FIN7 hacker trialed in Russia gets no prison time
A Russian court handed down a mild one-year suspended prison sentence to a member of the FIN7 hacking group, a notorious cybercrime cartel that has hacked more than 100 US companies between 2015 and 2018.
The man, whose identity was not initially shared in a press release circulated to Russian media last week, was identified today by The Record in Russian court proceedings as Maxim Zhukov Sergeevich (Максим Жуков Сергеевич), a 36-year-old from the city of Vladimir.
Zhukov previously worked as a developer for Combi Security, a Russian company that the US Department of Justice described in 2018 as a front company and fake security firm through which FIN7 hired new members and used them to hide intrusions as penetration tests.
According to public directories [archived], Zhukov worked as a Ruby programmer specialized in Metasploit, a legitimate penetration-testing framework that was a known tool used by FIN7 in past operations.

Zhukov was identified as a FIN7 member and detained by Russia's FSB security service in February 2019 and later accused of creating malware specialized in the theft of money from bank accounts.
His arrest came months after the FBI cracked down and arrested three Ukrainian nationals across Europe for running Combi and FIN7 operations.
The FBI said the group hacked more than 100 US companies and orchestrated intrusions at tens of US retailers, such as Chipotle Mexican Grill, Chili's, Arby's, Red Robin, and Jason's Deli, where they deployed malware that collected millions of customer payment card details that they later sold on hacking forums.
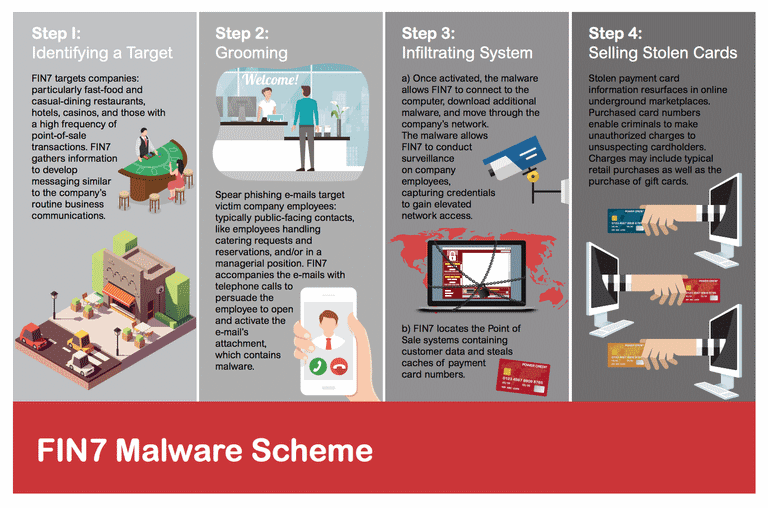
Zhukov is the fifth FIN7 member identified by law enforcement agencies and the third to be sentenced after two Ukrainian nationals received hefty prison terms in US jails.
He is the second Russian national identified to have been part of the FIN7 group but is the first to be trialed in Russia. Zhukov is also the first hacker part of a major cybercrime cartel to be detained and trialed in Russia in many years, since the Lurk arrests of 2016.
NameAgeCountryDetailsSentenceDmytro Fedorov47UkraineWas a high-level hacker and manager who assigned tasks and supervised other FIN7 members. Was detained in Poland and still fighting his extradition to the US.--Fedir Hladyr36UkraineWas one of the group's leaders and served as systems administrator, maintaining servers for the gang. Was arrested in Germany in January 2018.10 yearsAndrii Kolpakov33UkraineWorked as a manager and recruiter for the gang, hiring and supervising hackers. Was arrested in Spain in June 2018. 7 yearsDenys Iarmak--RussiaWas a FIN7 penetration tester. Was detained in March 2020. Expected to plead guilty. --Maxim Zhukov36RussiaWas a FIN7 malware dev1 year suspended, 1 year probation
FIN7 has shifted to ransomware
But despite the 2018 arrests, the remaining FIN7 group members have not stopped their attacks but shifted gears from targeting point-of-sale operations to conducting ransomware attacks, which began yielding higher ransom payments about the time the FBI had arrested their previous leadership structure.
Since the arrests, FIN7 is now a major player on the ransomware scene, where after working as an affiliate for various ransomware groups like Maze, Egregor, REvil, and BitPaymer, they have now launched not one but two Ransomware-as-a-Service (RaaS) offerings of their own.
Speaking on stage at the Mandiant Defence Summit in October, Microsoft security researchers Nick Carr and Christopher Glyer said that a smaller group inside FIN7, which they are tracking as ELBRUS, is the group that created and ran the Darkside and BlackMatter RaaS platforms.
Two of the most prodigious and advanced RaaS offerings in the criminal underground in recent years, both are now down. FIN7 closed the Darkside RaaS after the attack on Colonial Pipeline, and they shut down BlackMatter last month after pressure from Russian authorities.
But while FIN7 switched its targeting from Point-of-Sale malware to ransomware, they have not changed their tactics that much.
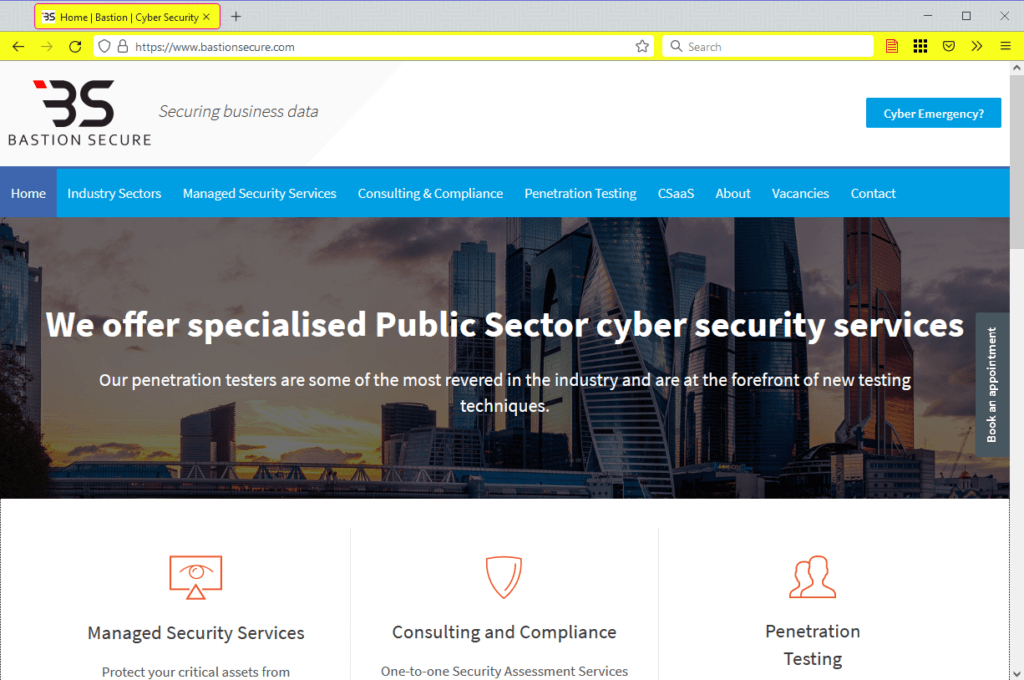
According to Microsoft and Gemini Advisory, the group has even set up a second fake security firm, named Bastion Secure, which they have been using to hire security researchers and trick them into conducting hacks disguised as "customer penetration tests." Following these intrusions, the group has often deployed the Darkside and BlackMatter ransomware.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.


