FBI warns of credential stuffing attacks against grocery and food delivery services
The FBI says that hackers are using credential stuffing attacks to hijack online accounts at grocery stores, restaurants, and food delivery services in order to drain user funds through fraudulent orders and to steal personal or financial data.
The warning comes via an FBI Private Industry Notification the agency's Cyber Division sent last week to companies in the US food and agricultural sectors.
The agency said that cybercriminal groups are using username and password combos obtained through breaches at other companies to log into customer accounts at grocery and food delivery services, hoping that users had reused passwords across accounts.
These intrusions, known as credential stuffing attacks, are usually carried out using automated tools and proxy botnets in order to spread the attacks over a large pool of IP addresses and disguise the attackers' location.
With billions of user credentials having been leaked online following security breaches over the past decade, credential stuffing attacks are now common across a wide spectrum of industry verticals.
Because most grocery, restaurants, and food delivery accounts tend to run a reward points program and typically store payment card information, cybercrime groups started focusing their efforts on hijacking these types of accounts over the past year.
The FBI said it received reports of several incidents that have taken place since July 2020:
As of February 2021, an identified US-based food company suffered a credential stuffing attack that affected 303 accounts through customers' emails. The cyber actors used six of the compromised accounts to make purchases through the US-based company; however, the US-based company canceled and flagged one of the orders as fraudulent. The US-based company suffered a financial loss of $200,000 due to the fraudulent orders.In October 2020, customers of a restaurant chain reported orders fraudulently charged to their accounts as the result of a credential stuffing attack. The company reimbursed the customers for the fraudulent charges. Another restaurant chain experienced a credential stuffing attack in April 2019. Customers posted on social media that their payment cards had been used to pay for food orders placed at restaurants.In July 2020, the personal information of customers of a grocery delivery company was being sold on the dark web. The information from approximately 280,000 accounts included names, partial credit card numbers, and order history. The company received customer complaints about fraudulent orders and believed the activity was the result of credential stuffing.
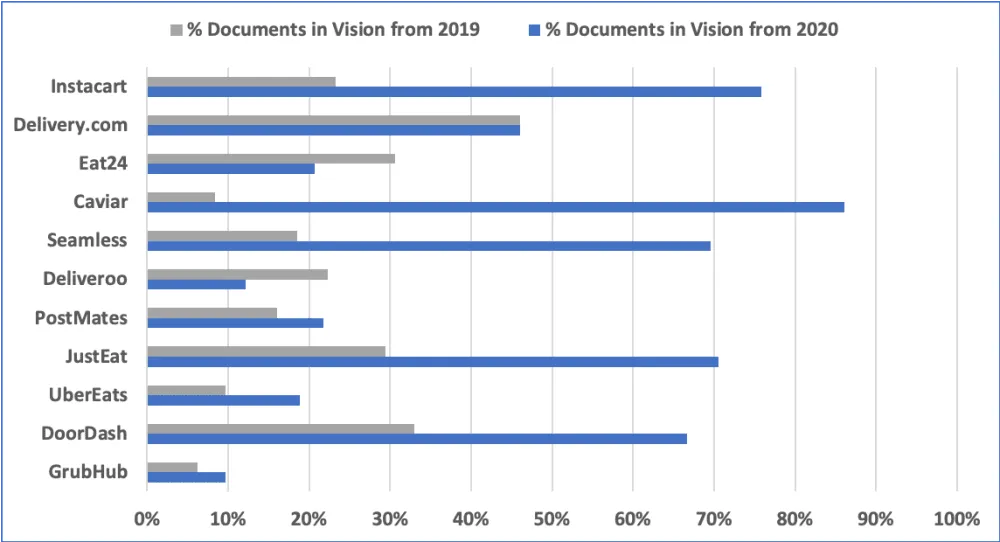
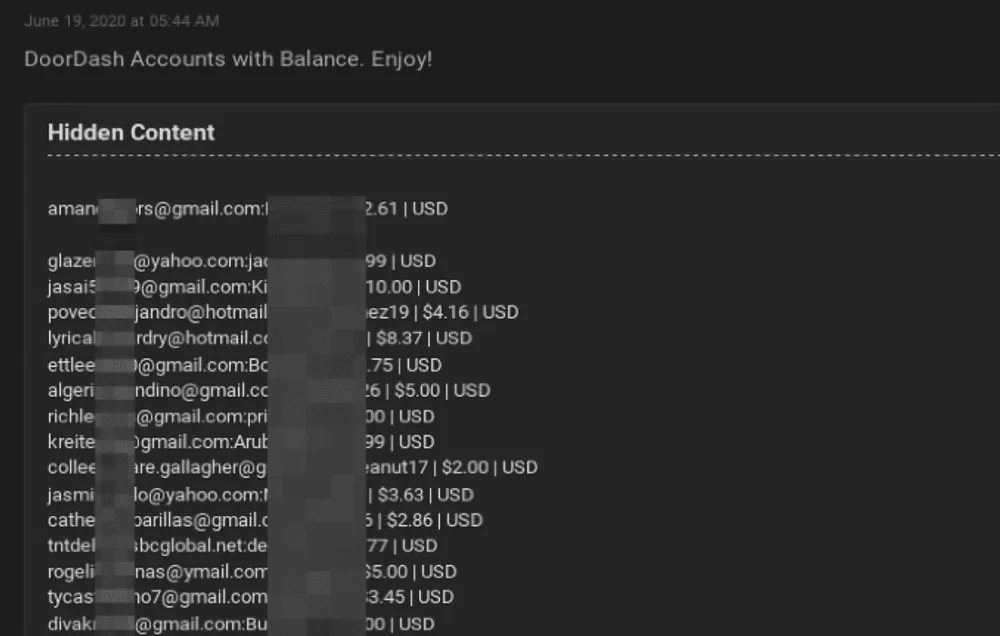
In addition, independent reporting from threat intelligence company DarkOwl also noted a rise in the number of underground ads offering access to restaurant and food delivery accounts, a spike that appears to have taken place since the onset of the COVID-19 pandemic in early 2020.
With more users now stuck in their homes and having to order online, the demand for food delivery accounts has risen as miscreants have sought to eat on someone else's dime.
The FBI said that in these incidents, and others, victim companies are often unaware of any compromises until customers complain of suspicious activities on their accounts, such as food orders for pick-ups that they didn't place.
While hackers can gain access to these types of accounts by breaching the online food ordering platforms itself—as it was recently the case—the FBI said that in most incidents, cybercriminals gained access to individual accounts through basic techniques like credential stuffing.
Now, the agency wants companies to improve their security defenses against these types of attacks. The FBI is now urging companies to keep on eye out on indicators of a credential stuffing attack and work on deploying a multi-layered mitigation strategy:
Indicators of a credential stuffing attack:
an unusually high number of failed logins, possibly in the millions, from a diverse range of IP addresses via the online account portal;a higher than usual lockout rate and/or an influx of customer calls regarding account lockouts and unauthorized changes;
Recommended mitigations:
Educate customers and employees about this scheme, advising them to use unique passwords for various accounts and to change passwords regularly.Advise customers to actively monitor their accounts for unauthorized access, modification, and anomalous activities; usernames and passwords should be changed upon identification of account compromise or fraud.Establish Two-Factor or Multi-Factor Authentication for creating and updating account information.Establish company policies to contact the owner of an account to verify any changes to existing account information. Use anomaly detection tools that identify an unusual increase in traffic and failed authentication attempts. To combat automated scripts or bots, consider deployment of a Completely Automated Public Turing test to tell Computers and Humans Apart (CAPTCHA), which requires users to confirm they are not running automated scripts by performing an action to prove they are human.Establish device fingerprinting and IP blacklisting policies.Use a PIN code and password together. The PIN code is a second piece of information the cyber actor would need to know, thus increasing the difficulty for unauthorized individuals to access the account.Monitor the dark web for lists of leaked user IDs and passwords, and perform tests to evaluate whether current user accounts are susceptible to credential stuffing attacks.
Other threats to be aware off
In addition, owners of hacked accounts should also be aware that if financial data was stored in their account and was unprotected, they might also need to check payment card balances and look into some form of identity fraud protection.
Furthermore, besides selling access to hacked accounts, DarkOwl also noted last year that some cybercriminals have also been making money by selling or freely sharing step-by-step guides on how to perform refund policy fraud.
Refund policy fraud is not a direct threat to end-consumers, but companies in the food delivery sector should be aware of these types of schemes as well, even if the FBI has not specifically warned against them.

The FBI's PIN alert last week marks the second time that the agency warns an industry vertical about a wave of credential stuffing attacks after it previously warned the banking and financial sector in September 2020.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.


