Fraud Family phishing-as-a-service disrupted in the Netherlands
Dutch police have arrested two suspects this week who created and hosted phishing sites for other cybercrime groups as part of an online service they were calling The Fraud Family.
Police officers arrested a 24-year-old man from the city of Arnhem and a 15-year-old boy from the town of Loenen aan de Vecht.
Investigators said the former developed the phishing kits, while the latter had been responsible for selling access to the tools developed by his partner.
Police also searched the house of a third suspect, an 18-year-old teen from Hoogeveen, but his role in the operation was not detailed.
The arrests, which took place on Tuesday but were announced today, came after a report from Group-IB, a security firm specializing in financial fraud and security for the banking sector, which has been dealing and investigating phishing sites created by the gang's tools since last year.
The Fraud Family phishing-as-a-service operation
According to Group-IB, the group has been active since the beginning of 2020, when the group began building phishing toolkits, which they would later advertise on Telegram channels, typically named The Fraud Family.
Over the past two years, Group-IB said it tracked over eight Telegram channels where the group had been selling its phishing toolkits.
The whole network of channels has close to 2,000 subscribers. Their most popular group has 640 members. According to Group-IB assessment, half of these users could be actual buyers.
Group-IB Europe
But while the group sold self-standing phishing kits, they also ran a phishing-as-a-service platform where they offered to host phishing sites and backend panels for cybercrime gangs that did not have the technical know-how to operate and host their own infrastructure.
This platform came with anti-bot tools to prevent security researchers from accessing and analyzing the phishing sites but also features to prevent web crawlers for security scanners like VirusTotal and URLScan from detecting the phishing operations.
Prices for these hosting plans usually ranged between €200/month for the Express Panel offering or €250/month for the Reliable Panel.
Most customers were from Belgium and the Netherlands
Both Dutch police and Group-IB said the group's phishing toolkits were widely used to attack banks and their customers in the Netherlands and Belgium.
The phishing toolkits were often spotted in two types of operations, with the first using email and SMS spam to lure users on phishing sites, while the second tactic relied on ads posted on Dutch classified ads sites, luring users on the phishing site after a short WhatsApp interaction.
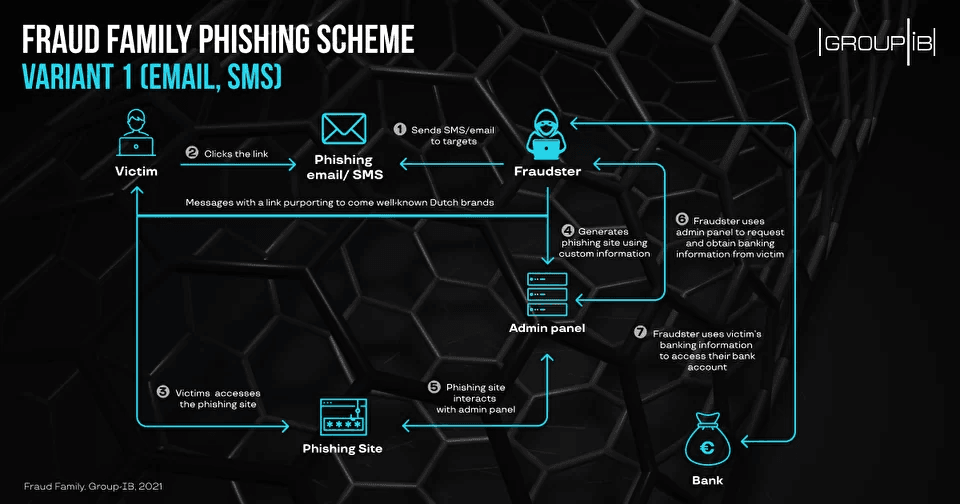
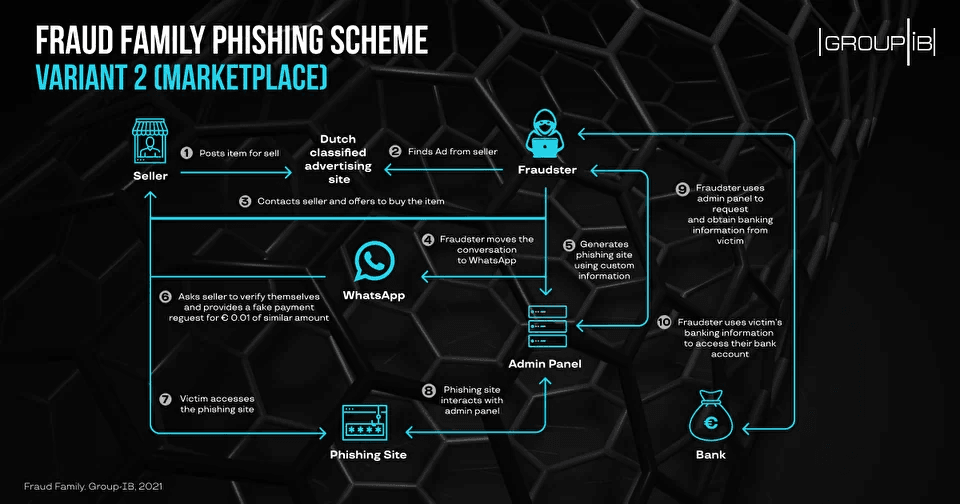
Once users landed on any of these phishing sites, they would typically be prompted at one point or another to log into their e-banking account in order to make a payment or approve a transaction.
Typically, the phishing sites came with a selector to allow victims to pay with their desired bank account, meaning the phishing toolkits were also pre-configured with a wide set of spoofed bank login screens.
Furthermore, Group-IB said the phishing toolkits were very advanced, being also capable of bypassing two-factor authentication.
The toolkits usually came with a real-time notification feature that would alert operators when a victim was interacting with the fake login form. This way, the operator would be in front of their computer to collect credentials and 2FA tokens from victims and log into their bank accounts in real-time, as the users were still on the phishing sites.
NL Multipanel, Express Panel, and Reliable Panel
Over the past two years, Group-IB said the Fraud Family had been linked to at least three different phishing kits, namely NL Multipanel, Express Panel, and Reliable Panel.
NL Multipanel was the first product they developed, which group forked from a leaked version of another phishing toolkit named U-Admin (uPanel).
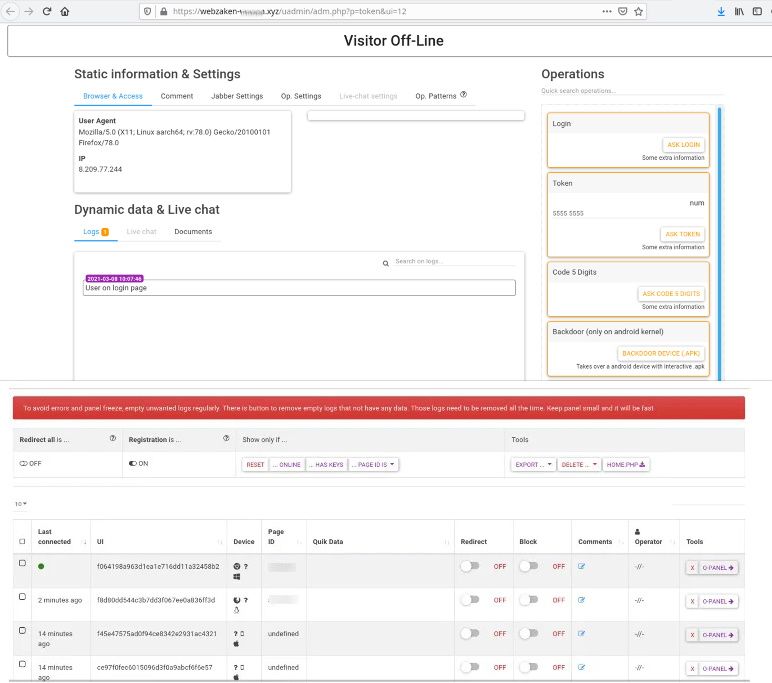
However, the group also began working on creating their own phishing toolkits. Developed in November 2020 and named Express Panel and Reliable Panel, the two were major improvements from NL Multipanel, and customers slowly migrated to these two, especially after the U-Admin coder, a Ukrainian national, was arrested earlier this year and U-Admin became a tainted brand.
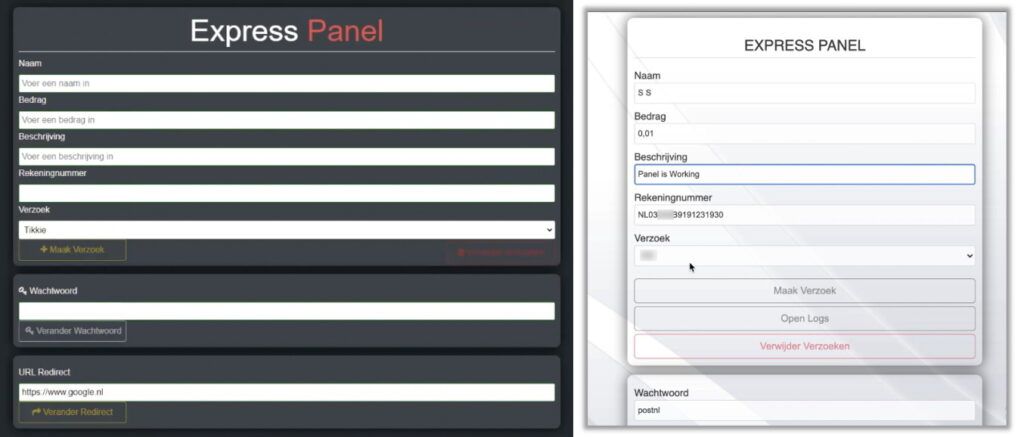
- Coded in PHP.
- Not based on U-Admin and sellers made sure to advertise it.
- Very light panel with a simple user interface.
- Optimized to be used with a mobile phone.
- Allows live interaction with victims.
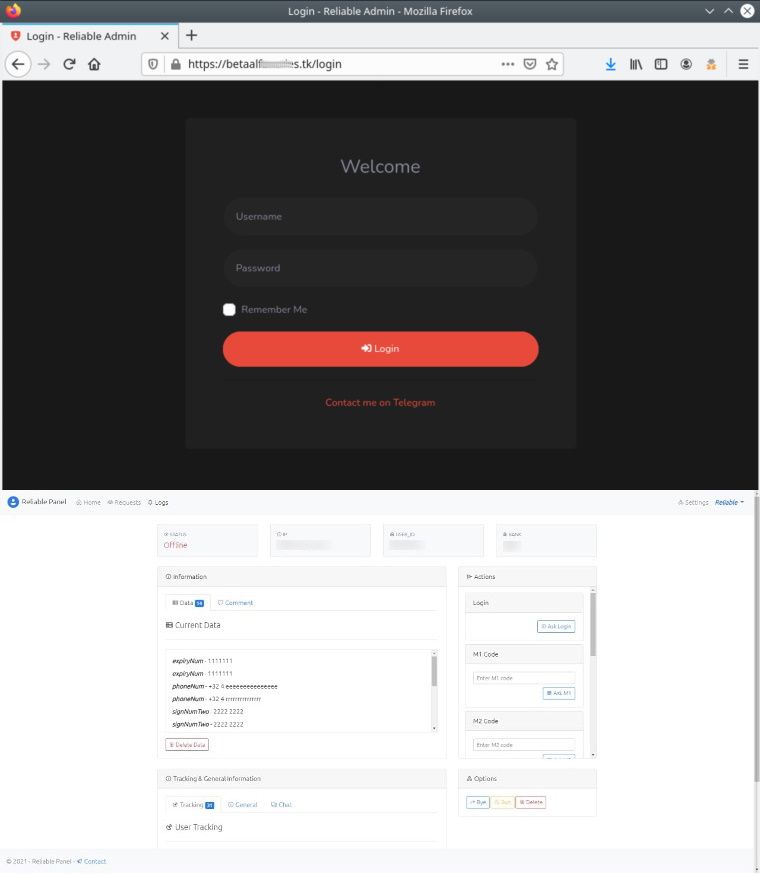
- Developed from scratch and based on Nodejs instead of PHP.
- Faster than NL Multipanel and its variants.
- Fully customizable.
- Allows live interaction with victims.
- Specially crafted for the Dutch and Belgian markets.
Dutch police send a warning
This week's arrests and takedown effectively spell the end of the Fraud Family and its phishing-as-a-service offering among the local market.
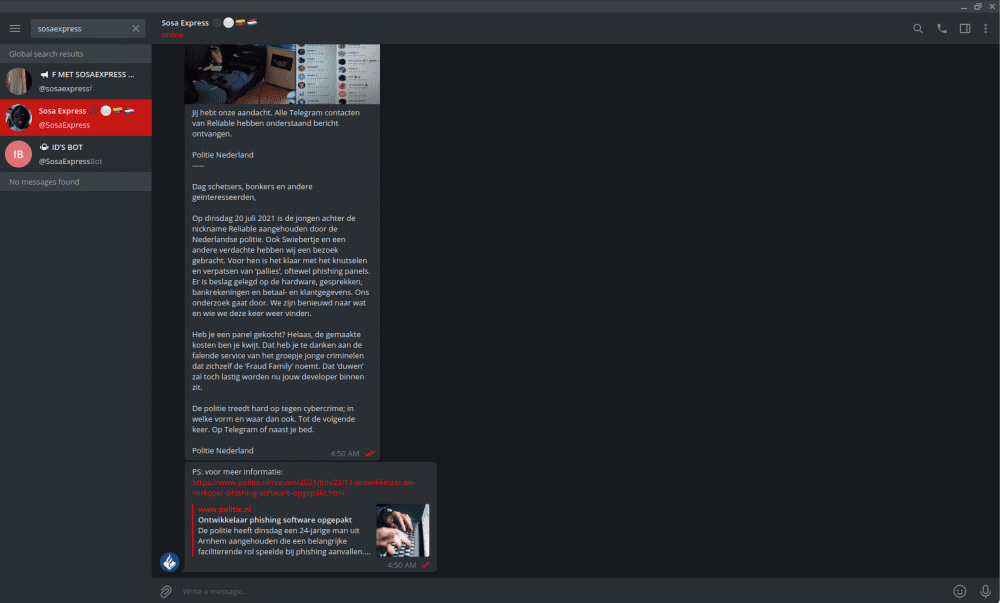
But besides the two arrests, Dutch police have also taken a rare step to message all members of the Fraud Family Telegram channels to notify them about the arrests and warn them against carrying out future attacks against Dutch targets.
This marks the second time Dutch police have done this after they posted a similar message on the RAID and XSS hacking forums earlier this year, warning members that hosting cybercrime infrastructure in the Netherlands was "a lost cause."
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



