Genesis Market, one of world’s largest platforms for cyber fraud, seized by police
Genesis Market was seized on Tuesday in an FBI-led operation involving more than a dozen international partners, scuttling one of the most significant online criminal platforms.
Genesis — which functioned as a one-stop-shop for criminals, selling both stolen credentials and the tools to weaponize that data — has been linked to millions of financially motivated cyber incidents globally, from fraud through to ransomware attacks.
A splash page revealing the takedown, titled Operation Cookie Monster, has now replaced the login pages on Genesis Market’s websites. The organization maintained sites on the dark web and regular web.
The Record understands that a large number of arrests are being carried out globally.
Genesis Market was unique among credential marketplaces such as Russian Market or 2easy Shop, according to Alexander Leslie, an analyst at Recorded Future, the parent company of The Record.
Unlike its competitors, Genesis Market provided criminals access to “bots” or “browser fingerprints” that allowed them to impersonate victims’ web browsers — including IP addresses, session cookies, operating system information, and plugins.
These fingerprints meant the criminals could access subscription platforms such as Netflix and Amazon — as well as online banking services — without triggering security warnings: “What’s Joe doing logging in from India?” as Leslie said. Users could even bypass multi-factor authentication.
“What makes the fingerprints on Genesis Store different is that they're emulating the victim's browser session — bypassing these ‘flags’ by appearing, to the victim, to be indistinguishable from the actual user,” Leslie said.
The data included in the “bots” was mostly harvested by infostealer malware, explained Leslie, who noted that unlike its competitors, Genesis Market did not have a list of third-party vendors, such as the RedLine, Vidar, Raccoon or META infostealers listed on Russian Market.
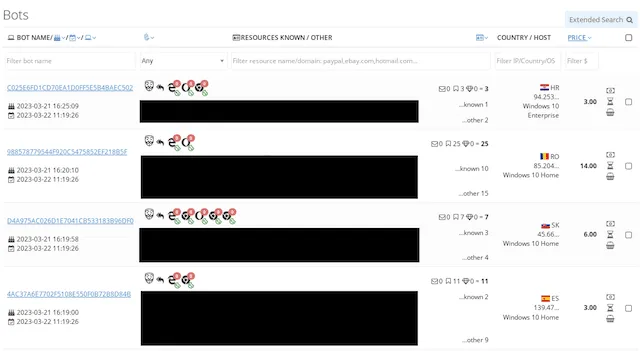
Bots listed on the Genesis Market. Image: Recorded Future
Once purchased, the “bots” could be imported into a browser the criminals had developed called Genesis Security, also available as an extension for other web browsers. The bots allowed criminals to masquerade using the stolen credentials.
Listings appeared alongside the services that fingerprints had access to, often including Netflix, Amazon, Facebook and eBay accounts. Bots could also include credentials for services that didn’t automatically appear in the listings, for instance employee networks.
“Everything matches — location, IP address, browser information, etc. When you have the Genesis Store browser extension installed, you can import the bot of your victim and the browser will immediately reset — assuming the ‘identity’ of your victim. To online services, this identity is similar — if not exactly the same — as the real user,” said Leslie.
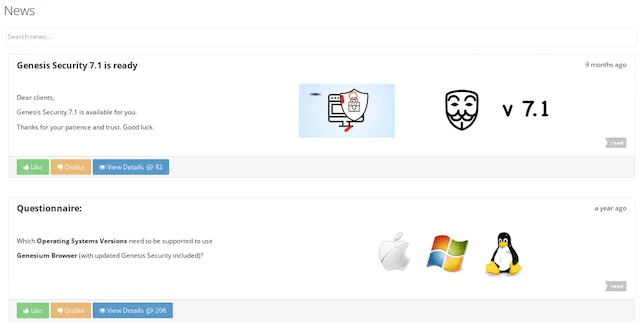
The platform provided a browser and plug-in so users could deploy "bots." Image: Recorded Future
Genesis Market was an invite-only site, but it was discoverable through regular web search engines. As with most large-scale criminal forums, invite codes were widely available, even being offered on YouTube videos.
The total number of Genesis Market victims isn’t known, although Leslie said that the Recorded Future platform showed approximately 135 million individual bot listings since 2018.
“Based on the current number of active listings, weighed against a sample size of the total number of platform references over the past month (1.3 million), I believe it is possible that Genesis Store has had somewhere between 30 and 50 million active listings over its lifespan,” said Leslie.
He cautioned the figure was only an approximation “as Genesis Store does not display historical records,” and that “the real number may be much higher.”
The low barrier to access was part of the design of the criminal service, which functioned as a one-stop-shop for fraud. Genesis even provided a Wiki explaining how it worked for new users in a bid to commoditize the fraud.
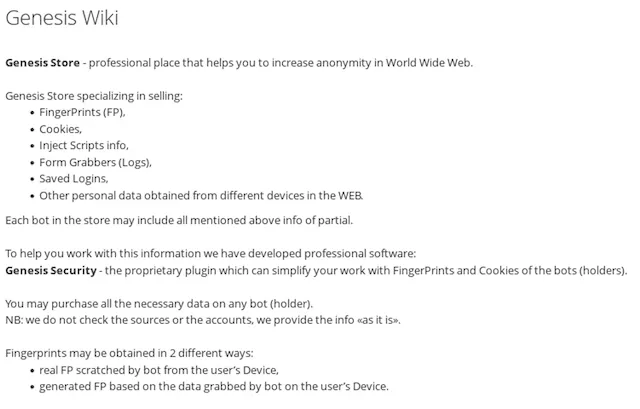
Genesis provided a wiki explaining how to commit fraud. Image: Recorded Future
“This implies that the infostealer ‘botnet’ is controlled by the Genesis Store administration,” meaning the criminals behind the Genesis Store also owned the “command-and-control for the entirety of its listings and have continuous access to infected machines,” said Leslie.
“That's part of what made the Genesis Store so effective. This constant communication with the infected machine means that the ‘bot’ is constantly updated or ‘fresh’, making the fingerprint as up-to-date as possible.”
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and is also a fellow at the European Cyber Conflict Research Initiative.