Google says Rowhammer attacks are gaining range as RAM is getting smaller
A team of Google security researchers said they discovered a new way to perform Rowhammer attacks against computer memory (RAM) cards that broaden the attack's initial impact.
First detailed in 2014, Rowhammer was a ground-breaking attack that exploited the design of modern RAM cards, where memory cells are stored in grid-like arrangements.
The basic principle behind Rowhammer was that a malicious app could perform rapid read/write operations on a row of memory cells. As the cells would shift their values from 0 to 1 and vice versa in a very small time window, this would generate small electromagnetic fields inside the row of "hammered" memory cells.
The result of these fields were errors in nearby memory rows that sometimes flipped bits and altered adjacent data.
In the initial 2014 Rowhammer paper [PDF], researchers showed how they could abuse "row hammering" to control these electromagnetic fields and the way that data was manipulated.
Initial Rowhammer attacks targeted RAM DDR3 memory cards, but academics kept researching the topic. In the following years, they also discovered that Rowhammer attacks could also impact RAM DDR4, that attacks could be executed via JavaScript code loaded on a web page, or even via network packets sent directly to a computer's networking card.
Furthermore, researchers also found that Rowhammer attacks could also be used to exfiltrate data from the RAM (not only alter it) and that attacks could also be accelerated by using locally installed GPU or FPGA cards.
Hardware vendors responded to these attacks by deploying a set of mitigations collectively known as Target Row Refresh (TRR). When enabled on a RAM card, TRR would combine a set of hardware and software improvements to detect and diminish the effects of row-hammering attacks.
These mitigations were not perfect, and academics showed last year that a new variation of the initial Rowhammer attack named TRRespass could bypass TRR even on the latest generation of RAM cards.
Meet Half-Double, a new Rowhammer attack variation
But in a research paper published today, a team of five Google security researchers took Rowhammer attacks to a new level.
In a new attack variation named Half-Double, researchers said they managed to carry out a Rowhammer attack that caused bit flips at a distance of two rows from the "hammered" row instead of just one.
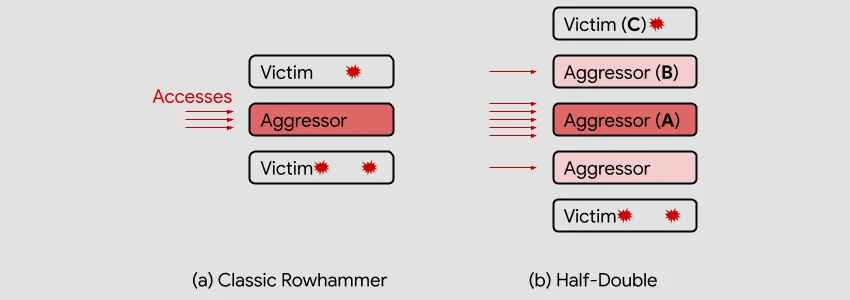
Unlike TRRespass, which exploits the blind spots of manufacturer-dependent defenses, Half-Double is an intrinsic property of the underlying silicon substrate. This is likely an indication that the electrical coupling responsible for Rowhammer is a property of distance, effectively becoming stronger and longer-ranged as cell geometries shrink down. Distances greater than two are conceivable.
Google
In other words, the Google team is saying that while RAM cards become smaller in recent years, the distance between memory rows was also decreased, allowing the electromagnetic field caused by Rowhammer to reach more memory cells than in the original 2014 attack.
To put this into perspective, the main threat from Half-Double attacks primarily comes from the fact that TRR protections were designed to protect nearby memory cells and not cells at a two-row distance—meaning that Half-Double now joins TRRespass as the second Rowhammer variation that can bypass TRR.
But while there are no known cases where Rowhammer attacks have been used in the real world, Google's discovery is monumental, at least from an academic standpoint.
It confirms once again that TRR is not enough to protect from Rowhammer exploits.
In a blog post today, Google said that it is currently working with several semiconductor industry players to search "possible solutions for the Rowhammer phenomenon," and encouraged fellow experts to join their efforts, as "the challenge is substantial and the ramifications are industry-wide."
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.