Google shuts down malicious ad posing as Brave browser but delivering malware
Internet surfers looking to download a copy of the Brave browser were fooled this week by a cleverly disguised ad that redirected them to a malicious website where they infected their systems with malware.
The malicious website was located at bravė.com, where Brave was spelled with a Lithuanian small caps ė (with a dot on top) instead of the normal Latin alphabet e.
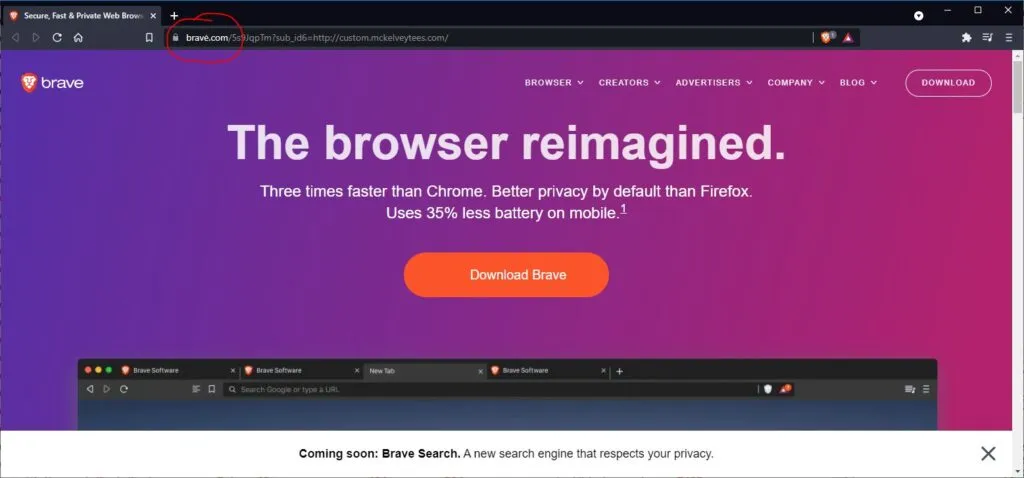
Users who landed on the site, which was designed to look like the legitimate Brave portal, downloaded an ISO file claiming to contain the Brave installer.
However, besides installing a copy of the Brave browser, the ISO file also installed a version of the ArechClient (SectopRAT) malware, security researcher Bart Blaze told The Record today, after analyzing the malicious file.
The malware's primary functionality is to steal data from browsers and crypto-wallets, Blaze said.
It also contained several anti-VM and anti-emulator detection capabilities to prevent researchers and security solutions from detecting its malicious capabilities.
Users who installed this malware are advised to reset web account passwords and transfer cryptocurrency funds to new addresses.
Contacted by email, Google said it has now taken down the malicious ad.
We have robust policies prohibiting ads that attempt to circumvent our enforcement by disguising the advertiser's identity and impersonating other brands. In this case, we immediately removed the ad and suspended the advertiser account.
Google spokesperson
Furthermore, after news of the attack spread online this week, Namecheap, the domain registrar used by the attackers, took down the domain, and others from the same threat actor that impersonated the Tor and Signal websites.
since this is getting some attention today, just want to add that Namecheap promptly took down the abusive domains (for Brave, Tor, Signal, etc.) and Google blocked their ads not long after these tweets went out.
— yan (@bcrypt) July 30, 2021
thanks twitterverse for keeping people safe :)
These types of attacks are called IDN homograph attacks and happen when threat actors register domains using international characters that resemble the classic Latin alphabet.
Attacks like the one aimed against Brave users have been happening for more than a decade since internationalized glyphs were approved for use in domain names, and browser makers have responded by spelling these non-standard characters using Punycode.
For example, the malicious bravė.com domain would equate to xn--brav-epa.com when loaded inside a modern browser, but if users didn't pay attention to the address bar, they would have most likely downloaded the malicious payload.
According to Google's annual Ads Safety Report, the company saw 968 million ads last year that used various techniques to cloak their intentions to attack users and bypass Google's advertising policies.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



