Faulty emailing tool prevented Accellion from notifying customers of attacks
Efforts to patch a zero-day vulnerability in Accellion file-sharing servers that was actively exploited by hackers last year were hindered by a faulty emailing tool that delayed crucial customer notifications for days, allowing the attackers to wreak havoc among Accellion devices.
The attacks, which began on December 16, last year, targeted Accellion FTA, a web-based file-sharing solution that companies usually install on their premises to allow employees and customers to host and share large files that can't be sent via email.
Accellion released patches for the exploited vulnerabilities last year, days after learning of the ongoing hacks.
According to a timeline compiled by security firm FireEye [PDF], which Accellion hired to investigate the attacks, patches were made available on December 20 and again on December 23.
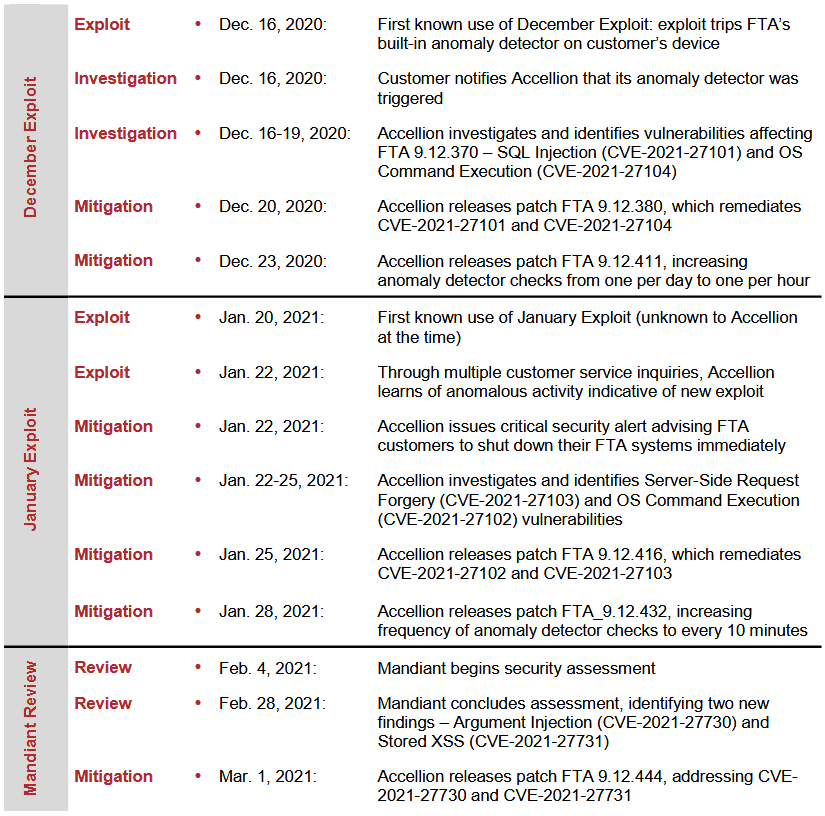
However, in a report [PDF] published on Monday by the Reserve Bank of New Zealand, one of the companies that had its FTA device hacked, the organization said that while Accellion released patches, its staff did not receive any notification.
Software updates to address the issue were released by the vendor in December 2020 soon after it discovered the vulnerability. The email tool used by the vendor, however, failed to send the email notifications, and consequently the Bank was not notified until January 6, 2021.
While the bank said it applied Accellion's patches a day later, on January 7, by that time, the attackers already had weeks at their disposal to break into the institution's FTA server and steal sensitive information.
Auditing firm KPMG, which compiled the RBNZ hack post-mortem report, argued that the lack of a timely notification contributed to the hack and the way the bank could have reacted to prevent the intrusion.
Email tool failure explains successful hacking campaign
With the emailing tool failing, very few Accellion customers knew that a patch was available for their FTA appliance and left their devices unpatched before taking time off during the winter holidays.
The KPMG finding sheds some light for companies still investigating their own hacks and which found about the FTA attacks from the press in early January.
This includes names such as the Australian Securities and Investments Commission (ASIC), law firm Allens, the University of Colorado, the Washington State Auditor Office, the QIMR Berghofer Medical Research Institute, Singapore telco Singtel, security firm Qualys, US-based Flagstar Bank, airplane maker Bombardier, and US retail store chain Kroger.
Accellion estimated the number of companies hacked via FTA zero-days in the realm of tens.
Security firm FireEye later discovered that the Accellion hackers partnered with the Cl0p ransomware gang and tried to extort FTA owners for ransom payments. Companies that didn't pay had their data dumped on a website operated by the Cl0p gang on the dark web.
As is shown in the timeline above, the threat actors also discovered additional Accellion FTA zero-days, which they exploited for subsequent attacks.
Following the repeated bugs and exploitation, Accellion retired its FTA appliance on April 30 [PDF].
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



