Fujitsu suspends ProjectWEB platform after Japanese government hacks
Japanese tech giant Fujitsu has temporarily taken down its ProjectWEB enterprise software-as-a-service (SaaS) platform after hackers gained access to its systems and stole files belonging to multiple Japanese government entities.
Impacted agencies whose names have been made public so far include the Ministry of Land, Infrastructure, Transport, and Tourism; the Ministry of Foreign Affairs; the Cabinet Secretariat; and the Narita Airport.
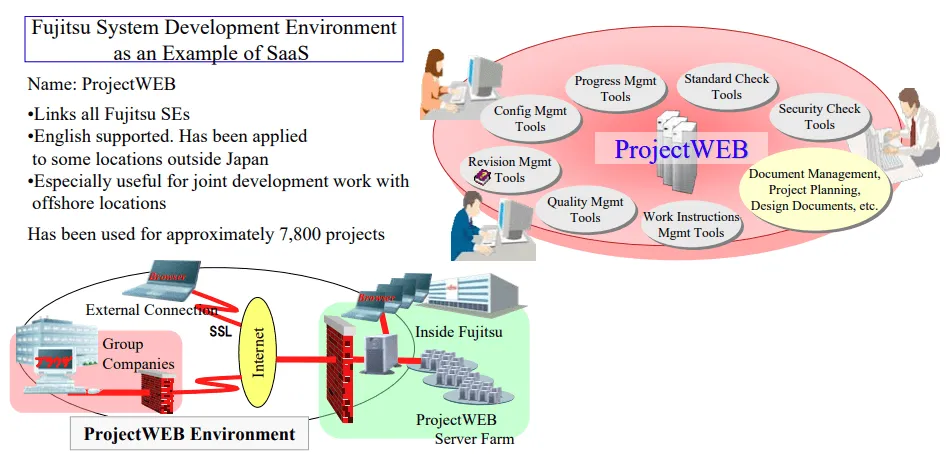
Stolen data included files that government employees stored on ProjectWEB, a cloud-based enterprise collaboration and file sharing platform launched by Fujitsu in the mid-2000s and which is broadly used today by Japanese government agencies.
According to the Cabinet Cyber Security Center (NISC), which is investigating the incident on behalf of the Japanese government, the intrusion was detected by Fujitsu on Monday, May 24.
A day after the attack was detected, Fujitsu shut down the ProjectWEB platform to investigate the "scope and cause" of the breach and after pressure from NISC investigators.
Local press reported that the hackers stole documents that contained more than 76,000 email addresses for employees and contractors for the Ministry of Land, Infrastructure, Transport, and Tourism, but officials did not confirm the reports in a press conference on Wednesday.
However, at the time of writing, no additional details about the intrusion are known, such as the identity of the attackers and their goals.
The ProjectWEB breach comes after Japanese government agencies were targeted in similar attacks earlier this year. The previous attacks targeted FileZen file-sharing servers made by Soliton, which are also broadly used by Japanese government agencies.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



