Experts concerned about ransomware groups creating searchable databases of victim data
Several ransomware gangs and extortion groups are creating searchable databases of information stolen during attacks, according to several cybersecurity experts.
Ransomware groups have long extorted organizations with the threat of data leaks, but often leave the stolen data on leak sites buried on the dark web.
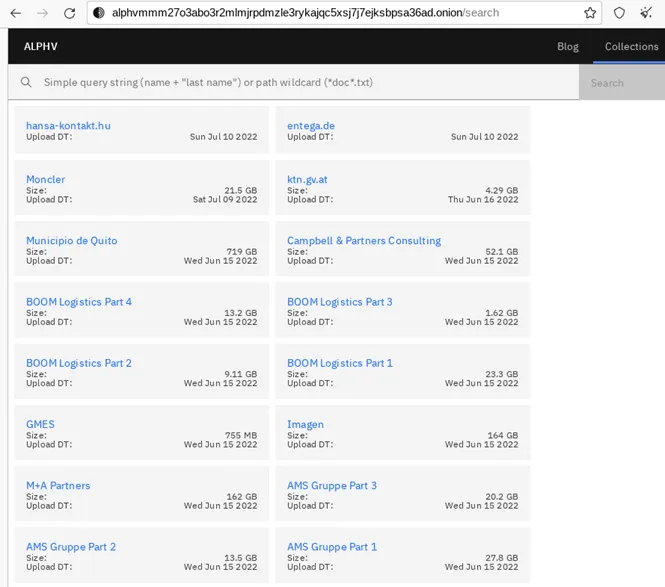
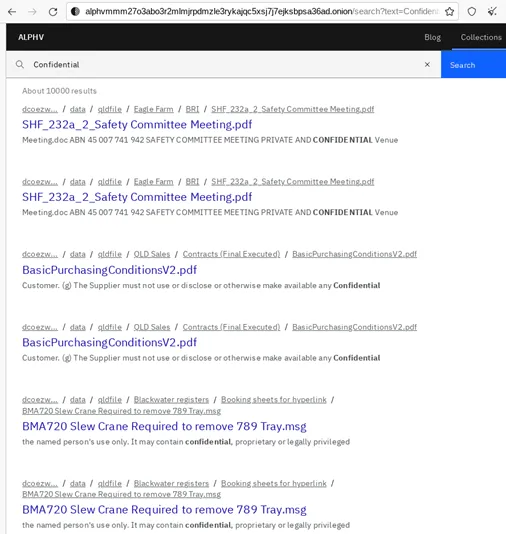
Over the last month, ransomware groups AlphV and LockBit have debuted features on their leak sites that allow anyone to search through troves of data by company name or other signifiers.
ALPHV ransomware group (alternatively referred to as BlackCat ransomware group) put out a message today to its affiliates
— vx-underground (@vxunderground) July 5, 2022
In summary: they are creating a searchable database of individuals and/or companies who do not pay. pic.twitter.com/p1KWyr7e8j
Lockbit ransomware group has created a new domain. This domain contains victims data leaks in "files". This domain stores the data of past and present victims.#lockbit #ransomware pic.twitter.com/CpjaPho5pB
— Tom Malka (@ZeroLogon) July 9, 2022
Bleeping Computer also reported that the Karakurt extortion group has created a similar functionality.
Tenable senior staff research engineer Satnam Narang confirmed to The Record that all three groups have incorporated some kind of searchable database functionality into their leak sites.
Narang said that while most groups are simply making the information they steal available, other extortion groups may include data exfiltrated by other groups or individuals in the ransomware ecosystem.
“What stood out most to me was how the collections have been implemented. In the case of ALPHV, it’s fairly robust as you’re able to search within the data, whereas LockBit’s version is more limited, though this could change at any moment,” Narang explained.
Narang and other ransomware experts listed several reasons why ransomware groups would begin creating tools like this.
Emsisoft threat analyst Brett Callow said the tactic is designed to increase pressure on organizations by weaponizing their customers and business partners.
“The gangs likely believe that making the data available in this way will result in more companies paying due to a perceived increase in the potential for reputational harm. And they may even be right,” Callow said.
He added that companies have been able to dodge accountability by claiming there is “no evidence user data has been misused” – a line seen in hundreds of breach notification letters over the last few years.
“Soothing statements like that aren’t really possible when people know their personal information was exfiltrated, compiled into an individual downloadable pack and made available online,” Callow explained.
Recorded Future ransomware expert Allan Liska expressed worry that if the trend catches on, other ransomware groups will follow.
The recent phenomenon addresses one of the biggest challenges associated with extortion sites: finding relevant data for victims is impossible, Liska told The Record.
He added that the point of extortion sites is to make victims more likely to pay a ransom if the prospect of not decrypting their data isn't enough.
“No one wants sensitive organizational or customer data leaked, for a variety of reasons. But, when leaked data is just dumped online it is hard to tell what is up there,” he explained.
“Some ransomware groups have tried to organize the data in a way they think is meaningful, but mostly it is just a morass of data that isn't useful to anyone. This makes extortion sites less useful as a tool to compel ransom payments. If ordinary people can't find relevant data then having data dumped isn't that ‘scary.’”
By making the data searchable, ransomware groups are hoping to make it easier for anyone to find sensitive data, which now makes the idea of exposing sensitive data on extortion sites a compelling reason to pay again, Liska noted.
“At least that is the hope of the ransomware groups,” he said.
Narang said the new features are yet another extortion tool on top of several others cybersecurity officials have seen evolve over the last few years since double extortion became a prominent fixture in the ransomware ecosystem.
According to Narang, some ransomware groups are trying things like distributed denial-of-service attacks and stolen data auctions while others have gone as far as contacting customers and employees of victim organizations.
“Some have called these tactics ‘triple extortion’ or ‘quadruple extortion,’ though, whatever you choose to call it, these tactics remain part of the same extortion tree,” Narang said.
“The more layers of extortion, the more pressure is placed on victims to pay up. We know that the threat of publishing stolen files has provided enough incentive for some victims to pay up even though they’re able to restore systems. As a side effect of this, the collections component brings the stolen data front and center and allows other cybercriminals the ability to possibly take the stolen data and use it against third-parties that weren’t directly victims of the original ransomware attack.”
Jonathan Greig
is a Breaking News Reporter at Recorded Future News. Jonathan has worked across the globe as a journalist since 2014. Before moving back to New York City, he worked for news outlets in South Africa, Jordan and Cambodia. He previously covered cybersecurity at ZDNet and TechRepublic.