FIN7 cybercrime cartel tied to Black Basta ransomware operation: report
Cybersecurity researchers said they have tied the long-running cybercrime cartel FIN7 to the Black Basta ransomware operation — a group behind high-profile attacks on the American Dental Association and German wind farm operator Deutsche Windtechnik.
A new report from SentinelOne found that in multiple Black Basta incidents, the threat actors made use of a custom cyberdefense impairment tool that FIN7 developed.
SentinelOne’s senior threat intelligence researcher Antonio Pirozzi noted that FIN7 has previously been tied to other notable ransomware operations like Darkside, BlackMatter, REvil and ALPHV.
“The exact nature of the involvement is open to speculation, but it is based on signing certificates used by FIN7 to sign ransomware or the presence of FIN7 backdoors and toolkits in ransomware incidents,” he said.
“Other researchers have identified multiple threat actor clusters as being affiliated with FIN7 with varying levels of confidence. One important highlight of the report is that we assess with high confidence that Black Basta is a private operation and not a Ransomeare-as-a-service (RaaS). This leads to a high level of control over all the operations and special trust into the different possible affiliations.”
Pirozzi explained that it “would not surprise” him if Black Basta is a FIN7-owned operation but noted that the “level of collaboration likely goes beyond selling/buying some tool advertised in some cybercrime forum somewhere.”
“The testing of the evasion tools is tightly connected to the deployment phase, and appears to be something quite unique and specific to Black Basta,” he added.
Several ransomware experts confirmed the report's findings and noted that the two had been previously tied based on the tools used.
The report also highlights the way Black Basta operators use several popular vulnerabilities including PrintNightmare, ZeroLogon and NoPac.
The ransomware emerged in April and quickly racked up more than 90 attacks on organizations by September.
“The rapidity and volume of attacks prove that the actors behind Black Basta are well-organized and well-resourced, and yet there has been no indications of Black Basta attempting to recruit affiliates or advertising as a RaaS on the usual darknet forums or crimeware marketplaces,” the researchers said.
“Our research indicates that the individuals behind Black Basta ransomware develop and maintain their own toolkit and either exclude affiliates or only collaborate with a limited and trusted set of affiliates, in similar ways to other ‘private’ ransomware groups such as Conti, TA505, and Evilcorp.”
SentinelLabs said it began tracking Black Basta in June, when it began infections involving the Qakbot malware. The malware is delivered by email in Microsoft Office documents and exploits CVE-2022-30190.
Black Basta was also seen using ZeroLogon (CVE-2020-1472), NoPac (CVE-2021-42287, CVE-2021-42278) and PrintNightmare (CVE-2021-34527).
Behind FIN7
FIN7 – previously known as Carbanak – has been operating dozens of cybercriminal efforts since 2012. The group started out using point-of-sale malware to run financial scams but switched to ransomware around 2020, with alleged connections to REvil, Conti, Darkside, BlackMatter.
SentinelOne said that the cybercriminal cartel likely “began writing tools from scratch in order to disassociate their new operations from the old.”
“The crimeware ecosystem is constantly expanding, changing, and evolving. FIN7 (or Carbanak) is often credited with innovating in the criminal space, taking attacks against banks and PoS systems to new heights beyond the schemes of their peers,” the researchers said.
“As we clarify the hand behind the elusive Black Basta ransomware operation, we aren’t surprised to see a familiar face behind this ambitious closed-door operation. While there are many new faces and diverse threats in the ransomware and double extortion space, we expect to see the existing professional criminal outfits putting their own spin on maximizing illicit profits in new ways.”
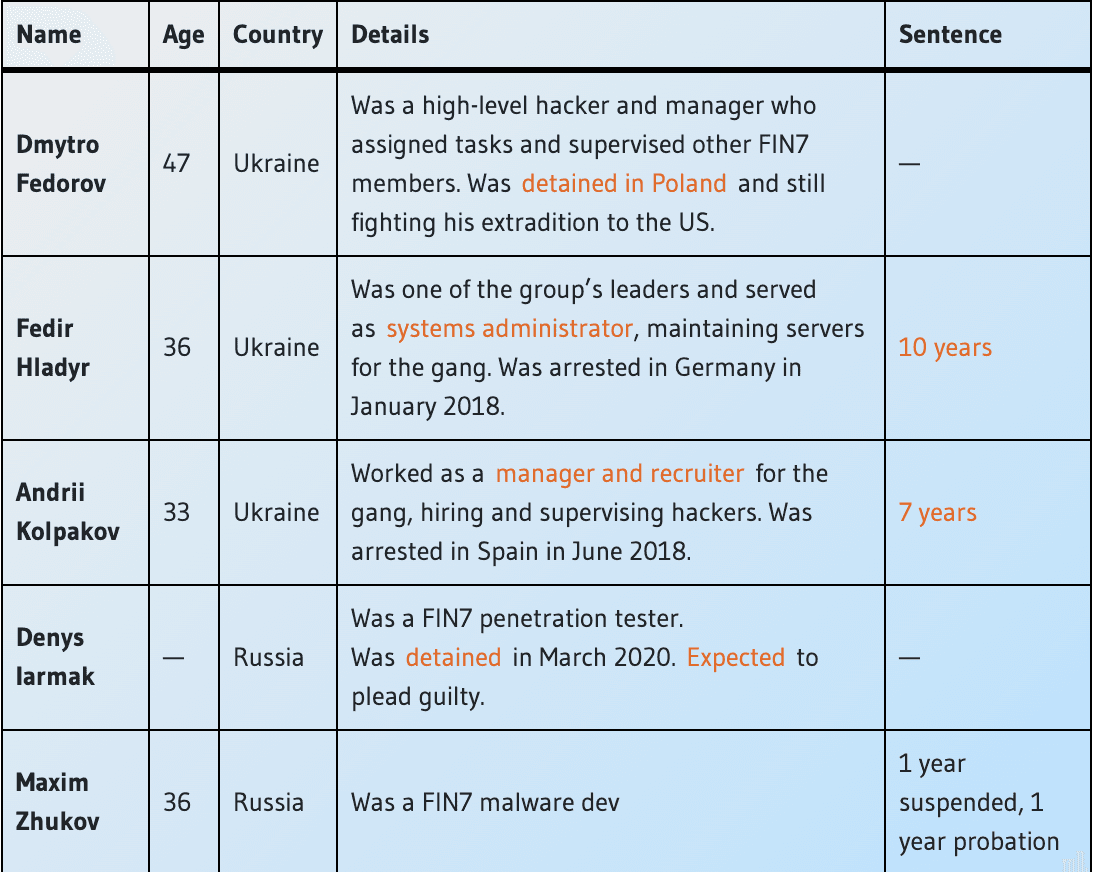
A key member of FIN7 was sentenced to 84 months in prison and ordered to pay $2.5 million in restitution in June 2021 and another was given a one-year suspended prison sentence by a Russian court in December 2021. At least five FIN7 members have been identified by law enforcement agencies.
FIN7 is accused of attacking more than 100 U.S. companies between 2015 and 2018 and orchestrated intrusions at tens of U.S. retailers, such as Chipotle Mexican Grill, Chili’s, Arby’s, Red Robin, and Jason’s Deli, where they deployed malware that collected millions of customer payment card details that they later sold on hacking forums.
Adam Flatley, director of threat intelligence at Redacted, told The Record that FIN7 has been partnering with multiple ransomware groups for years now.
But Flatley said what stood out most was not that Black Basta worked with FIN7. Instead, the report illustrated how FIN7 – which he said is “one of the most talented and capable cybercriminal gangs out there” – continues to enable less capable ransomware gangs to be more effective.
“They’re making the ransomware problem worse by continuing to bring their nearly nation-state level talent to the table as a force multiplier,” he said.
“Disrupting FIN7 operations needs to be a key part of any international counter-ransomware strategy.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



