Facebook disrupts two nation-state groups operating out of Palestine
The Facebook security team announced today that it disrupted the activities of two state-sponsored hacking groups operating out of Palestine that abused its platform to infect users with malware.
Facebook said it tracked the first of these groups to members of the Palestinian Preventive Security Service (PSS) and the second group to a well-known cyber-espionage outfit known as Arid Viper.
The first group targeted domestic audiences inside Palestine in what looked like a domestic surveillance operation orchestrated by the country's intelligence service, while the second group operated from inside Palestine but also went after targets outside the country.
Facebook said that while the two groups used different malware strains and attack techniques, the end goal was the same—namely, to use Facebook accounts and posts to lure their targets on malicious sites hosting malware, usually packaged as a benign-looking desktop or mobile application.
"To disrupt both these operations, we took down their accounts, released malware hashes, blocked domains associated with their activity and alerted people who we believe were targeted by these groups to help them secure their accounts," Mike Dvilyanski, Head of Cyber Espionage Investigations, and David Agranovich, Director, Threat Disruption said in a press release today.
PSS group activity
As for what each group was doing, Facebook said the PSS-linked threat actor was the least sophisticated of the two.
The group used "low-sophisticated" tools for their attacks. This included a custom-built Android spyware strain and, on some occasions, publicly available Windows malware.
The PSS group operated by creating fake Facebook profiles posing as young women, reporters, or Hamas supporters, which they used to approach their targets and lure them into installing malware-laced chat apps.
Facebook said the group primarily targeted journalists, people opposing the Fatah-led government, human rights activists, and military targets, including individuals from the Syrian opposition and Iraqi military.
To the best of our knowledge, this is the first public reporting of this PSS activity
Mike Dvilyanski, Head of Cyber Espionage Investigations, and David Agranovich, Director, Threat Disruption
Arid Viper activity
But while the first group operated on a small scale and used low-level tools, the second group was far more active and much more sophisticated.
In a 40-page report [PDF] detailing this group's activity, Facebook said it tracked Arid Viper abusing its platform as far back as August 2019.
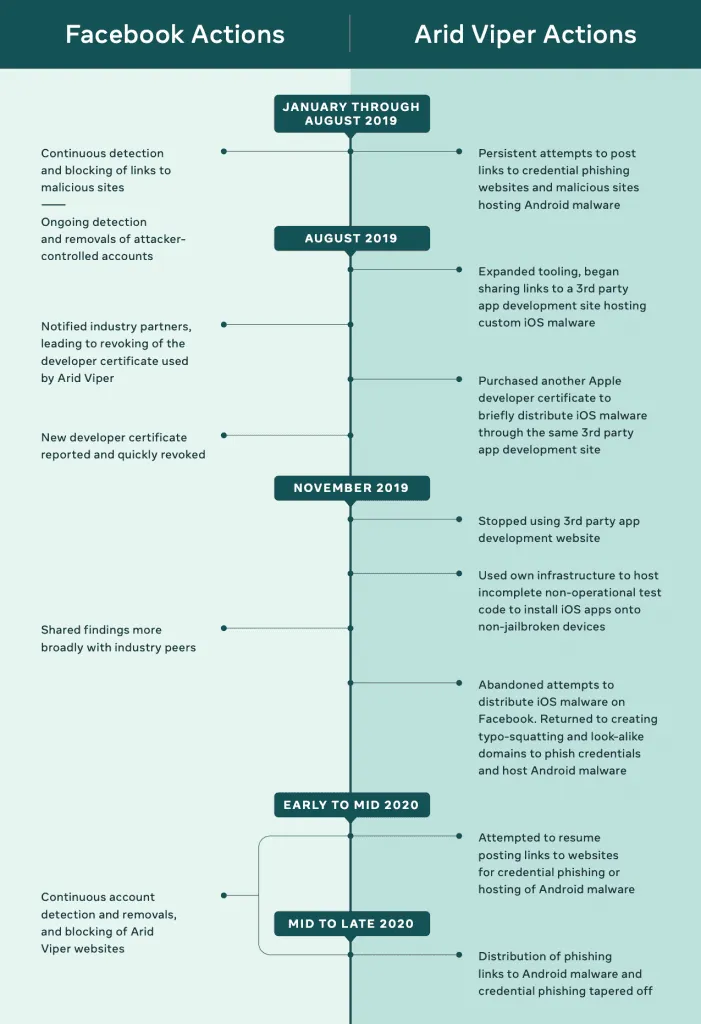
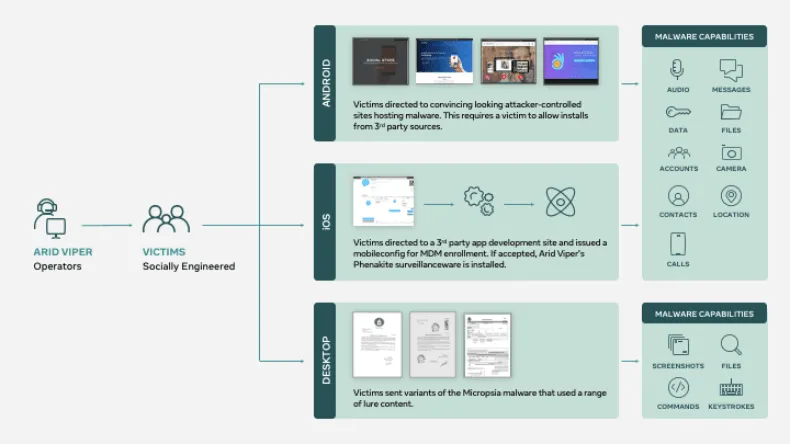
Furthermore, Facebook also said the group used advanced malware and was capable of attacking users across Windows, iOS, and Android environments.
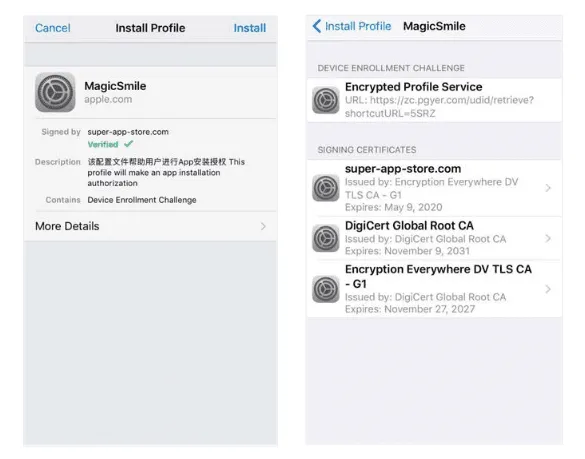
The malware was custom-built, and Facebook's security team said it even discovered a new iOS toolkit, which they named Phenakite, which hasn't been seen in any previous attacks before.
According to Facebook, Phenakite worked by social-engineering victims into installing a mobile configuration profile on their device, which allowed the malware to collect data from infected systems and send it back to the attacker's server.
Facebook says that just like the PSS-linked group, Arid Viper operated out of Palestine and targeted the Palestinian community, but also individuals living in Syria, Turkey, Iraq, Lebanon, and Libya.
Despite operating since 2015, neither Facebook nor other security firms who studied this group's activities haven't been able to link it to a specific real-world entity until today.
In total, Facebook said it identified ten Android malware strains, two iOS malware hashes, eight desktop malware strains, and 179 domains used by Arid Viper in attacks that were carried out via Facebook accounts and other services.
Both groups expected to resume operations with new infra
Dvilyanski and Agranovich said that despite their actions today, Facebook described the two groups as "persistent," and they expect both operators to create new accounts, malware strains and set up new domains and servers to launch new attacks.
"Our hope is that by sharing insights into these attacks, the increased awareness will allow those directly impacted by these attacks to avoid device compromise, that security teams will have a better understanding of the possible attack vectors that can take place against their organization's mobile fleet and that these new signals will allow the larger security community to track this persistent threat actor," Facebook said.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



