuse of GTM containers.
By abusing legitimate tools like GTM, hackers can avoid security software that often does not scan GTM containers because website administrators typically whitelist trusted source domains, especially those coming from Google.
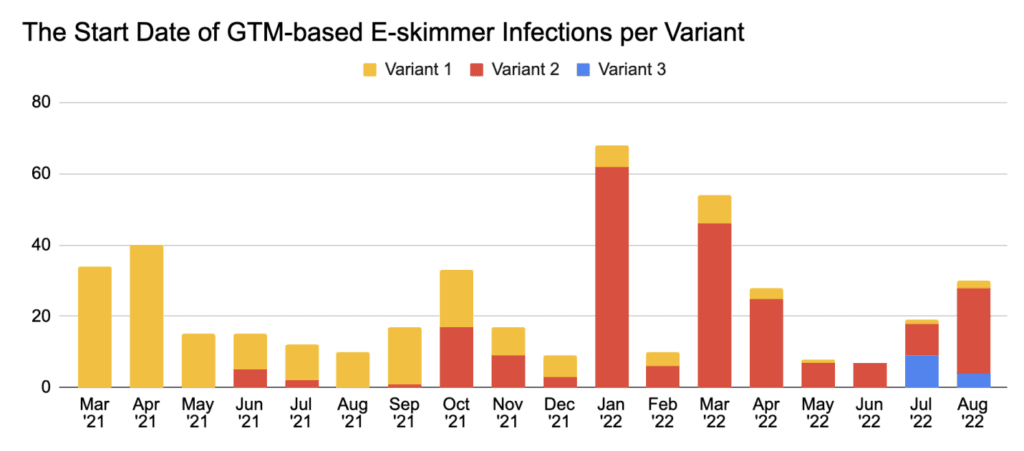
Recorded Future said it began tracking the use of the three GTM-based e-skimmer variants since March 2021 and noted that newly infected e-commerce domains have been observed every month since then.
The first and third variants the researchers found have similarities that suggest they may be used by the same cybercriminals — indicating that hackers are updating their tools to avoid detections.
“All 3 variants use separate e-skimmer scripts and exfiltration domains. All 3 variants are currently in use for active infections and have been deployed to infect new e-commerce domain(s) in August 2022, indicating that all 3 variants pose an active risk to e-commerce websites and their customers — and by extension, to financial institutions and card networks,” the researchers said.
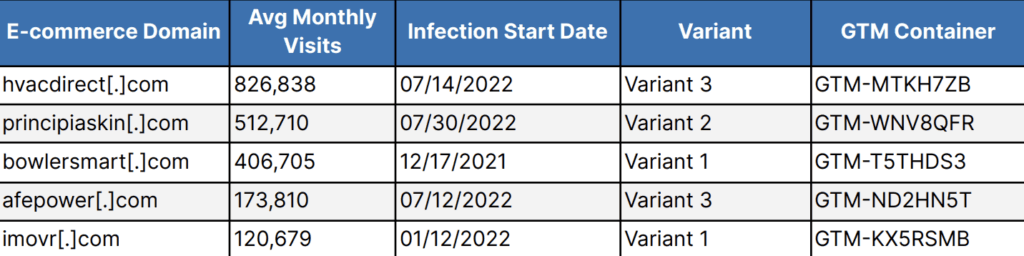
When the researchers examined the attacks, they found that the hackers were not exclusively targeting “high-value” e-commerce domains with more than 1 million monthly visitors. Some of the sites that were abused only saw about 10,000 monthly visitors.
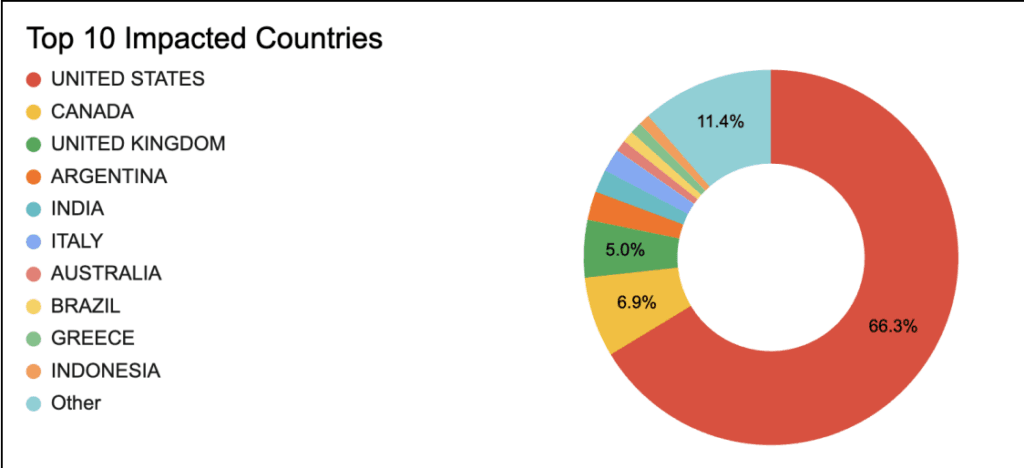
Most of the websites are based in the U.S., which accounted for more than 66% of infections. The rest were based in Canada, the UK, Argentina, India, Italy, Australia, Brazil, Greece, Indonesia and others.
Alforov said it is common for malicious actors to abuse a wide variety of legitimate web services and platforms, citing previous attacks on Google’s analytics service.
“We were surprised to see the abuse of GTM containers given the prior abuse of Google analytics,” Alforov explained. “Additionally, the use of look-alike domains in some of the variants was odd as most large companies employ detection and remediation activities against look-alikes for security and brand protection reasons.”
Recorded Future suggested e-commerce sites perform a full scan of files used within their webpages to catch any unauthorized changes.
According to the researchers, hackers are likely to continue leveraging these publicly available, and often free-to-use, services in an effort to maintain infections.
This kind of abuse also allows hackers to avoid detection and keep their anonymity, the report adds.
“As security tools may be configured to save resources by whitelisting files hosted on ‘trusted’ source domains, this same optimization may be self-defeating for e-commerce websites, leaving websites open to exploitation and persistent infection with malicious files,” the researchers said.
“The abuse of GTM containers also enables threat actors to update Magecart campaign infrastructure and software without the need to access the victim server.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



