FBI, NSA: Russian military cyber-unit behind large-scale brute-force attacks
US and UK cybersecurity agencies said today that a Russian military cyber unit has been behind a series of brute-force attacks that have targeted the cloud IT resources of government and private sector companies across the world.
The attacks have been linked to a hacking group tracked as APT28, or Fancy Bear, in a series of joint security advisories published today by the US National Security Agency (NSA), the US Cybersecurity and Infrastructure Security Agency (CISA), the US Federal Bureau of Investigation (FBI), and the UK's National Cyber Security Centre (NCSC).
Since at least mid-2019 through early 2021, Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS), military unit 26165, used a Kubernetes cluster to conduct widespread, distributed, and anonymized brute force access attempts against hundreds of government and private sector targets worldwide.
[...]
The 85th GTsSS directed a significant amount of this activity at organizations using Microsoft Office 365 cloud services; however, they also targeted other service providers and on-premises email servers using a variety of different protocols. These efforts are almost certainly still ongoing.
The four security agencies said that the brute-force attacks are only the beginning of an APT28 attack.
The agencies said the GRU hackers utilized the successfully compromised accounts to pivot internally inside the hacked organizations.
In particular, the agencies said that APT28 used the compromised account credentials in conjunction with exploits for Microsoft Exchange servers like CVE-2020-0688 and CVE-2020-17144, combining the two to gain access to internal email servers.
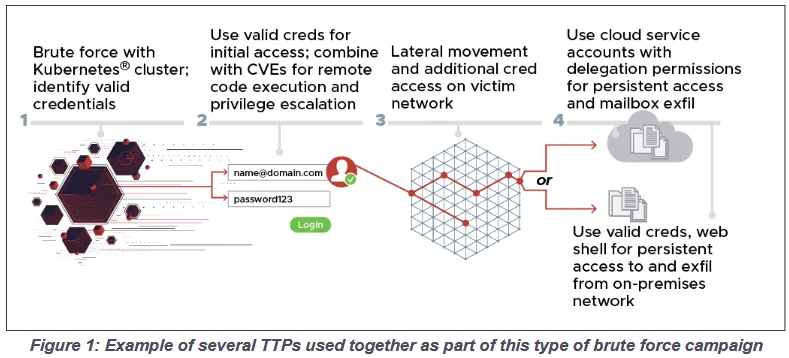
CISA, FBI, NSA, and NCSC officials said the group's attacks had remained largely under the radar because APT28 worked to disguise its brute-forcing attempts via the Tor network or commercial VPN services, such as CactusVPN, IPVanish, NordVPN, ProtonVPN, Surfshark, and WorldVPN.
These brute-force attacks were also carried out via a variety of protocols, such as HTTP(S), IMAP(S), POP3, and NTLM, so they weren't always coming via the same channels.
In addition, in a September 2020 report, Microsoft, which first discovered this new APT28 tactic, also added that while some attacks were carried out at scale, going after tens of thousands of accounts at more than 200 organizations, APT28 also took great care to distance the brute-force attempts far apart from each other and spread them across different IP address blocks, in order to prevent triggering anti-brute-force solutions.
The joint security advisory published today includes some of the IP addresses and user-agent strings used in these low-and-slow APT28 brute-force attacks that have been going on since 2019, so companies can deploy detections and countermeasures.
APT28 brute-force targets spread across multiple verticals
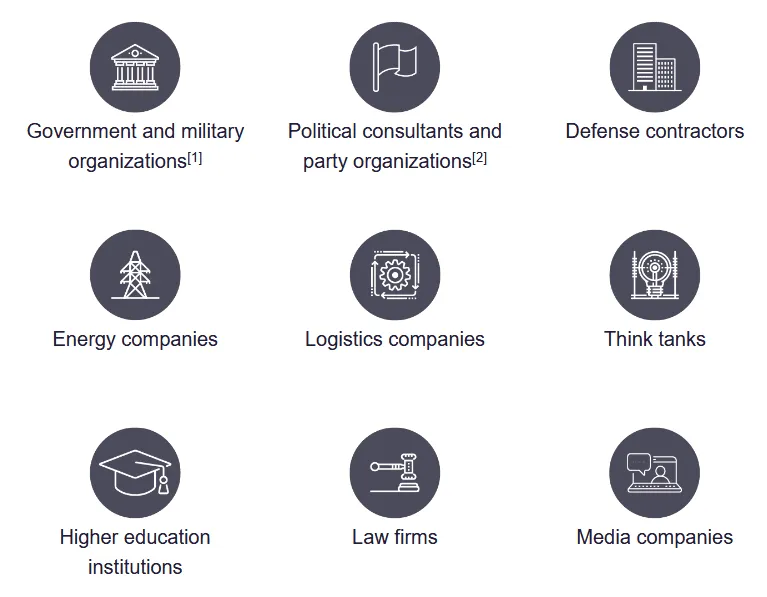
Per the four cybersecurity agencies, APT28's attacks have targeted the cloud resources of a wide array of targets, including government organizations, think tanks, defense contractors, energy companies, and more.
"This lengthy brute force campaign to collect and exfiltrate data, access credentials and more, is likely ongoing, on a global scale," Rob Joyce, NSA Director of Cybersecurity, said today.
"Net defenders should use multi-factor authentication and the additional mitigations in the advisory to counter this activity."
A downloadable PDF copy of the joint security advisory can be found here.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



