Google: North Korean hackers are still targeting security researchers
The North Korean government-backed hackers who spent last year trying to lure security professionals to malicious sites to infect their systems with malware have returned with new attacks.
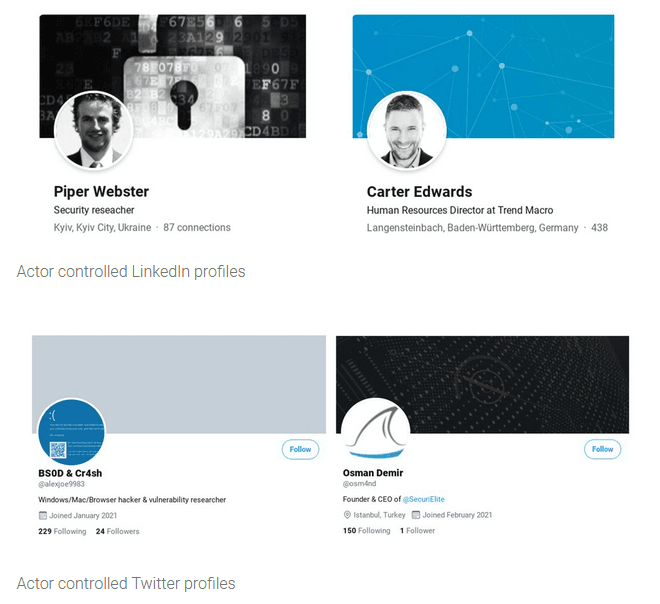
Google's Threat Analysis Group, which detected and disclosed the first set of attacks in February, said today they've identified a website for a fake security company, along with Twitter and LinkedIn accounts, that were created by the same group.
Google says the North Korean hackers were planning to use these social media accounts to lure security researchers on the fake security company's website, where they would have most likely used browser exploits to plant malware on the researcher's computers.
But while the first wave of attacks involved the use of a Google Chrome, Internet Explorer, and Windows 10 zero-day, Google said that this new site was not yet loaded with any malicious code, suggesting Google caught the operation in its planning phase before any zero-day exploits were uploaded on the site.
As for the site itself, Google said the North Korean group tried to pose as "an offensive security company located in Turkey that offers pentests, software security assessments and exploits."
Named SecuriElite, Google was able to link this company to the previous campaign due to the use of a public PGP key they also used in the first attacks.
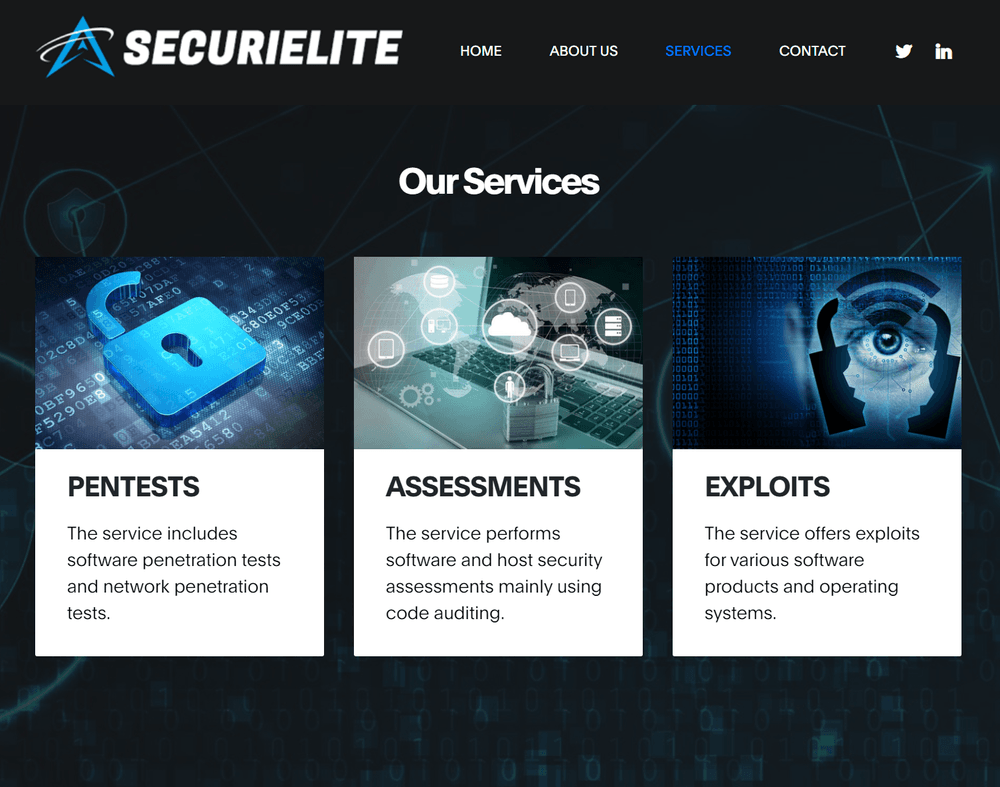
Even if the SecuriElite site was not malicious at the time of its discovery, Google said it added its URL (securielite[.]com) to the Safe Browsing API to prevent users from easily accessing the site, even accidentally.
Furthermore, Google's TAG team also said they reported the attacker's social media accounts to both Twitter and LinkedIn, which have now suspended the profiles.
While we may never be sure of the reasons and motivations behind these attacks, there are several theories why North Korean government-backed actors might invest this much effort into such a campaign.
The first theory is that North Korean hackers may be attempting to get a foothold on systems managed by security researchers in order to gain access to zero-day research before vulnerabilities are publicly disclosed and patched.
The second theory is that the attackers may want to gain a foothold on the networks of security firms, from where they could collect data on the victim's customers and the weaknesses in their networks.
Either way, the attacks have shaken up the infosec community, which is used to hunting threat groups, and not getting attacked.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



