FBI and Australian police ran an encrypted chat platform to catch criminal gangs
The FBI and Australian Federal Police ran an encrypted chat platform and intercepted secret messages between criminal gang members from all over the world for more than three years.
Named Operation Ironside (AFP) / Trojan Shield (FBI, Interpol) on Monday, law enforcement agencies from Australia, Europe, and the US conducted house searches and arrested thousands of suspects across a wide spectrum of criminal groups, from biker gangs in Australia to drug cartels across Asia and South America, and weapons and human traffickers in Europe.
In a press conference today, Australian police said the sting operation got underway in 2018 after the FBI successfully seized encrypted chat platform Phantom Secure.
Knowing that the criminal underworld would move to a new platform, US and Australian officials decided to run their own service on top of Anøm (also stylized as AN0M), an encrypted chat platform that the FBI had secretly gained access to through an insider.
Just like Phantom Secure, the new service consisted of secure smartphones that were configured to run only the An0m app and nothing else.

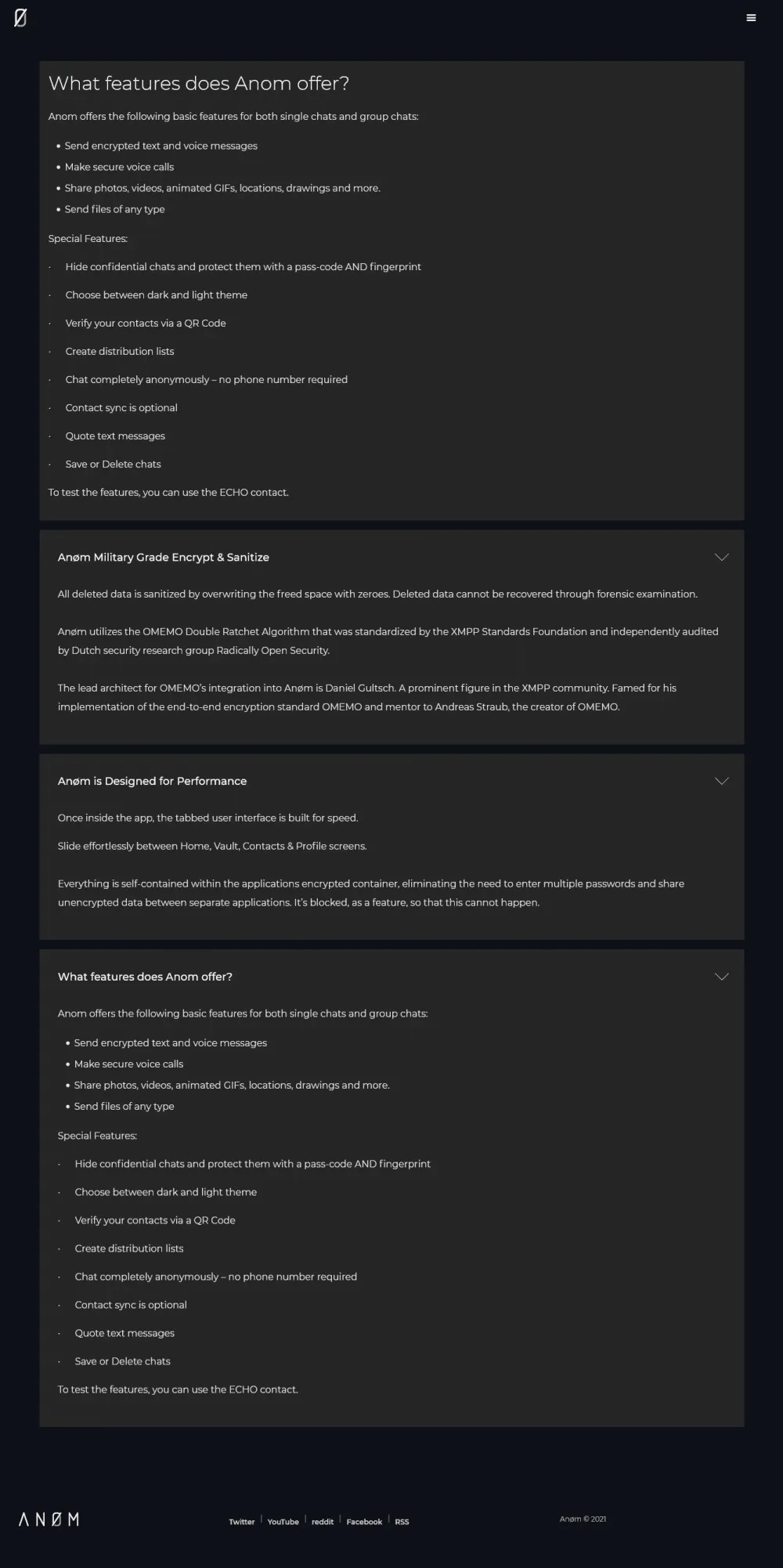
The app, advertised through word of mouth and via the anom.io website, allowed phone owners to send encrypted text and voice messages between devices and prevented them from running other services or installing other apps that would leak their identities.
All data on the device was encrypted, and no phone number was required to use the app, which relayed all its messages via An0m's central platform.
But according to investigators and court documents filed on Monday [PDF], the An0m insider provided access to the FBI, which was able to set up a man-in-the-middle scheme that allowed it to receive copies of all messages sent through the platform since October 2018.
Per the court documents, all An0m devices located outside the US were configured to send a blind carbon copy (BCC) of all their messages to a third-party XMPP bot, which the FBI called iBot.
Here, the bot would decrypt the messages and then re-encrypt them using encryption keys managed by the FBI.
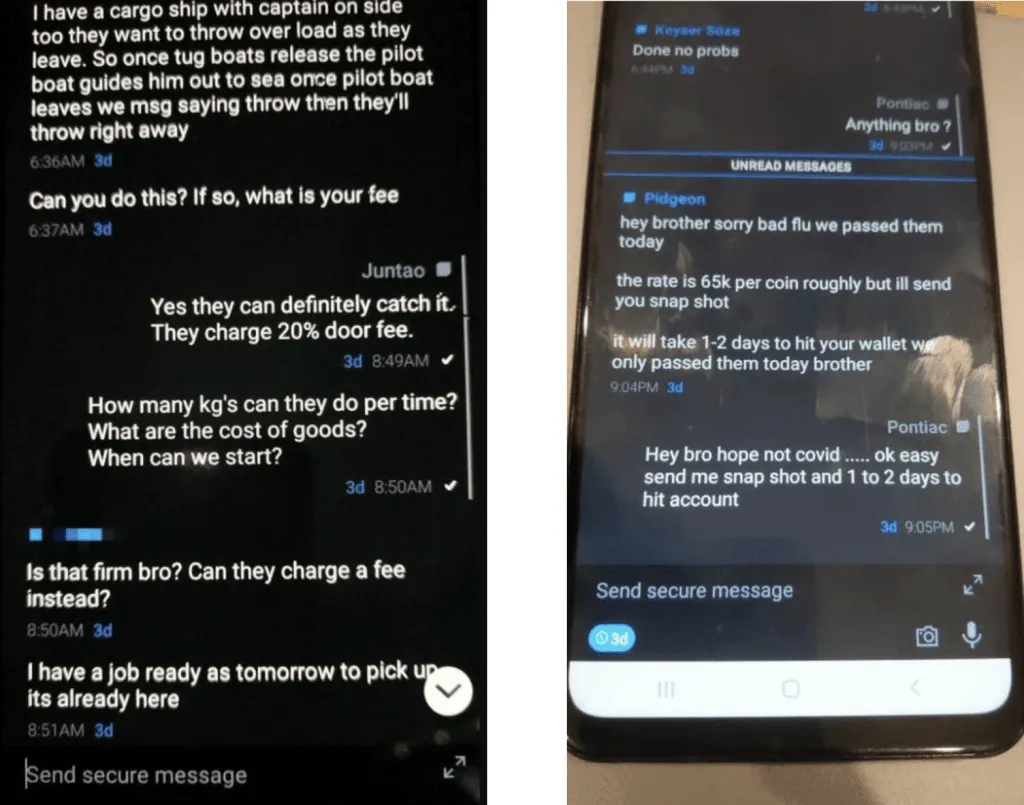
This design allowed the FBI to intercept the messages and decrypt texts sent by gang members to each other, many of which included details of drug movements or murder plots.
But while the FBI had set up the scheme, it was mostly Australian authorities who reviewed these messages, due to jurisdiction issues, as it was easier for AFP officials to obtain all the necessary paperwork, and then pass the information to the US three times a week. Per court documents, the scheme was so successful that a third unnamed country, believed to be in the EU, hosted another iBot server and helped sift through more than 26 million encrypted messages.
Officials initially relied on undercover agents to promote the An0m devices, but as law enforcement agencies shut down competing platforms, such as EncroChat and Sky ECC, criminal gangs found refuge on the network, which eventually amassed more than 12,000 users from 300+ criminal syndicates across 100+ countries.
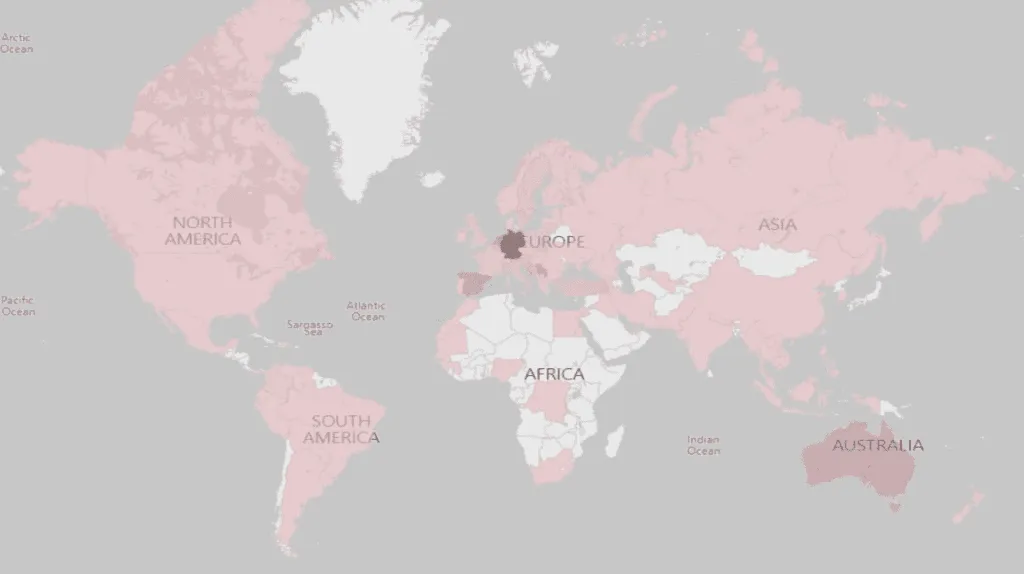
All in all, investigators described Operation Ironside as one of the largest sting operations in law enforcement history.
Per court documents, investigators shut down the sting operation after their interception warrant expired on June 7, on Monday, but it appears that some criminal groups caught on that the An0m app was leaking their conversations to third party XMPP servers earlier this year, in March.
On 21st March 2021, a (now deleted) blog post correctly identified that Anøm @anomsecure was in fact sending all the user messages to US-based LE. Criminals had caught onto the game as the arrests began. It can be viewed here in Google's cache. https://t.co/ck7bxun7la
— hackerfantastic.crypto (@hackerfantastic) June 7, 2021
Below is the AFP's Operation Ironside press conference in full.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.