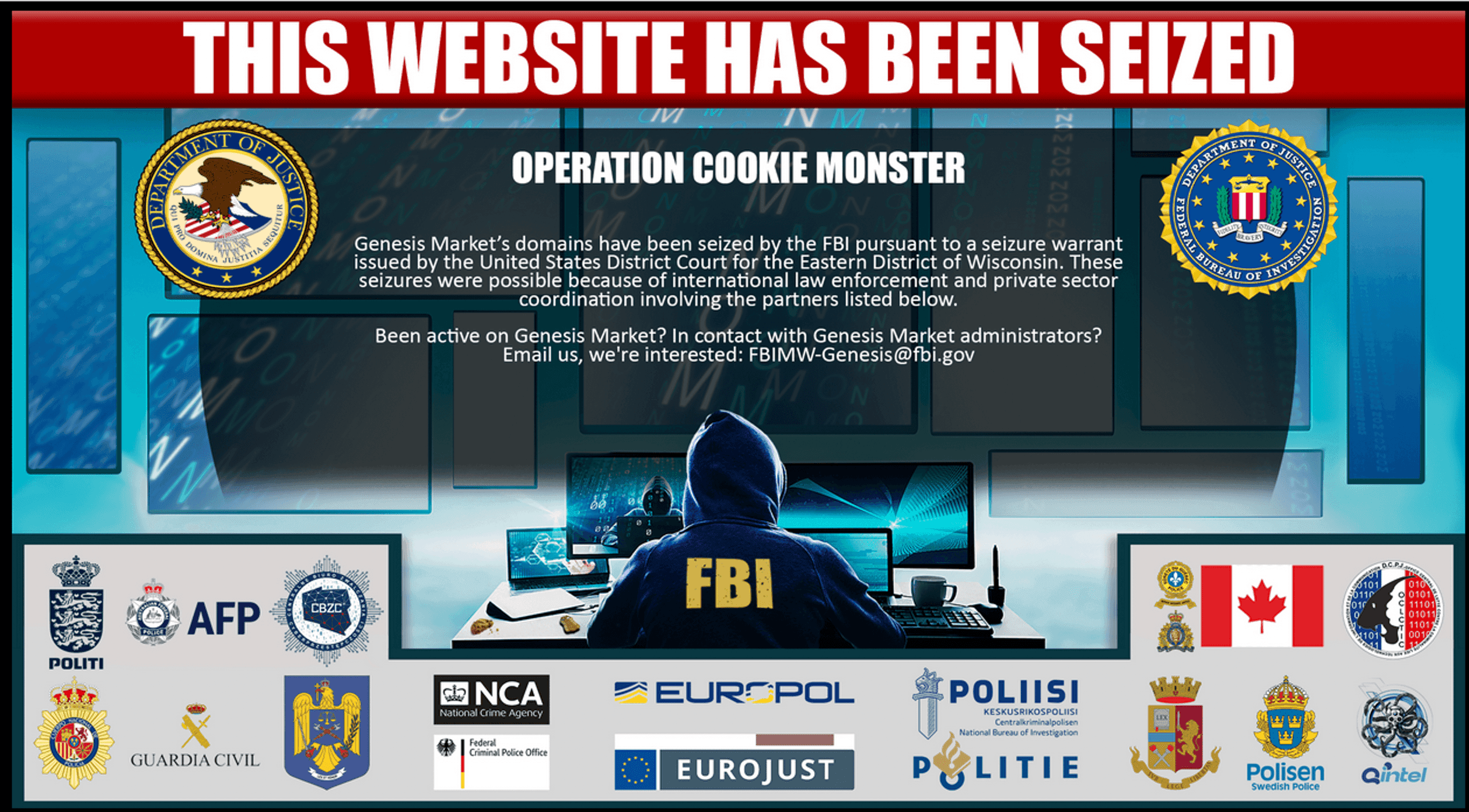
Genesis Market gang tries to sell platform after FBI disruption
The criminals behind the cyber fraud platform Genesis Market are attempting to sell their enterprise almost three months on from an FBI-led operation that seized their clear web domains and added the platform to the U.S. Treasury’s sanctions list.
An account that appears to be associated with Genesis Market’s operators has made several posts across darknet hacking forums to advertise the sale. The posts, which were made on June 28, have not previously been reported.
A post to sell the platform on CrdClub was first identified by Michele Campobasso, a researcher at the Eindhoven University of Technology, who has studied Genesis Market since 2020. Recorded Future News identified a second identical post on Exploit Forum.
Back in April, within the first 24 hours of the platform’s clear web domains being replaced by police splash pages, international law enforcement agencies announced the arrests of almost 120 people globally who had been using the platform to commit fraud.
Even more significantly for the site’s criminal users, senior officials at the FBI said they had identified and located Genesis Market's backend servers, obtaining “information about approximately 59,000 individual user accounts,” who could potentially be investigated in the future.
The platform’s dark web mirror remained active as it was “hosted in an inaccessible jurisdiction,” the U.K.’s National Crime Agency explained to Recorded Future News, but the international operation had an observable effect on the activity on both Genesis Market’s surviving .onion site and even its primary alternatives, Russian Market and 2easy Shop.
Cybercrime innovations
Unlike its competitors, Genesis Market did not just sell stolen data and credentials but also provided a platform to criminals that allowed them to weaponize that data using a custom browser extension to impersonate victims.
That offering made Genesis Market “an entirely new threat model” according to Campobasso, who is about to obtain his PhD from Eindhoven’s faculty of mathematics and computer science, and who describes the threat model as impersonation-as-a-service (IMPaaS).
 The law enforcement splash page posted on Genesis Market's websites.
The law enforcement splash page posted on Genesis Market's websites.
Campobasso had been closely monitoring Genesis Market since February 2020, when alongside his PhD supervisor Luca Allodi he began to scrape its contents to study how it functioned. Some of their findings are set to be presented at the 32nd USENIX Security Symposium next month.
“This is one of the few examples of innovation in the cybercriminal ecosystem,” said Campobasso, who described the platform as “a testament of the presence of expert and tech-savvy threat actors that understand market needs and manage to deliver credible attacker technology.”
An account with the same username as that advertising the sale had posted to the same criminal forums in the first few days following the takedown, claiming that the FBI had only seized Genesis Market’s open web domains and that its darknet platform remained safe to use.
Despite this attempt to address consumer confidence, criminal forums banned the account — a standard move in the underworld, where there is little trust for operators who have been successfully targeted by law enforcement.
The advertisements on criminal forums say the sale includes “all the developments, including a complete database (except for some details of the client base), source codes, scripts, with a certain agreement, as well as server infrastructure.”
Campobasso said: “One may speculate that the reason to sell the platform is at least partially due to the level of attention market operators have from law enforcement.”
It is not clear whether any purchasers would seek to retain the Genesis Market brand or if they would use the purchase to develop their own IMPaaS platform. Campobasso told Recorded Future News that “similar [IMPaaS] platforms are likely to follow in the future.”
This is not least because the service model “offers a cheap, outsourced and convenient solution to (at least attempt to) perform targeted attacks against companies (i.e., if you’re lucky, you can find credentials to internal services of an institution and with lateral movement potentially perform more disruptive attacks – like ransomware).”
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79



