Facebook takes down accounts for seven "cyber-mercenary" firms
Meta (formerly Facebook) said today that it suspended accounts on its Facebook and Instagram platforms operated by seven companies that provide surveillance and cyber-mercenary services.
Meta said these companies targeted users with links to phishing sites and malware in order to collect login credentials and infect them with malware.
The seven companies, which have been active for years, sold their services "indiscriminately to any customer," Meta said in a press release today.
While the companies advertised their services as meant for law enforcement, Meta said that many of the victims they targeted were in reality journalists, dissidents, critics of authoritarian regimes, and the families of opposition and human rights activists.
In total, Meta said the seven companies used more than 1,500 fake accounts to target more than 50,000 users across 100 countries on behalf of their customers.
Besides suspending their Facebook and Instagram accounts, Meta said it also notified law enforcement, other security researchers, and policy makers. In addition, Meta said it also took legal action against six of the seven, and sent cease & desist letters as the last warning before filing a full-on lawsuit, as Facebook did against NSO Group in 2019.
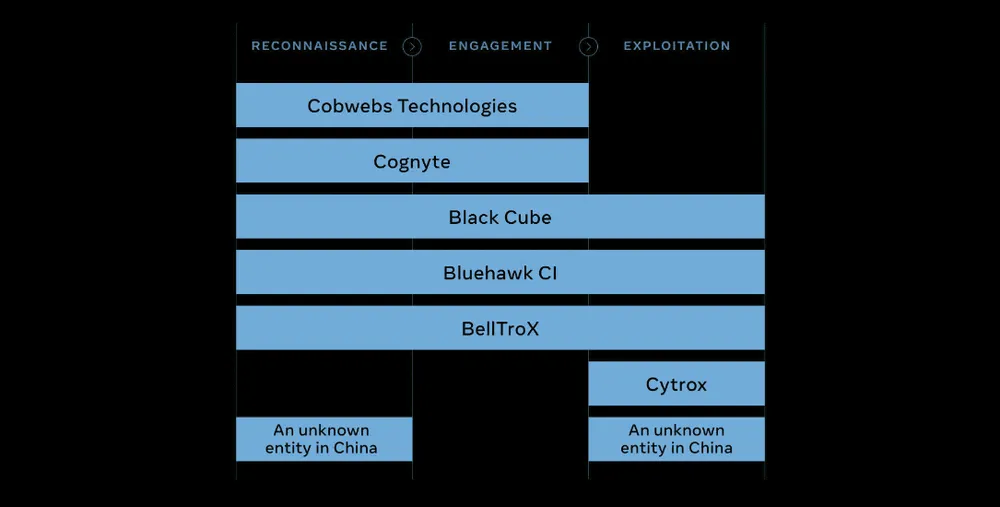
The seven surveillance-for-hire companies are listed below, along with the reasons Meta suspended their accounts, as described in a 17-page report published by the company's security team today.
Cobwebs Technologies (Israel, 200 accounts) - This firm was founded in Israel with offices in the United States and sells access to its platform that enables reconnaissance across the internet, including Facebook, Instagram, WhatsApp, Twitter, Flickr, public websites and "dark web" sites. In addition to collecting information about their targets, the accounts used by Cobwebs customers also engaged in social engineering to join closed communities and forums and trick people into revealing personal information. Meta's investigation identified customers in Bangladesh, Hong Kong, the United States, New Zealand, Mexico, Saudi Arabia, Poland, and other countries. In addition to targeting related to law enforcement activities, we also observed frequent targeting of activists, opposition politicians and government officials in Hong Kong and Mexico.
Cognyte (formerly WebintPro, Israel, 100 accounts) - This firm is based in Israel and sells access to its platform which enables managing fake accounts across social media platforms including Facebook, Instagram, Twitter, YouTube, and VKontakte (VK), and other websites to social-engineer people and collect data. Our investigation identified customers in Israel, Serbia, Colombia, Kenya, Morocco, Mexico, Jordan, Thailand, and Indonesia. Their targets included journalists and politicians around the world.
Black Cube (Israel, 300 accounts) - An Israeli-based firm with offices in the UK, Israel and Spain. It provides surveillance services that include social engineering and intelligence gathering. Black Cube operated fictitious personas tailored for its targets: some of them posed as graduate students, NGO and human rights workers, and film and TV producers. They would then attempt to set up calls and obtain the target's personal email address, likely for later phishing attacks. Black Cube relied on different tactics to obfuscate its activity, including by performing unrelated activities, likely to drown out malicious targeting in the "noise" of the seemingly innocuous social media behavior. Meta's investigation found a wide range of customers, including private individuals, businesses, and law firms around the world. Targeting by Black Cube on behalf of its customers was also widespread geographically and across industries, including the medical, mining, minerals and energy industries. It also included NGOs in Africa, Eastern Europe, and South America, as well as Palestinian activists. They also targeted people in Russia associated with universities, the telecom, high tech, consulting, legal, and financial industries, real estate development and media.
Bluehawk CI (Israel, 100 accounts) - a firm based in Israel with offices in the UK and the US. We collaborated on this investigation with Meta said it collaborated with The Daily Beast, who had identified a subset of this activity leading us to uncover the full cluster and who's behind it earlier this year. Bluehawk sells a wide range of surveillance-for-hire activities that included social engineering, gathering of litigation-related intelligence about people, and managing fake accounts to trick them into installing malware. The individuals behind this firm showed persistence and continued to try to come back to our platform after we took down dozens of their accounts. These fake accounts posed as journalists working for existing media organizations like La Stampa in Italy and Fox News in the US to trick their targets into giving an on-camera interview.
BellTroX (India, 400 accounts) - BellTroX is based in India and sells what's known as "hacking for hire" services, which were reported on by researchers at the Citizen Lab and Reuters. Its activity on Facebook was limited and sporadic between 2013 to 2019, after which it paused. BellTroX operated fake accounts to impersonate a politician and pose as journalists and environmental activists in an attempt to social-engineer its targets to solicit information including their email addresses, likely for phishing attacks at a later stage. This activity, based on the exact same playbook, re-started in 2021 with a small number of accounts impersonating journalists and media personalities to send phishing links and solicit the targets' email addresses. Among those targeted were lawyers, doctors, activists, and members of the clergy in countries including Australia, Angola, Saudi Arabia, and Iceland.
Cytrox (North Macedonia, 300 accounts) - This North Macedonian company develops exploits and sells surveillance tools and malware that enable its clients to compromise iOS and Android devices. Meta worked together with Citizen Lab on identifying this company's network of phishing domains. Cytrox and its customers took steps to tailor their attacks for particular targets by only infecting people with malware when they passed certain technical checks, including IP address and device type. If the checks failed, people could be redirected to legitimate news or other websites. Meta said that Cytrox appears to have sold its services to a threat actor known as Sphinx, which targeted people in Egypt and its neighboring countries. Other targets were located in rmenia, Greece, Saudi Arabia, Oman, Colombia, Côte d'Ivoire, Vietnam, the Philippines, and Germany.
Unnamed company (China, 100 accounts) - Meta said this "entity" developed surveillanceware for Android, iOS, Windows, and also Linux, Mac OS X, and Solaris operating systems. Evidence suggested the threat actor suggests these tools were used by China's domestic law enforcement agencies. In some instances, Meta found this group's malware framework deployed along with facial recognition software developed by a Beijing-based company. Access to this framework was protected by username, password, and a SafeNet SuperDog physical hardware key. The investigation found that malware tools were used to support surveillance against minority groups throughout the Asia-Pacific region, including in the Xinjiang region of China, Myanmar, and Hong Kong.
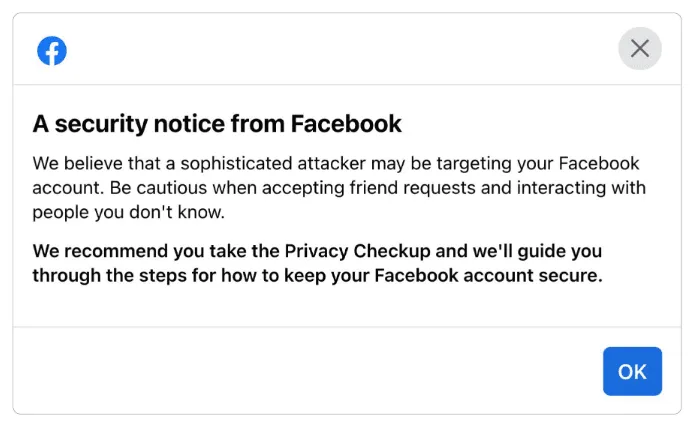
Meta said that users who might have received messages and URLs from these groups would receive a message like the one below, notifying them that they've been targeted.
"We will continue to investigate and enforce against anyone abusing our apps," Meta said today. "However, these cyber mercenaries work across many platforms and national boundaries. Their capabilities are used by both nation-states and private enterprises, and effectively lower the barrier to entry for anyone willing to pay."
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.