Freedom Hosting admin gets 27 years in prison for hosting child pornography
An Irish man who ran a cheap dark web hosting service has been sentenced today to 27 years in prison for turning a blind eye to customers hosting child sex abuse material.
Eric Eoin Marques, 36, from Dublin, operated the Freedom Hosting service between July 2008 and July 2013, when he was arrested following an FBI investigation.
One of the largest facilitators of child pornography in the world
"The investigation revealed that the hosting service contained over 200 child exploitation websites that housed millions of images of child exploitation material," the US Department of Justice said today, announcing Marques' sentencing.
Over 1.97 million of these images and/or videos were not previously known by law enforcement. Many of these images involved sadistic abuse of infants and toddlers to include bondage, bestiality and humiliation to include urination, defecation and vomit.
US Department of Justice
US prosecutors, who have worked on the case for almost eight years, described Marques as "one of the largest facilitators of child pornography in the world."
Some of the child pornography portals hosted on Freedom Hosting included Lolita City, the Love Zone, and PedoEmpire.
The service also hosted anonymous email service TorMail, dark web index HiddenWiki, and carding forum HackBB, along with other sites peddling various illegal services.
Users who wanted to host a site on the dark web accessed the Freedom Hosting site via the Tor Browser, registered an account, paid a $5 one-time fee, and then deployed their site on a classic PHP+MySQL hosting environment. At one point, it was believed that the site hosted about half of all dark web (.onion) sites.
All dark web portals were hosted on servers belonging to Marques' real-world company, the now-defunct Host Ultra Limited.
The Freedom Hosting service came under an official investigation towards the end of 2011 when it found itself in news headlines after members of the Anonymous collective exposed it as a primary host of child pornographic content on the dark web and bombarded the site with huge DDoS attacks.
Marques tried to seek shelter in Russia
Details about how the FBI tracked down Marques remain unknown, but he was arrested two years later, in July 2013. All Freedom Hosting sites were taken down a week later, on August 3, 2013.
Marques' fought his extradition for six years and even tried to obtain Russian citizenship. US officials managed to get him in the US in March 2019, and he pleaded guilty a year later in February 2020.
He was sentenced this week to 27 years in prison, from a maximum of 30. If released, he will be on a lifetime supervised release.
The FBI deployed malware via Freedom Hosting's servers
But the Freedom Hosting investigation is notorious today for other reasons than the sheer scale of the child abuse material that was hosted on its servers.
The case is one of the first known incidents where the FBI deployed malware as part of an investigation.
According to court documents released throughout the years, after seizing Freedom Hosting servers at the end of July 2013, the FBI kept the infrastructure running for another week, during which time they secretly deployed a JavaScript file to all sites hosted on the Freedom Hosting platform.
The script worked by exploiting a bug in Firefox — the browser on which the Tor Browser was built — to bypass the IP anonymization features of the Tor network and collect the real-world IP address of users accessing child pornography portals.
This information was then sent to an FBI-controlled server, and officials used the data to launch other investigations and track down other suspected pedophiles.
Since then, the FBI used similar exploits in the Playpen investigation, but the Freedom Hosting incident revealed the FBI's penchant to deploying offensive hacking tools when going after child abuse sites.
Freedom Hosting copycats
But even if Freedom Hosting suffered a highly mediatized fallout, that didn't stop copycats from popping up on the dark web, offering similar hosting services, and using the same brand.
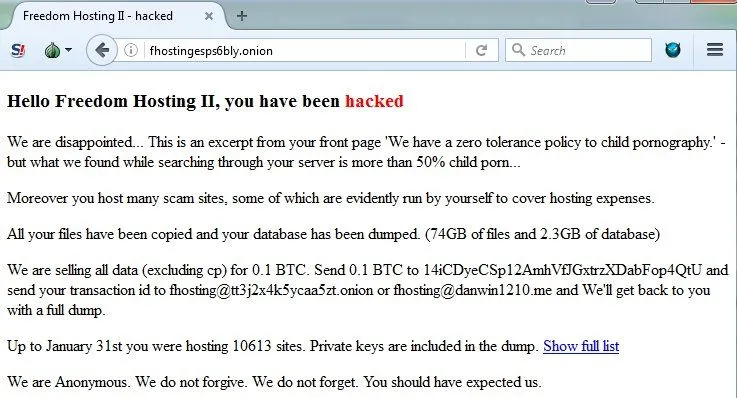
One of the most infamous copycats was Freedom Hosting II, which was hacked and taken down by the Anonymous collective in February 2017, under the same accusations that it was hosting a slew of child pornography sites, like its predecessor.
Other copycats like Freedom Hosting III or Freedom Hosting Reloaded also surfaced in the following years, with the latter still running today.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.


