Experts warn of hacker claiming access to 50 U.S. companies through breached MSP
Cybersecurity experts are raising concerns about an individual on a hacker forum claiming to have access to 50 American companies through an unnamed managed service provider (MSP).
MSPs are paid to manage IT infrastructure and provide support, typically by smaller organizations lacking their own IT departments. In recent years they have been singled out by cybersecurity agencies as potentially vulnerable access points for hackers to exploit.
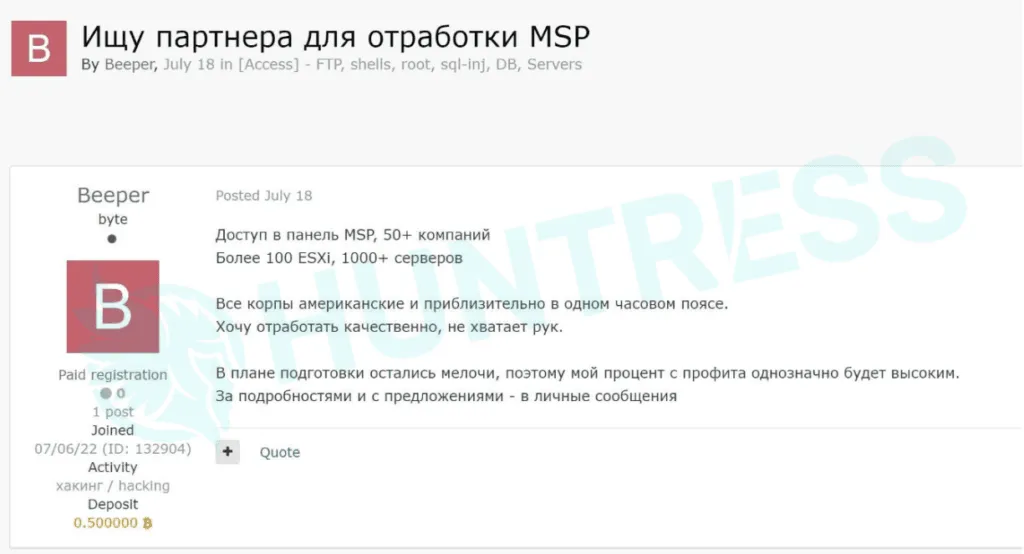
Harlan Carvey, senior incident responder at cybersecurity firm Huntress, told The Record that on July 18 someone with the handle “Beeper” had posted in Russian on exploit[.]in asking for help monetizing access to a managed service provider.
“Looking for a Partner for MSP processing. I have access to the MSP panel of 50+ companies. Over 100 ESXi, 1,000+ servers ... I want to work qualitatively, but I do not have enough people,” the translated message said.
“In terms of preparation, only little things are left, so my profit share will be high. Please send me a message for more details and suggestions.”
Several cybersecurity experts have shared the message on Twitter and other social media sites warning of the potential fallout from the kind of access the hacker purportedly has.
Carvey said it appears that the hacker gained access to an MSP's management system and has already done some of the initial legwork.
“It sounds as if they're claiming to have done some pre-work, perhaps something like identifying an account with a high privilege level. As a result, anyone who takes them up on their offer isn't going to have to do much ‘heavy lifting’ to achieve whatever their goals may be,” Carvey said. “It doesn't appear that there's any data involved at this point, per se. Intent isn't clear at this point, and it may depend upon who responds to the ad. The original poster does seem to be offering to answer questions and provide additional details.”
Carvey added that based on the typical customer base he sees for MSPs, personal details, business data and healthcare information could be at risk.
Some online noted that Kansas City-based MSP NetStandard announced on Wednesday morning that their hosted environment had been hit by a cyberattack. The company did not respond to requests for comment but told customers they discovered the attack on Tuesday and are “working to isolate the threat and minimize impact.”
“MyAppsAnywhere services, which include Hosted GP, Hosted CRM, Hosted Exchange, and Hosted Sharepoint, will be offline until further notice,” the company said.
“At this point, no additional information on the extent of the impact nor time to resolution can be provided. We are engaged with our cybersecurity insurance vendor to identify the source of the attack and determine when the environment can be safely brought back online.”
MSP NetStandard have been hit with ransomware HT @secboyuk pic.twitter.com/QwiL6JyQBj
— Kevin Beaumont (@GossiTheDog) July 27, 2022
The cybersecurity authorities of the U.K. (NCSC-UK), Australia (ACSC), Canada (CCCS), New Zealand (NCSC-NZ), and the United States (FBI, CISA and NSA) warned in May that hackers and APT groups have stepped up their targeting of MSPs in their efforts to exploit provider-customer network trust relationships.
Two of the most prominent hacks from the last two years involved popular MSPs – SolarWinds and Kaseya – and caused widespread damage due to the access they have to hundreds of companies and government agencies.
The CISA alert noted that government agencies are aware of reports of an increase in malicious cyber activity targeting MSPs, adding that they “expect this trend to continue.”
“As this joint advisory makes clear, malicious cyber actors continue to target managed service providers, which can significantly increase downstream risk to the businesses and organizations they support – why it’s critical that MSPs and their customers take action to protect their networks,” said CISA Director Jen Easterly.
Managed service providers make attractive targets for malicious actors to scale their attacks. MSPs and their customers should use these recommendations for handling the shared responsibilities of securing sensitive data. https://t.co/pZPluNVLQr
— Rob Joyce (@NSA_CSDirector) May 11, 2022
The agencies provided a range of recommendations to MSPs, such as hardening defenses against password spraying and phishing by potential attackers.
Former Obama administration cybersecurity commissioner Tom Kellermann, who now serves as head of cybersecurity strategy at VMware, previously told The Record that cybercrime cartels have studied the interdependencies of financial institutions and have a better understanding of which MSPs are used.
“In turn, these organizations are targeted and hacked to island hop into banks. Rogue nation states love this method of cyber-colonization,” Kellermann explained, referring to an attack that targets a third party in order to gain access to another entity. VMware has found that such attacks have increased 58% over the past year.
“I am concerned that as geopolitical tension metastasizes in cyberspace, these attacks will escalate and Russian cyber-spies will use this stratagem to deploy destructive malware across entire customer bases of MSP,” he said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



