FileWave patches two vulnerabilities that impacted more than 1,000 orgs
Swiss device management company FileWave confirmed on Tuesday that two vulnerabilities in their platform have been patched after being discovered by researchers from Claroty’s Team82.
The vulnerabilities – CVE-2022-34907 and CVE-2022-34906 – were found in FileWave’s mobile device management (MDM) system and affect thousands of companies that use the system.
Noam Mosche, a researcher for Claroty’s Team82, told The Record that it is common for any type of organization to use an MDM solution considering the large number of IoT devices in use today. The tools make it simpler for IT administrators to manage all of an organization’s devices effectively.
“In our research we discovered more than 1,100 FileWave MDM instances across multiple organizations, including large corporations, schools and educational institutions, government agencies, and small and medium businesses,” Mosche said.
FileWave’s MDM system allows IT departments to manage, monitor, and view all of an organization’s devices, ranging from iOS and Android smartphones, MacOS and Windows tablets to laptops and workstations, and smart devices such as televisions.
The vulnerabilities are remotely exploitable and allow an attacker to bypass authentication mechanisms and gain full control over the MDM platform and its managed devices.
CVE-2022-34907 is an authentication bypass flaw that exists in FileWave MDM before version 14.6.3 and 14.7.x, prior to 14.7.2. CVE-2022-34906, a hard-coded cryptographic key, exists in FileWave MDM prior to version 14.6.3 and 14.7.x, prior to 14.7.2.
Mosche compared the vulnerability to one that was recently discovered in F5 BIG-IP devices (CVE-2022-1388), which he said “caused a lot of headaches for many IT administrators.”
“Authentication bypass vulnerabilities, such as CVE-2022-34907, are unfortunately more common than many people realize,” Mosche said.
Claroty also compared the vulnerabilities to ones used by the REvil ransomware group during the headline-grabbing attack on Kaseya in July 2021 that spread ransomware to more than 1,500 organizations around the world.
“Furthermore, attackers could abuse legitimate MDM capabilities to install malicious packages or executables, and even gain access to the device directly through remote control protocols,” Claroty explained in its report.
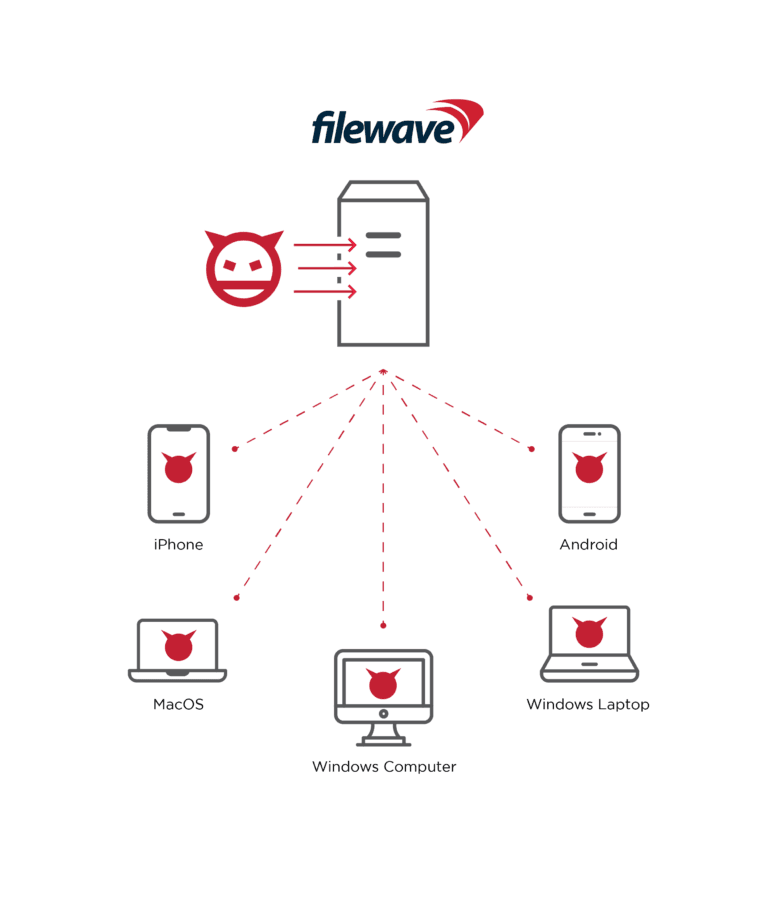
Management services like this provide attackers with wide-ranging control over an organization. Claroty said a hacker could use CVE-2022-34907 to not only take over all managed devices but also exfiltrate sensitive data like device serial numbers, user email addresses, geo-location coordinates, IP addresses, device PIN codes and more.
FileWave addressed the vulnerabilities in a recent update, according to a statement sent to The Record.
The security update released to address the vulnerabilities is included in the patched software upgrades of versions 14.6.3, 14.7.2, as well as in the latest software release 14.8, and all future subsequent versions, FileWave explained.
FileWave said it is not aware of any exploitation of the vulnerability, but recommended users to “double-check that the security update is properly installed and up to date to avoid the risk of third-party attacks going forward.”
The spokesperson added that all affected software users were first notified of the vulnerabilities by FileWave on 26th April 2022 and were provided with a software upgrade to address the vulnerabilities.
“The security vulnerabilities were carefully reviewed and confirmed in close cooperation with Claroty Research,” the company said.
“Immediately after the vulnerabilities became known, measures were taken to develop patched versions of the software, following a robust protocol to not only provide FileWave software users with a solution, but also to protect and help them understand the risks and install software upgrades on their servers in a timely manner.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



