Google Docs commenting feature abused in phishing operations
Threat actors are using the commenting feature of Google Docs files to lure users on phishing sites or to download malware-infected files.
In a report today, email security firm Avanan said it has seen the technique being abused in malware distribution campaigns last month, in December 2021.
The technique, first documented in the fall of 2020, is extremely simple to carry out and can be easily automated for mass attacks.
- A threat actor creates a Google Docs file.
- The threat actor adds a malicious link inside the file's comments section.
- The threat actor uses the "@" feature to mention Gmail users.
- All users mentioned via @ will receive an email containing a link to the Google Docs file, but also a preview of the comment section, including the link to the malicious site.
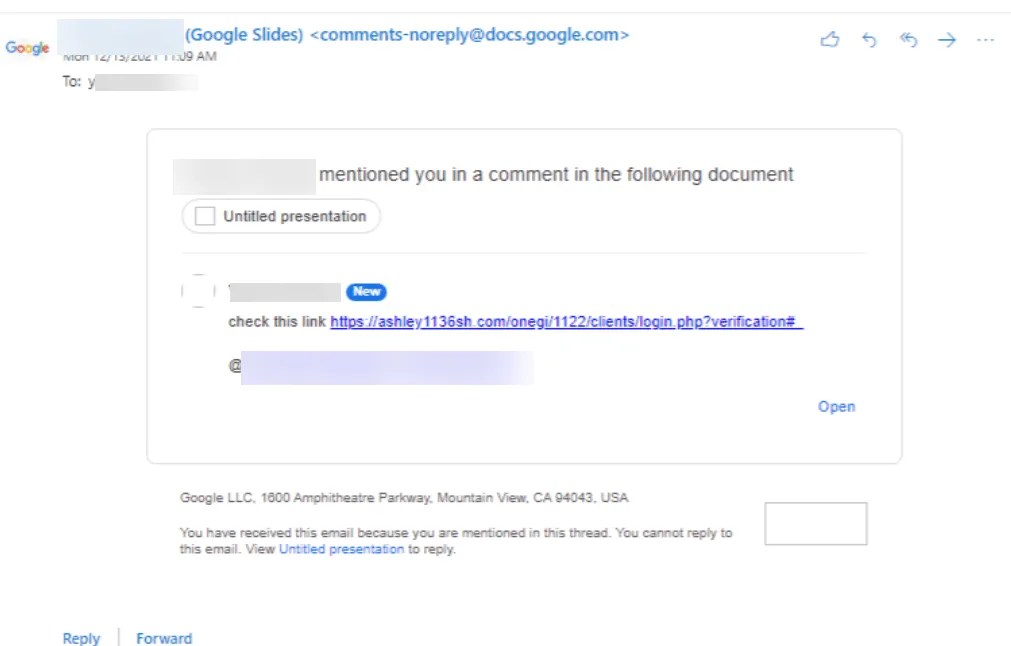
Avanan says the technique is ideal for phishing and malware distribution because the threat actor's email address isn't shown, but just their self-configured name, which could be very easily be set to the name of another person from the same organization.
In addition, all emails come from Google's systems, meaning they can't be stopped without blacklisting Google's email infrastructure.
Avanan said it notified Google of the resurgence of this old technique in new campaigns, for which Google initially rolled out some detections back in 2020.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



