Free decrypter released for the TargetCompany ransomware
Czech security firm Avast has released today a free utility that can help victims of the TargetCompany (Tohnici) ransomware recover their files without paying the ransom demand.
The company said it created the app, called a decrypter, after one of its customers was hit by the ransomware and needed a way to recover their files.
First spotted in June 2021, TargetCompany is one of the smaller ransomware gangs active today, engaged in attacks against companies and home consumers alike.
Seems #TargetCompany #Ransomware is branching out and also hitting home users now with a new ".mallox" variant... if you've been hit by this extension, please DM me with an encrypted file.
— Michael Gillespie (@demonslay335) December 3, 2021
In order to create the decrypter, Avast said it reverse-engineered the TargetCompany ransomware, and its novel encryption scheme made up of a mix between the ChaCha20, AES-128, and Curve25519 algorithms.
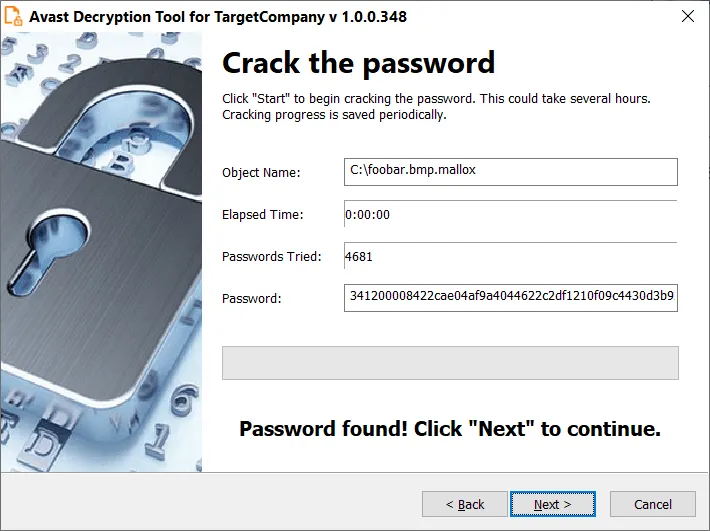
The security firm said its decrypter can be used to crack the encryption password and recover files without paying the ransom, but it can also be used with a decryption password provided by the attackers in order to make sure files are decrypted correctly.
If customers choose to crack the password, Avast researchers said this process might take tens of hours, but there's the added benefit of not having to pay the attackers.
The decrypter is available in 32-bit and 64-bit versions, and should work for versions of the TargetCompany ransomware that encrypted files with the architek, exploit, brg, and mallox file extensions.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



