Google disrupts Glupteba botnet, files lawsuit against two Russians
Google has announced today that it has disrupted the operations of the Glupteba botnet and has filed a lawsuit against two Russian nationals it believes have created and helped run the malware for the past few years.
The company said it removed around 63 million Google Docs files used by the Glupteba gang to distribute its malware to unsuspecting victims, along with 1,183 Google accounts, 908 cloud projects, and 870 Google Ads accounts used by the gang to create and host parts of their botnet.
In addition, Google said it has also been working for the past few days with several internet infrastructure companies and web hosting providers, such as Cloudflare, to take down servers used by the gang to control its botnet of infected computers.
Google says disruption is likely temporary
Google said that despite its extensive disruption attempt, its efforts will not cripple the Glupteba botnet for good as the malware was designed with a backup command-and-control (C&C) system that runs on top of the Bitcoin blockchain.
This backup C&C system still allows the Glupteba gang to maintain control over all infected systems, despite losing access to their primary command servers today.
However, Google said that its actions "will materially affect the actor's ability to conduct future operations," something that will most likely result in the botnet losing steam in the coming months and reducing the overall threat to internet users.
Serious cybercrime is not an easy problem to solve, but I strongly believe that pressure from technical analysis, coordinated disruption and legal action can make a difference and keep users safer.
— Shane Huntley (@ShaneHuntley) December 7, 2021
I'm proud of this work and TAG's expansion into countering serious cyber crime.
What is Glupteba?
As for what Glupteba is and what it does; the reality is that this botnet has gone for years under the radar of most cybersecurity firms and experts.
First documented in a 2011 report from antivirus maker ESET, Glupteba is one of today's oldest malware botnets today.
It exclusively targets Windows systems and relies on cracked or pirated software and pay-per-install (PPI) schemes to infect its users. Once it has a foothold on an infected device, the Glupteba malware downloads different modules that can perform specialized tasks.
"Glupteba is known to steal user credentials and cookies, mine cryptocurrencies on infected hosts, deploy and operate proxy components targeting Windows systems and IoT devices."
Shane Huntley and Luca Nagy, threat analysts for the Google Threat Analysis Group
One of its most notorious modules is one that can spread an infection from a Windows computer to a MikroTik router found on internal networks. This particular module is believed to have been used earlier this year to assemble the Meris botnet, which was itself used over the summer to perform some of the largest DDoS attacks recorded to date.
Google sues two Russian nationals
But in addition to its attempt to cripple the botnet's active infrastructure, Google said today that it also identified two Russian nationals that were linked to some of the domains and accounts it has taken down today.
In court documents [PDF], Google names Dmitry Starovikov and Alexander Filippov as two of Glupteba's creators.
Google says the two operated several online websites where they advertised the botnet's capabilities, such dont.farm, a website where they sold access to compromised Google and Facebook advertising accounts. Google says the group obtained credentials to these accounts through their botnet, and they later sold access to other threat actors to use the accounts in other criminal schemes to place ads at the expense of the real account owner.
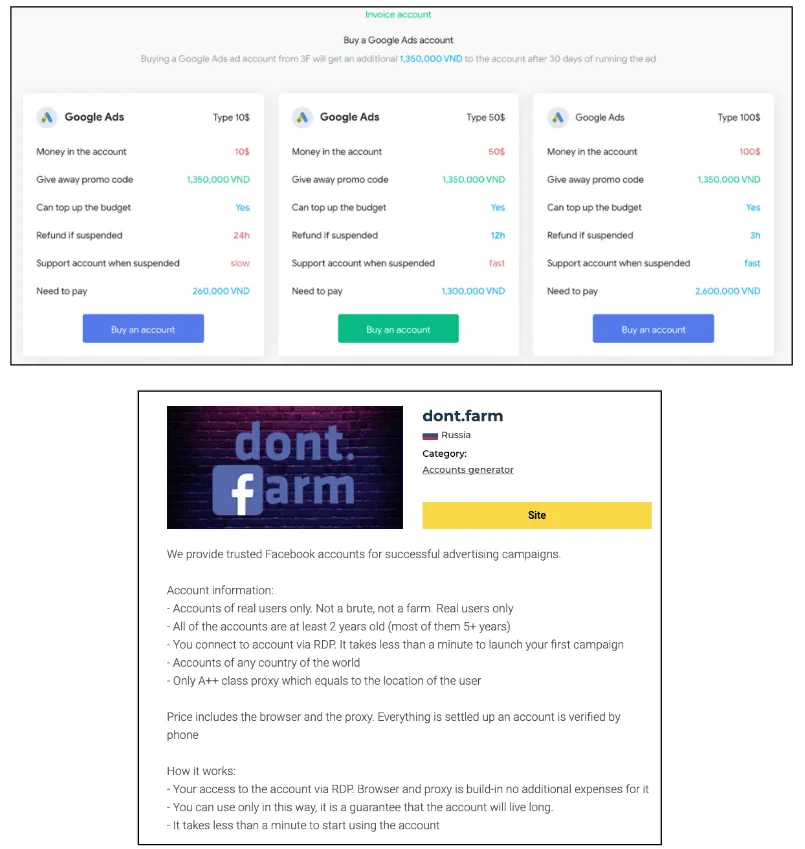
But Google says that this was only a part of the larger Glupteba "criminal enterprise" also included operating the AWMProxy.net (later rebranded as vd.net) and abm.net, websites that rented access to proxy networks hosted on Glupteba-infected computers.
Google is now seeking financial damages, an injunction against the two suspects to bar them from interacting with Google services, and a ruling that the two Glupteba members broke several laws, such as the Racketeer Influenced and Corrupt Organizations Act (RICO), the Computer Fraud and Abuse Act, the Electronic Communications Privacy Act, the Lanham Act, tortious interference of business relationships, and obtained unjust enrichment.
The hope is that Google's civil lawsuit will eventually trigger a criminal case that may lead to official charges against the two.
Google's lawsuit also comes a day after Microsoft took a similar legal step to seize 42 domains used by Chinese state-sponsored hackers in attacks against government agencies and think tanks in 29 countries.
Together with Facebook, Google and Microsoft are currently part of a trifecta of US tech companies that have been actively suing and using the courts to disrupt malware operations. Microsoft has filed 24 lawsuits so far, and Facebook is not far behind.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.


