Fort Worth gov’t officials confirm cyber incident but deny leak of sensitive info
Officials in Fort Worth, Texas, confirmed that a website with government information was breached and accessed by a group of hackers but downplayed the severity of the incident.
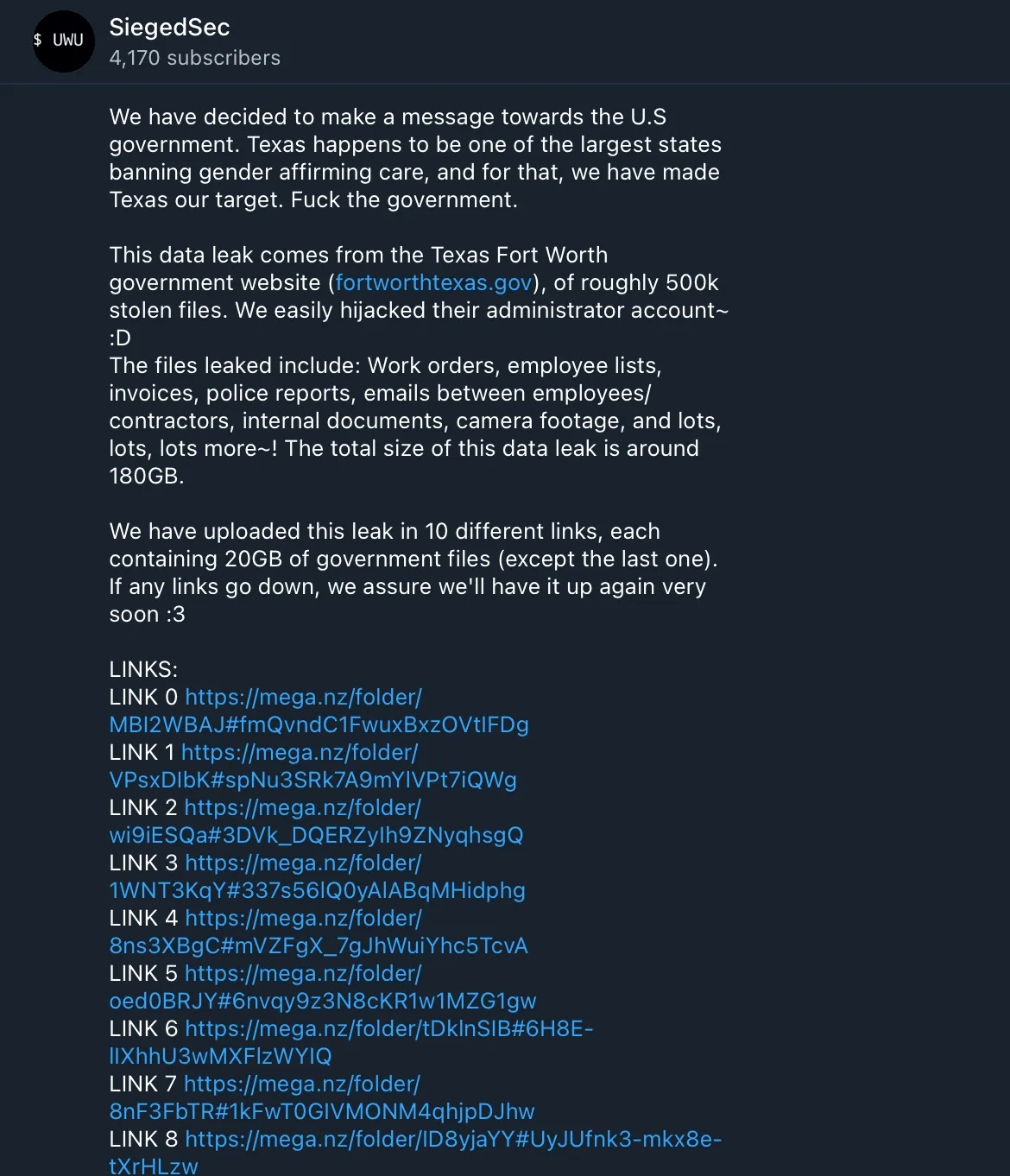
On Friday, a hacking group named SiegedSec took to Telegram to claim that it stole about 500,000 files from the government of the city, which has more than 935,000 residents.
The group claimed it stole administrator credentials and made copies of work orders, employee lists, invoices, police reports, emails between employees/contractors, internal documents, camera footage and more — about 180GB of data in total.
The group did so, it said, because of Texas state politics.
“Texas happens to be one of the largest states banning gender affirming care, and for that, we have made Texas our target,” the group said.
“Now you may think, ‘SiegedSec! What if the F.B.I comes after you???’ And to that we say, "GOOD LUCK, WE'RE BEHIND 7 PROXIES!" Enjoy.”
A spokesperson for the city government directed Recorded Future News to a press conference held on Saturday, where the city’s Chief Technology Officer Kevin Gunn confirmed the attack.
Gunn said the city was initially informed of SiegedSec’s posting on Friday afternoon by the Texas Department of Information Resources’ Computer Incident Response Team.
“The city of Fort Worth has confirmed that the posted information did originate from our computer systems. However, that data came from a website that our workers use to manage their maintenance activities and not from the city's public facing intranet website,” Gunn said.
“It appears the hackers downloaded file attachments to work orders within the system and those attachments include things like photographs, spreadsheets, invoices for work performed, emails between staff, PDF documents and other related materials for work orders.”
A sample of the documents shared by SiegedSec and viewed by Recorded Future News corroborates that assessment.
But despite what was leaked, Gunn claimed that their investigation has not found any “indication that there has been sensitive information related to either residents or businesses or employees that has been released as part of this incident.”
As an example, Gunn said the average document leaked concerned things like potholes or sidewalks that needed repair.
None of the information was “sensitive in nature,” Gunn said, adding that overall most of it is data that “would be released through a Public Information Act request.”
Gunn said the investigation uncovered that the group stole login information but it is unclear how they managed to accomplish that. No other systems were accessed and no sensitive data was accessed or released, Gunn reiterated.
Officials have since removed the system from the external internet and forced all users to reset their passwords.
Both federal and local law enforcement officials are involved in the investigation.
Gunn confirmed that the incident did not involve ransomware and said it was vastly different from what was seen last month in the city of Dallas, which was hit with a devastating ransomware attack.
SiegedSec has not asked the city for a ransom, according to Gunn. When asked by reporters what motivated the group, he referenced their Telegram post, noting that they appeared interested in embarrassing the city and “making a political statement.”
The city will offer credit monitoring services to those affected if their investigation reveals that sensitive data was included in the leaks.
SiegedSec claimed it hacked the government of Arkansas and Kentucky last year after the state banned abortion following the Supreme Court decision to overturn Roe v. Wade.
But state officials later confirmed that the group simply downloaded publicly available record data.
Emsisoft threat analyst Brett Callow said it is still unclear what SiegedSec’s motivation is or where they are based.
“It could simply be a hacktivist group, or it could be a state-linked operation intent on causing social instability,” he said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



