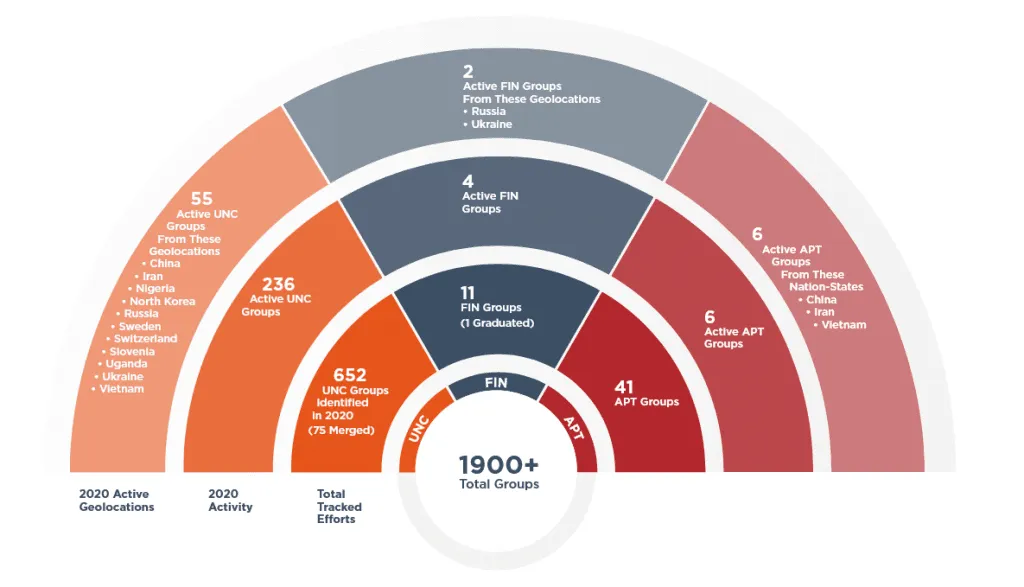
FireEye: More than 1,900 distinct hacking groups are active today
US cybersecurity firm FireEye says that based on its internal data, there are currently more than 1,900 distinct hacking groups that are active today, a number that grew from 1,800 groups recorded at the end of 2019.
In its yearly cybercrime report, the company said it discovered 650 new threat actors during 2020, but new evidence also allowed it to remove 500 groups from its threat actor tracker due to overlaps in activity and hacking infrastructure with previously-known clusters.
The 1,900 figure includes nation-state-sponsored threat actors (known as APTs), financially motivated groups (known as FINs), and uncategorized groups (known as UNCs) about which information is still scarce to place them in either of the first two categories.
Threat actors deployed 514 new malware strains in 2020
Per FireEye, these groups were also responsible for developing more than 500 new malware families during the past year, a number on par with the previous year's output.
Of the 514 newly tracked malware families in 2020, the top five categories were backdoors (36%), downloaders (16%), droppers (8%), launchers (7%), and ransomware (5%).
Moreover, 19% were malware tools that were publicly available, while 81% were tools that were either privately developed or their availability was restricted to tightly controlled circles.
The most common malware strains were the Beacon backdoor that's included in the Cobalt Strike adversary emulation toolkit, the Empire post-exploitation framework, the Maze ransomware, the Netwalker ransomware, and the Metasploit penetration-testing toolkit.
What's noteworthy on this list is that three of 2020's top five most encountered malware strains were not actually malware per-se but legitimate offensive security tools developed by the cybersecurity community(i.e., Beacon, Empire, and Metasploit), which have been adopted in recent years by threat actors and are now seeing widespread usage/abuse.
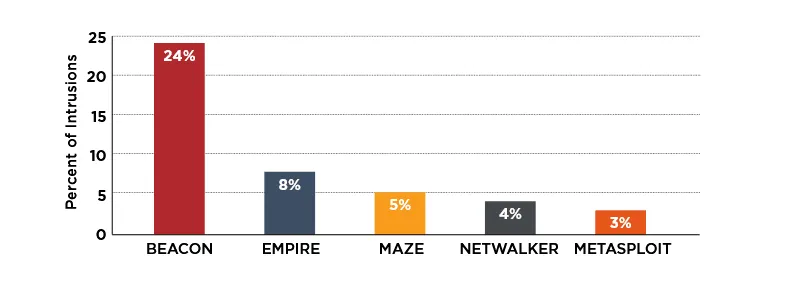
However, FireEye also notes that the Beacon backdoor is, by far, the most popular malware strain that was seen deployed in real-world intrusions in 2020, with the Cobalt Strike module being seen in roughly a quarter of all incidents investigated by FireEye analysts.
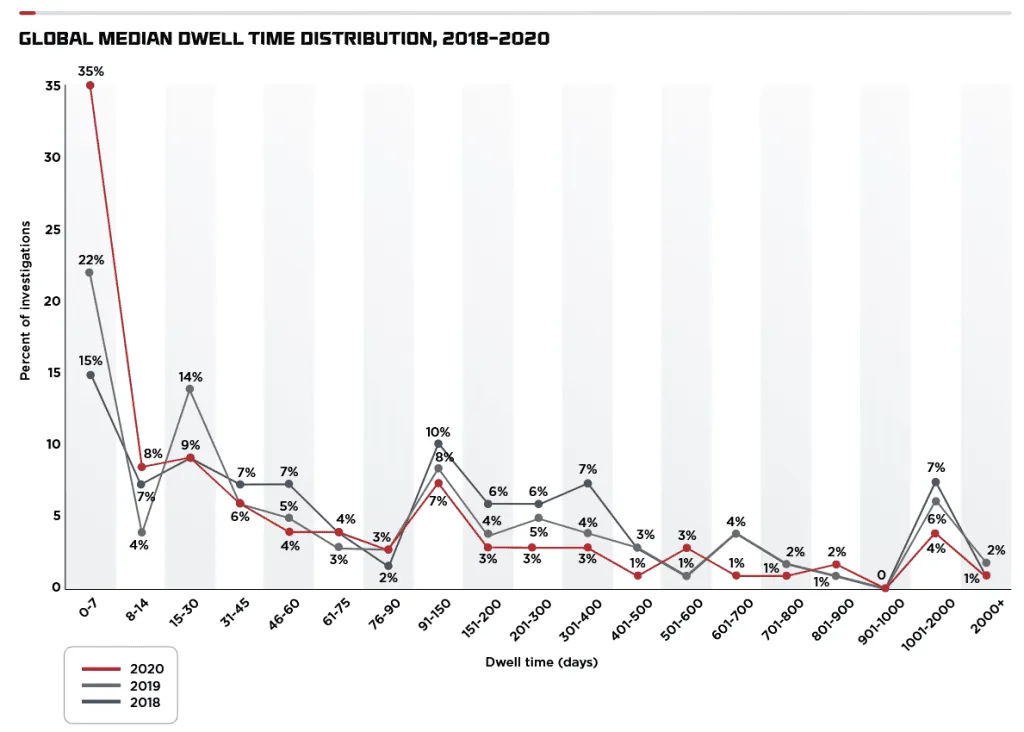
As for "dwell time," FireEye said that in 35% of the breaches it investigated, hackers had free access to a network for a week before being detected and kicked out.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



