Experts fear LockBit spread after ransomware builder leaked
A toolkit to create DIY versions of the LockBit ransomware has leaked, raising alarms among incident responders and cybersecurity experts warning of more widespread use in attacks.
The leak, for the LockBit 3.0 ransomware encryptor, was announced on Wednesday by security researcher 3xp0rt.
Unknown person @ali_qushji said his team has hacked the LockBit servers and found the possible builder of LockBit Black (3.0) Ransomware. You can check it on the GitHub repository https://t.co/wkaTaGA8y7 pic.twitter.com/cPSYipyIgs
— 3xp0rt (@3xp0rtblog) September 21, 2022
Several experts and researchers confirmed to The Record that the builder works and allows anyone to create their own ransomware.
In a message shared by 3xp0rt, someone allegedly connected to LockBit addressed the issue, attributing the leak to a disgruntled affiliate and dismissing the idea that what was stolen could be used by others to replicate what the ransomware group does.
Full LockBit's comment. I hope this programmer is educated and will leak source codes. pic.twitter.com/qiV2VTNicH
— 3xp0rt (@3xp0rtblog) September 21, 2022
“An affiliate program is not a locker, it is a software package, and most importantly an impeccable reputation that no one can tarnish, no matter what software leaks occur," the LockBit representative allegedly said. “Few people will agree to pay randomly to a pentester [penetration tester] without a reputation, hoping for a successful decryption and deletion of stolen data.”
But several cybersecurity experts expressed significant concern about that very prospect. Emsisoft threat analyst Brett Callow compared the situation to last year’s leak of the builder for the Babuk Locker ransomware.
“As was the case when Babuk’s builder leaked, we may well see other threat actors use LockBit's, which would obviously complicate attribution,” he explained.
Huntress Senior Security Researcher John Hammond said less skilled adversaries gravitated to the Babuk ransomware tool because it was simple to customize and use.
“Even open-source tools ‘for educational, research purposes’ like HiddenTear or RAASNet can be weaponized by adversaries for the wrong reasons. It just goes to show how commoditized cybercrime has really become,” Hammond explained.
Recorded Future ransomware expert Allan Liska said his team has identified more than 150 “new” ransomware groups this year, most of them are using stolen Conti or REvil code.
"At this time last year, Recorded Future was collecting from about 45 active DLS, today it is more than 100. There is a real proliferation of ransomware groups, most using leaked/stolen code from other ransomware groups," Liska explained.
Dick O’Brien, principal intelligence analyst at Symantec Threat Hunter Team, said it is a “near certainty” that we will see other attackers reuse LockBit's source code.
According to O’Brien, Lockbit’s success is partly due to the fact that they have a very effective "payload" — a term used to describe what a virus, worm or Trojan is designed to do on a victim’s computer.
“Other ransomware operators could replace their payloads with rebranded variants of Lockbit and you could see some aspirant groups use this to launch their own ransomware operations,” he said. O'Brien also cautioned against "overstating" the leak's potential ramifications, saying payload is just one aspect of a ransomware operation.
“Attackers also need to have the capability to access the networks of a large pool of potential victims and also the ability to scale by creating the infrastructure needed for an affiliate program," he said. "None of this is easy."
Lockbit 3.0
Researchers have linked more than 1,029 attacks to LockBit since the group began its operation in 2019. The group was considered a marginal player until last year when it launched LockBit 2.0, a new version of its ransomware-as-a-service platform.
The group revamped again, launching LockBit 3.0 this summer and supplanting Conti as the most prolific criminal organization. The gang had at least 68 victims in August, including a crippling attack on a hospital about an hour southeast of Paris last month that disrupted its medical imaging, patient admissions, and other services.
About one-third of ransomware attacks targeting industrial systems in the second quarter were attributed to LockBit, according to cybersecurity firm Dragos.
Huntress’ Hammond explained that the latest edition of LockBit had new features and functionality to encrypt files faster than before.
He said the leak of the builder software commoditizes the ability to configure, customize, and ultimately generate the executables to not only encrypt but decrypt files.
“Anyone with this utility can start a full-fledged ransomware operation,” he said, pointing to a screenshot of the leaked configuration file. “That is so customizable – note how the ransom note can be completed changed.”
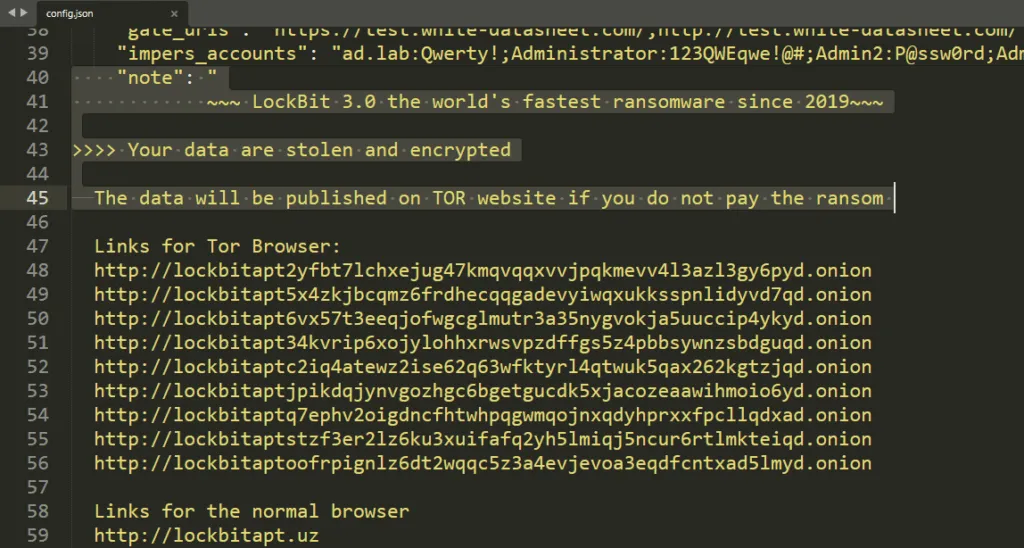
According to Hammond, the encryptor could delete event logs, interfere with processes and potentially move throughout the network and disable antivirus protections.
One small upside of the leak may be that security experts can analyze and explore this builder software and potentially garner new threat intelligence that could thwart ransomware operations, Hammond said.
At a minimum, the leak gives cybersecurity experts greater insight into the inner-workings of LockBit, with the message from LockBit indicating that they have contracted developers and that they suffer from insider threats.
Liska said the leak could be a sign of disgruntled factions within the LockBit group.
“These large RaaS groups are notorious for paying their developers, IABs [Initial Access Brokers] and other support staff poorly, so that is not necessarily a surprise,” he said.
A pattern of builder leaks
The LockBit leak also follows the appearance of a Conti ransomware builder leaked earlier this year.
Hammond told The Record that after the Conti Leaks were made freely available, the Conti ransomware builder “gained mass adoption from other threat actor groups wanting to quickly and easily spin up their own ransomware operation.”
“Money is the real motive, and when a tool like this is made available, it enables anyone to run the racket,” he said.
Even though it is customizable, the encryptor still changes the victim wallpaper to say "Lockbit Black,” according to Hammond, who noted that more skilled operators may try to change that. More low-tier groups, meanwhile, may even want the legitimacy of “looking like” a LockBit attack.
The publicity around the leak may scare many cybercriminals away considering how “easily fingerprinted and well-known” the builder is now by experts, he added.
Liska said that based on what was seen with Conti, it is likely criminal groups will build their own LockBit.
“Which means, in a year which has already seen the fracturing of ransomware groups, we’ll likely see even more ‘new’ groups spring up,” he said.
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.



