GandCrab ransomware distributor arrested in South Korea
South Korean national police have announced today the arrest of a 20-year-old suspect on charges of distributing and infecting victims with the GandCrab ransomware.
The suspect, whose name was not released, operated as a customer of the GandCrab Ransomware-as-a-Service (RaaS) cybercrime operation.
Known as an affiliate —or a distributor— police say the suspect operated by taking copies of the GandCrab ransomware and distributing them via email to victims across South Korea.
Between February and June 2019, the suspect sent nearly 6,500 emails to South Koreans. The emails mimicked official communications from local police stations, the Constitutional Court, and the Bank of Korea.
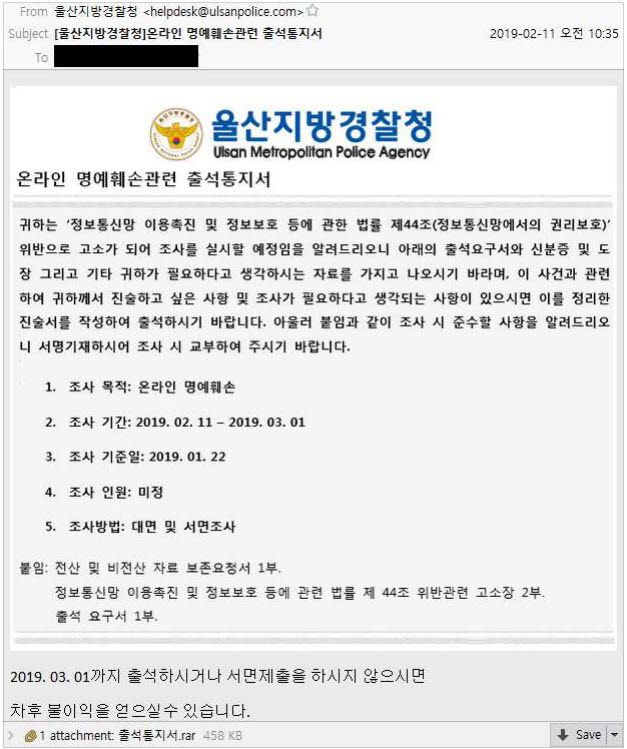
However, when victims opened documents attached to emails they received, they infected themselves with the GandCrab ransomware, which then proceeded to encrypt their files and ask for a $1,300 payment in Bitcoin.
South Korean national police say they tracked at least 120 users who fell victim to the suspect's phishing campaigns.
Despite the large number of victims, authorities said the suspect only made 12 million won, which stands to around $10,500, as he only received a 7% cut from the sum victims were paying on the GandCrab ransom portal.
Suspect tracked via cryptocurrency transactions
The suspect's attacks stopped in June 2019 after the GandCrab group announced their retirement and moved on to create and run the REvil (Sodinokibi) RaaS instead, which focused on infecting companies rather than regular users.
The South Korean individual marks the second GandCrab distributor arrested since the GandCrab shutdown. A 31-year-old suspect was previously arrested in Belarus in August 2020.
South Korean national police said the recent arrest, which took place last month on February 25, was the result of an international investigation led by Interpol focused on tracking down the GandCrab gang and its network of distributors. Law enforcement agencies from ten countries are involved in the investigation.
Authorities also said they tracked the suspect based on cryptocurrency transactions associated with the GandCrab operation, which led them to the suspect's bank account, despite him using a cloak of servers and IP addresses to hide his real location.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



