FBI sends out private industry alert about Mamba ransomware
The US Federal Bureau of Investigations has sent out this week a private industry notification to US organizations warning about attacks carried out by the Mamba ransomware gang, along with basic instructions about how organizations could recover from an attack if the intrusion was caught in its early stages.
In their alert [PDF] on Tuesday, FBI officials said the ransomware "has been deployed against local governments, public transportation agencies, legal services, technology services, industrial, commercial, manufacturing, and construction businesses."
But despite the recent warning, the Mamba ransomware is not new. The ransomware has been around since at least 2016, when it was first detected under the name of HDDCryptor.
First detailed in reports from Morphus Labs and Trend Micro, subsequent attacks were also spotted in 2017, 2019, and 2020, respectively.
However, while the ransomware received small updates across the years, its core principles remained the same — namely that it will first encrypt a victim's hard drive data, then move to rewrite the disk's MBR (Master Boot Record) section.
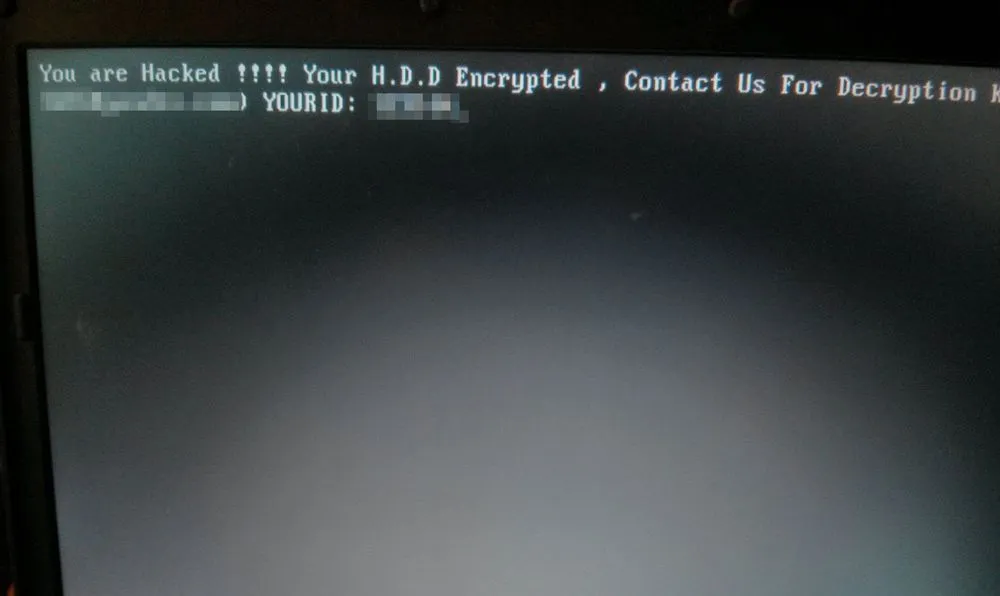
This latter step prevents infected computers from starting their operating system, trapping users in a pre-OS-boot screen showing the attacker's ransom demand.
Victims are then asked to contact the Mamba gang via email to negotiate a ransom payment and have their devices decrypted.
FBI: There might be a way to recover files
But the FBI alert sent out this week points to a weakness in the file encryption process, which the Mamba gang centered around DiskCryptor, a legitimate data encryption app, which it uses for encrypting files instead of its own custom code — like most ransomware strains tend to do.
Because DiskCryptor's encryption routines are well documented, the FBI points out in its advisory that there might be a way to recover the encryption key if an attack is caught in its early phases. The agency explains:
The ransomware program restarts the system about two minutes after installation of DiskCryptor to complete driver installation. The encryption key and the shutdown time variable are saved to the configuration file (myConf.txt) and is readable until the second restart about two hours later which concludes the encryption and displays the ransom note. If any of the DiskCryptor files are detected, attempts should be made to determine if the myConf.txt is still accessible. If so, then the password can be recovered without paying the ransom. This opportunity is limited to the point in which the system reboots for the second time.
Currently, it is unclear how widespread Mamba attacks really are. Ransomware attack statistics for 2020 published last week by security firm Emsisoft don't list Mamba as one of last year's top ransomware detections, suggesting that attacks are not on the same scale as attacks carried out by ransomware gangs such as STOP, Phobos, REvil, LockBit, and others.
Furthermore, attacks can't be tracked via the ID-Ransomware service because the ransomware prevents victims from booting their operating system, which means victims can't upload encrypted artifacts to ID-Ransomware for identification.
But even if the attacks are not on the same scale as other ransomware threats, the FBI alert sent this week should at least make companies aware that there might be a way to recover their files in case of an attack, something that the San Francisco municipal transport department was not aware in 2016 when its ticketing system went down due to a Mamba/HDDCrypter attack.
Apparently the SF Muni fell victim to ransomware last night #sanfrancisco #infosec pic.twitter.com/E1OVQpAAzY
— Colin Hellbut (@ColinHeilbut) November 26, 2016
FBI: Watch out for Pysa ransomware attacks too
The FBI's Mamba alert is also the second private industry notification (PIN) the agency sent out over the past week after it sent a first alert about the Pysa (Mespinoza) ransomware on March 16 [PDF].
FBI officials warned companies to deploy detection rules for Pysa payloads citing recent reports that this particular ransomware was used to attack education institutions in 12 US states and the United Kingdom.
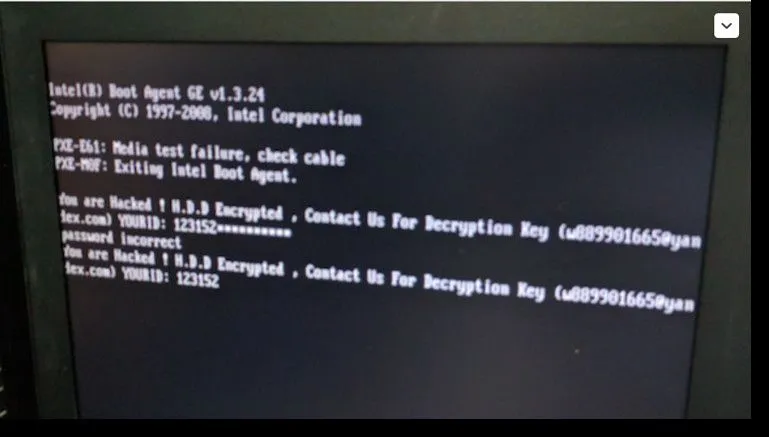
A similar warning was sent by the French government in March 2020, a year before, when the ransomware was first spotted being used across France. Since then, attacks have spread to other countries and have intensified, with a regular number of victims using the ID-Ransomware service to detect and identify Pysa attacks over the past few months.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.