First malware discovered targeting Windows Server containers
Security experts said they've discovered the first known malware strain that targets and then escapes Windows Server containers in order to infect a victim's Kubernetes cluster infrastructure.
The attacks, discovered by security firm Palo Alto Networks earlier this year in March, are believed to have been taking place for at least a year.
According to the researchers, the threat actor behind this campaign has been scanning the internet for common cloud applications such as web servers and deploying exploits for old vulnerabilities in order to gain a foothold on the unpatched application.
If the web app runs inside a Windows Server container, the attacker deploys a strain of malware named Siloscape that uses a previously documented Windows container escape technique to get access to the underlying operating system.
If the OS runs as a Kubernetes node, the attacker extracts and collects the node's credentials, which researchers believe they might use to pivot to a company's internal Kubernetes infrastructure to deploy new nodes with malicious capabilities.
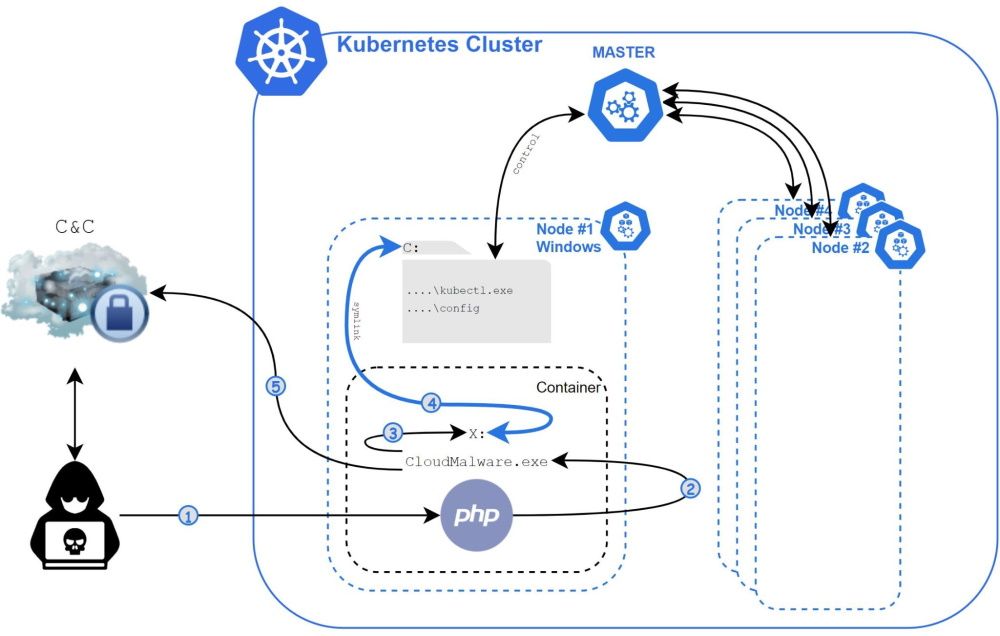
Siloscape also downloads and installs the Tor client in order to contact its command and control server and receive commands.
Palo Alto Networks said it was able to gain access to this C&C server, and, at the time of writing, the threat actor appears to have infected more than 300 systems.
However, researchers have not observed any malicious activity coming from the threat actor, so far.
Unlike other malware targeting containers, which are mostly cryptojacking-focused, Siloscape doesn't actually do anything that will harm the cluster on its own. Instead, it focuses on being undetected and untraceable and opens a backdoor to the cluster.
Daniel Prizmant, Senior Security Researcher at Palo Alto Networks
The security firm is now warning companies to take action and move applications from Windows containers to Microsoft's newer Hyper-V virtualization technology, which even Microsoft recommends using instead of its older and less-secure container mechanism.
Prizmant said companies that fail to heed this advice risk having crucial internal systems compromised by the threat actor. While this particular actor is very likely to engage in disguised cryptocurrency mining for their own profits, the actor could also rent access to some of the larger hacked companies to other criminal groups, such as ransomware gangs, for larger profits.
Until companies find a way to migrate from Windows Server containers to Hyper-V, they should deploy systems to detect Siloscape attacks. Indicators of compromise (IOCs) from the Siloscape campaign are available in the Palo Alto Networks report.
Because Siloscape is not a widespread campaign, for the time being, some of the malware's artifacts have been hard to track down, but some files have been found and shared by the vx-underground community earlier today.
We've aggregated samples from @Unit42_Intel 's latest paper on Siloscape.
— vx-underground (@vxunderground) June 7, 2021
You can download Siloscape here: https://vxug.fakedoma[.]in/tmp/
* File: Siloscape
* Size: 74.8KiB compressed
* Link modified to conform with Twitters ban on our domains https://t.co/UtN2OEEggA
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



