Experts warn of widespread exploitation involving Hikvision cameras
Both government and criminal hacking groups are still targeting Hikvision cameras with a vulnerability from 2021, according to reports from several security researchers.
Cybersecurity firm CYFIRMA released a report this week saying Russian cybercriminal forums are awash with hackers looking to collaborate on exploiting Hikvision cameras using the command injection vulnerability CVE-2021-36260.
“Specifically in the Russian forums, we have observed leaked credentials of Hikvision camera products available for sale,” the company’s researchers said.
“These can be leveraged by hackers to gain access to the devices and exploit further the path of attack to target an organization's environment.”
CYFIRMA reported they found that more than 80,000 Hikvision cameras are still vulnerable to the critical command injection flaw, which carries a CVSS score of 9.8 out of 10.
Of the more than 80,000 vulnerable cameras, more than 100 nations and 2,300 organizations are impacted.
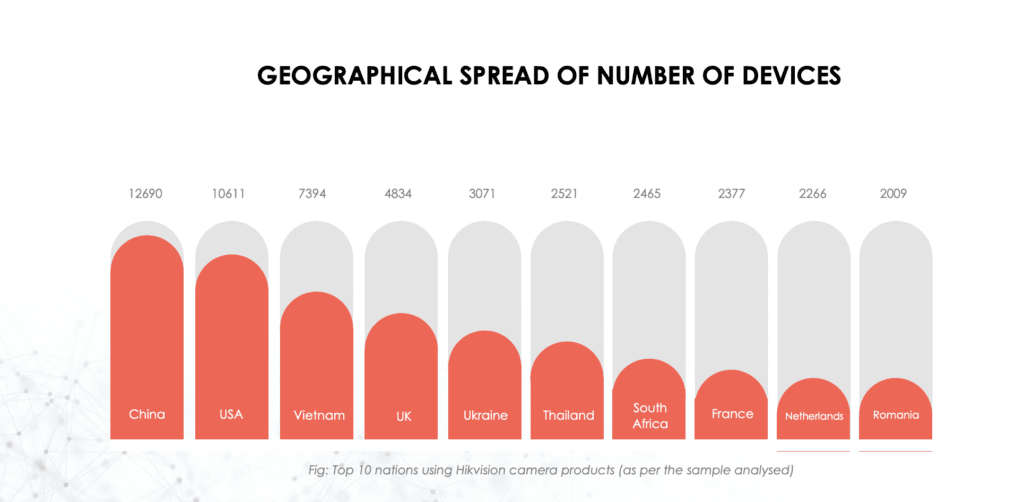
Credit: CYFIRMA
Nearly 12,700 vulnerable Hikvision camera products are located in China, followed by 10,611 in the U.S. and more than 7,300 in Vietnam.
The U.K., Ukraine, Thailand, South Africa, France, the Netherlands and Romania also topped the list of the countries with the most vulnerable Hikvision cameras.
The Chinese state-owned manufacturer provides video surveillance equipment for civilian and military purposes.
The company patched CVE-2021-36260 in an update released in September 2021. But multiple exploits for the bug have been released publicly since then.
CYFIRMA noted that it is difficult to pinpoint the attackers using it because a wide variety of groups are abusing the bug.
Several security experts backed up CYFIRMA’s findings, noting that cybercriminals on multiple forums are discussing the vulnerability and its exploitation.
2/ Almost on all private as well as public forums, you can find threat actors selling lists of the vulnerable Hikvision CCTV Cameras.
On Shodan there are over 5 million indexable cameras (many of which are vulnerable).
Kindly update your firmware if you using Hickvision Cameras. pic.twitter.com/HXSLT1oeke— Sunny Nehra (@sunnynehrabro) August 23, 2022
In December, Fortinet researchers said they "observed numerous payloads attempting to leverage this vulnerability to probing the status of devices or extracting sensitive data from victims."
"One payload in particular caught our attention. It tries to drop a downloader that exhibits infection behavior and that also executes Moobot, which is a DDoS botnet based on Mirai," the company said at the time.
The Cybersecurity and Infrastructure Security Agency (CISA) added the bug to its list of known exploited vulnerabilities in January, ordering federal civilian agencies to patch it by the end of the month.
David Maynor, senior director of threat intelligence at Cybrary, said wireless cameras have been a highly sought-after target for attackers over the past several years, particularly Hikvision cameras.
“Their product contains easy to exploit systemic vulnerabilities or worse, uses default credentials. There is no good way to perform forensics or verify that an attacker has been excised,” he said.
“Furthermore, we have not observed any change in Hikvision’s posture to signal an increase in security within their development cycle.”
Last year, Hikvision resigned from the Security Industry Association (SIA), the largest trade organization for surveillance vendors, after being accused of working with the Chinese Army on research to improve the ‘lethality’ of missiles.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



