On the sixth day of Christmas, an X account gave to me: a fake 7-Zip ACE
A social media user with what we assume is the inauthentic handle of @NSA_Employee39 claimed on Monday to have dropped a zero-day vulnerability for the popular, free and open-source file archive software 7-Zip.
In a post on X, the user’s verified account said it would be “dropping 0days all this week” to thank his new followers, which number just over 1,400 in total.
The first of these, they said, was an arbitrary code execution (ACE) vulnerability in 7-Zip — a vulnerability that would allow an attacker to run any code they wanted on the victim device — demonstrated by what the user claimed was exploit code uploaded to Pastebin.
The comments preceding the 90-odd lines of curious code describe it as using “a crafted .7z archive with a malformed LZMA stream to trigger a buffer overflow condition in the RC_NORM function.”
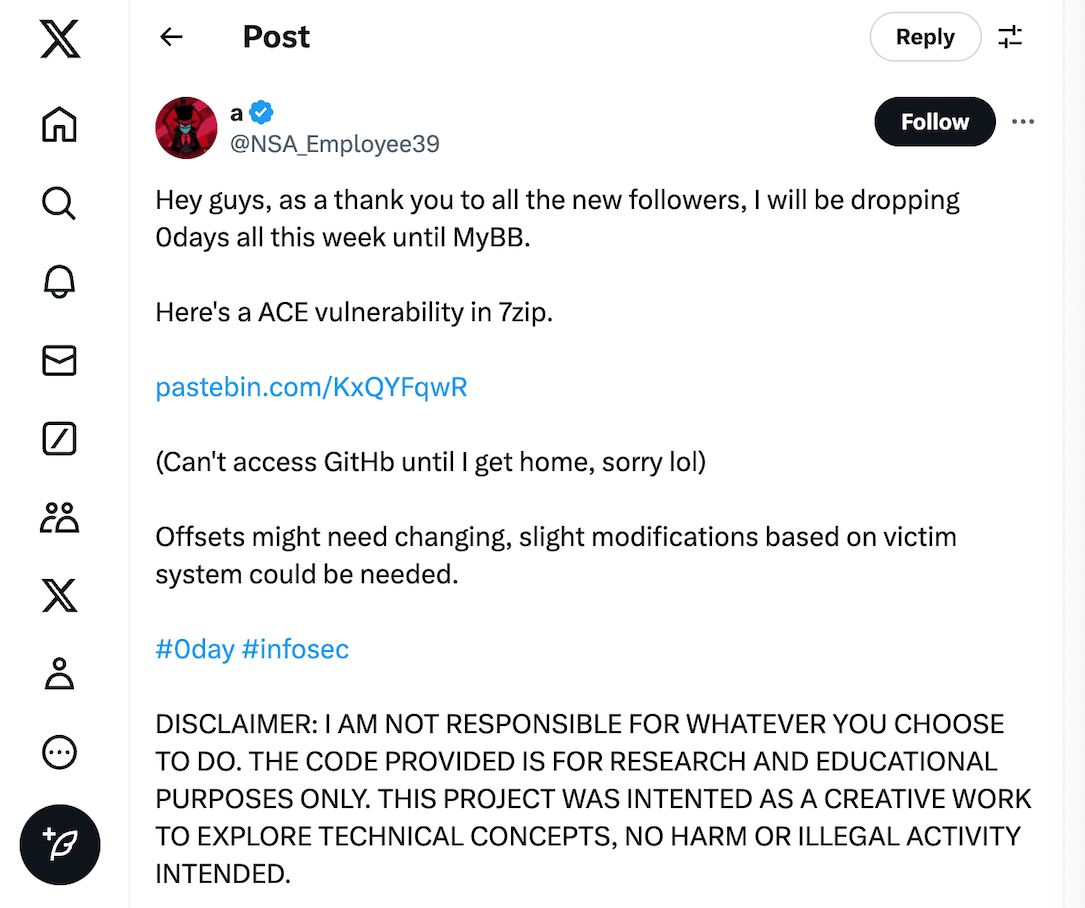
Despite the immediate excitement, however, nobody has been able to get the exploit code to work — or even resemble an actual exploit. As one security expert kindly responded: “Maybe I just suck but I don’t think this is real.”
Igor Pavlov, the developer behind 7-Zip, was less generous, telling the 7-Zip discussion forum’s bugs section: “This report on Twitter is fake. And I don’t understand why this Twitter user did this. There is no such ACE vulnerability in 7-Zip / LZMA.”
The @NSA_Employee39 account did not immediately respond to a request for comment on social media.
Perhaps more confusing than releasing a fake 7-Zip vulnerability at all is doing so on the sixth rather than seventh day of Christmas. But loneliness is a common experience for many during the holiday period, and if you’re suffering, there are ways to get help.
Alexander Martin
is the UK Editor for Recorded Future News. He was previously a technology reporter for Sky News and a fellow at the European Cyber Conflict Research Initiative, now Virtual Routes. He can be reached securely using Signal on: AlexanderMartin.79



