Google: North Korean gov’t hackers used Internet Explorer zero-day to target South Korea users
Internet Explorer users in South Korea were targeted by a group of North Korean government hackers using a zero-day vulnerability in late October, according to a new report.
In a report on Wednesday from Google’s Threat Analysis Group (TAG), researchers said they notified Microsoft about CVE-2022-41128 and the issue was patched “within a few hours.”
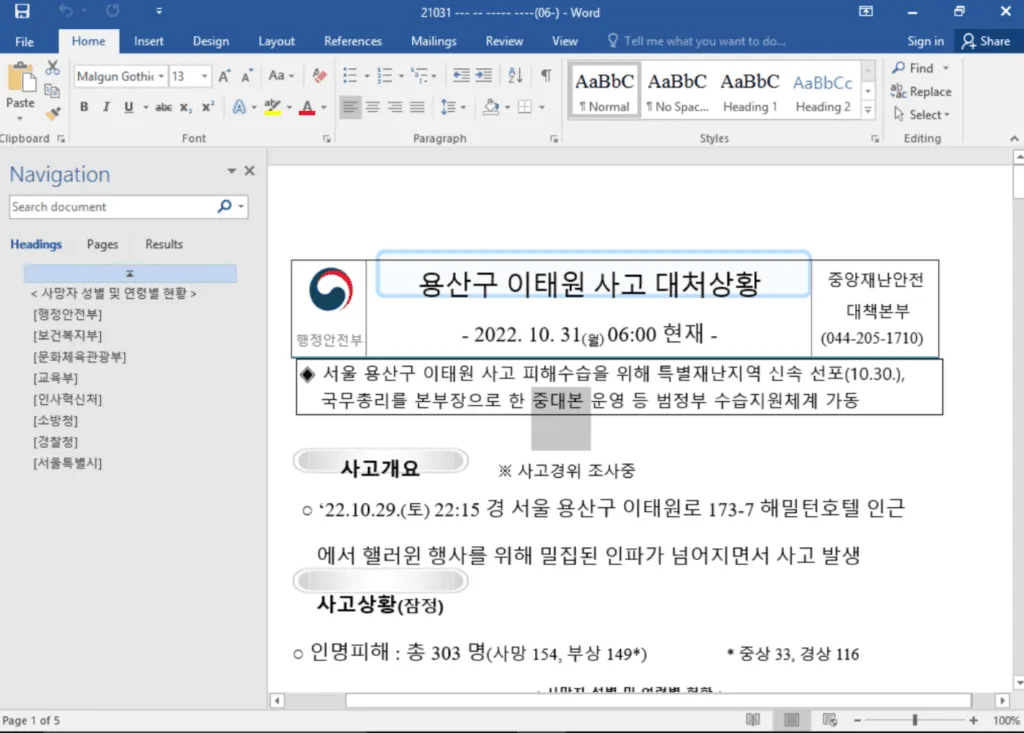
The hackers – from North Korean group APT37 – used documents referencing the tragic incident in Itaewon, in Seoul, South Korea during Halloween to exploit the vulnerability, which was in Internet Explorer’s JScript engine.
According to a Google report, they were first tipped off about the issue on October 31, when multiple people based in South Korea reported a new malware by uploading malicious documents to VirusTotal. The document’s title references the tragic incident that took place during Halloween celebrations on October 29.
The scheme takes advantage of a long-running feature where Microsoft Office renders HTML content using Internet Explorer. Google said delivering Internet Explorer exploits through this vector has the advantage of not requiring the target to use Internet Explorer as its default browser.
This latest bug takes advantage of the JavaScript engine of Internet Explorer and Google compared it to another issue from 2021. After reporting the problem to Microsoft on Halloween, It was given the CVE-2022-41128 tag on November 3 and was patched by November 8.
“TAG also identified other documents likely exploiting the same vulnerability and with similar targeting, which may be part of the same campaign,” the researchers said.
“TAG is committed to sharing research to raise awareness on bad actors like APT37 within the security community, and for companies and individuals that may be targeted. We’d be remiss if we did not acknowledge the quick response and patching of this vulnerability by the Microsoft team.”
Great research from @Google TAG's @_clem1 and @benoitsevens on N. Korean threat group APT37 exploiting an Internet Explorer 0-day vuln to target N. Korean defectors and human rights activists & S. Korean journalists https://t.co/Zlrh9l4vV1
— Royal Hansen (@royalhansen) December 7, 2022
The final payload used in this campaign was not recovered, but Google said they have seen the same group deploy a variety of malware strains including ROKRAT, BLUELIGHT, and DOLPHIN.
Google noted that this is not the first time APT37 has used Internet Explorer 0-day exploits to target users, explaining that the group typically targets South Koreans, North Korean defectors, policy makers, journalists and human rights activists.
A report last year from Volexity found that the group carried out a watering hole attack on one of the most popular North Korean-themed news sites on the internet and infected some of the site’s visitors with malware.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.

