Google, Mandiant say zero-day numbers reached all-time highs in 2021
Google and Mandiant released reports this week saying the number of disclosed and exploited zero-days reached record highs in 2021.
Mandiant said it identified 80 zero-days exploited in the wild, more than double the record volume they saw in 2019. The term zero-day refers to newly-discovered vulnerabilities in which a vendor has zero days to fix before a hacker can start exploiting it."
Google, which recently bought Mandiant, said it’s Project Zero found 58 in-the-wild zero-days, the most ever recorded since they began tracking the statistic in 2014.
“We believe the large uptick in in-the-wild zero-days in 2021 is due to increased detection and disclosure of these zero-days, rather than simply increased usage of zero-day exploits,” Google explained.
“When we look over these 58 zero-days used in 2021, what we see instead are zero-days that are similar to previous & publicly known vulnerabilities. Only two zero-days stood out as novel: one for the technical sophistication of its exploit and the other for its use of logic bugs to escape the sandbox.”
More than two thirds of the zero-days in 2021 were memory corruption vulnerabilities, which Google called the “standard for attacking software for the last few decades.”
Google tracked zero-days in Chrome, Safari and Internet Explorer as well as Windows, macOS, Android, Microsoft Exchange servers and more.
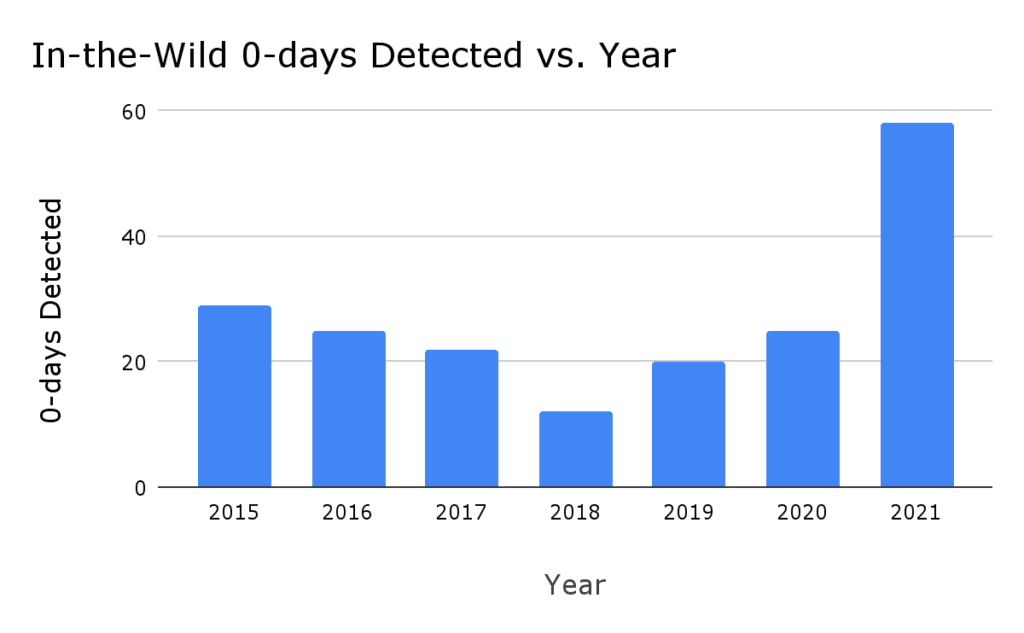
Mandiant’s report found that as the number of zero-days increased, exploitation increased alongside it. Just 32 zero-days were exploited in 2019 compared to the 80 seen last year, according to their data.
They attributed much of the activity to state-sponsored actors exploiting the move toward cloud hosting, mobile, and Internet-of-Things (IoT) technologies.
Financially-motivated actors are increasingly using the zero-days as well, growing to nearly one-third of all identified actors exploiting zero-days in 2021.
“Zero-day exploits and variants of malware that go after them have been on consistent rise as attackers invest in automation and research. Many of the zero-days discovered in old software like print spooler (print nightmare) are being discovered by overseas research teams," said Blue Hexagon CTO Saumitra Das.
"These can then be weaponized at scale and quickly by attackers using mutated malware to get in. In many cases, attacker use an existing foothold and simply try out a new POC at a victim.”
Microsoft, Apple, and Google products comprise about 75% of total zero-day vulnerabilities among the 12 vendors tracked by Mandiant.
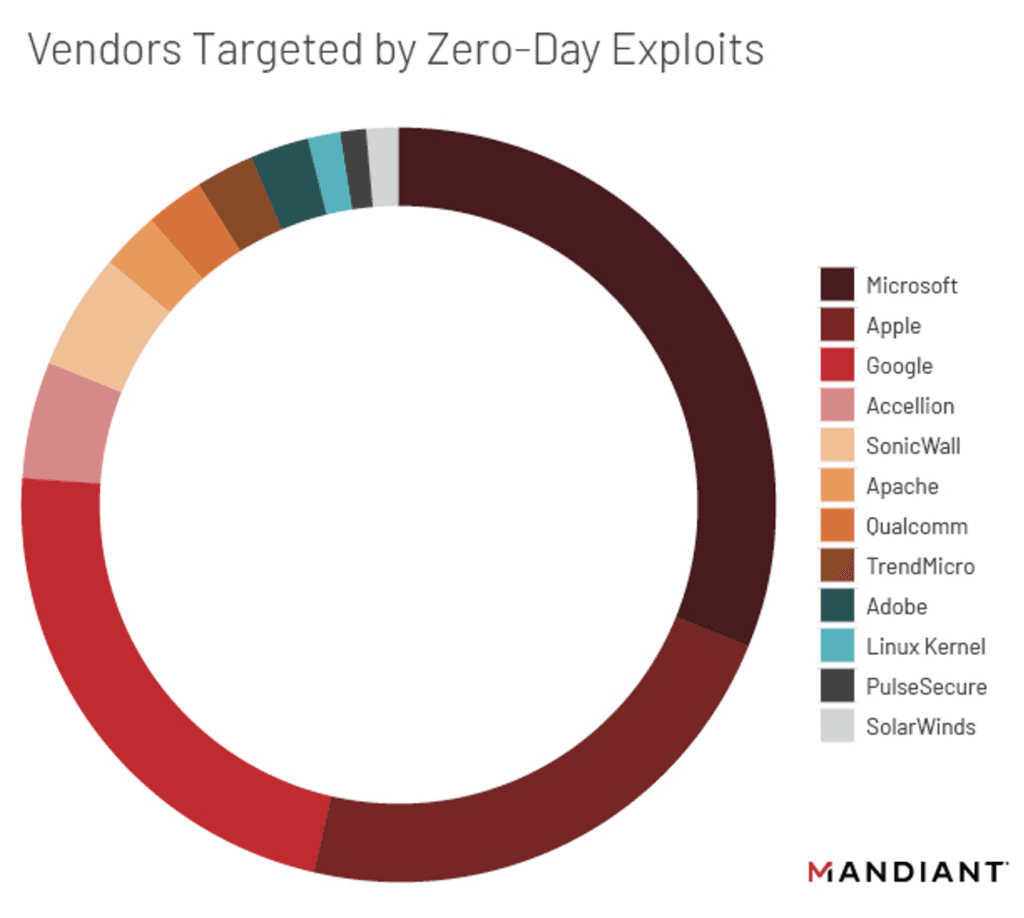
Adobe previously led the way in terms of zero-days because of issues tied to Adobe Flash, but since the tool was retired in 2017, they have dropped out of the top three.
According to Mandiant, there has also been growth in the use of zero-days by ransomware groups.
"We observed at least two instances in which separate threat actors exploited flaws in separate VPN appliances to obtain access to the victim networks and subsequently deploy ransomware in 2021," Mandiant said.
"We suggest that significant campaigns based on zero-day exploitation are increasingly accessible to a wider variety of state-sponsored and financially motivated actors, including as a result of the proliferation of vendors selling exploits and sophisticated ransomware operations potentially developing custom exploits."
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.