Attackers use EvilProxy phishing kit to take over executives’ Microsoft 365 accounts
Threat actors have been using the phishing toolkit EvilProxy to take control of cloud-based Microsoft 365 accounts belonging to executives at prominent companies, researchers have found.
The cybersecurity firm Proofpoint, which released a report on the incidents Wednesday, said the attacks exhibited both the prevalence of pre-packaged phishing-as-a-service toolkits, as well as the increased bypassing of multi-factor authentication to gain access to accounts.
In all, Proofpoint observed the targeting of more than 100 organizations with EvilProxy, with 35% of the compromised accounts being MFA-enabled. More than one-third of the accounts belonged to C-level executives, including CEOs and chief financial officers.
“As our research shows, threat actors often target specific job functions or departments, and their methods and techniques must constantly evolve, such as finding ways to bypass multi-factor authentication,” Proofpoint said. “Contrary to popular belief, not even MFA is a silver bullet against sophisticated cloud-based threats.”
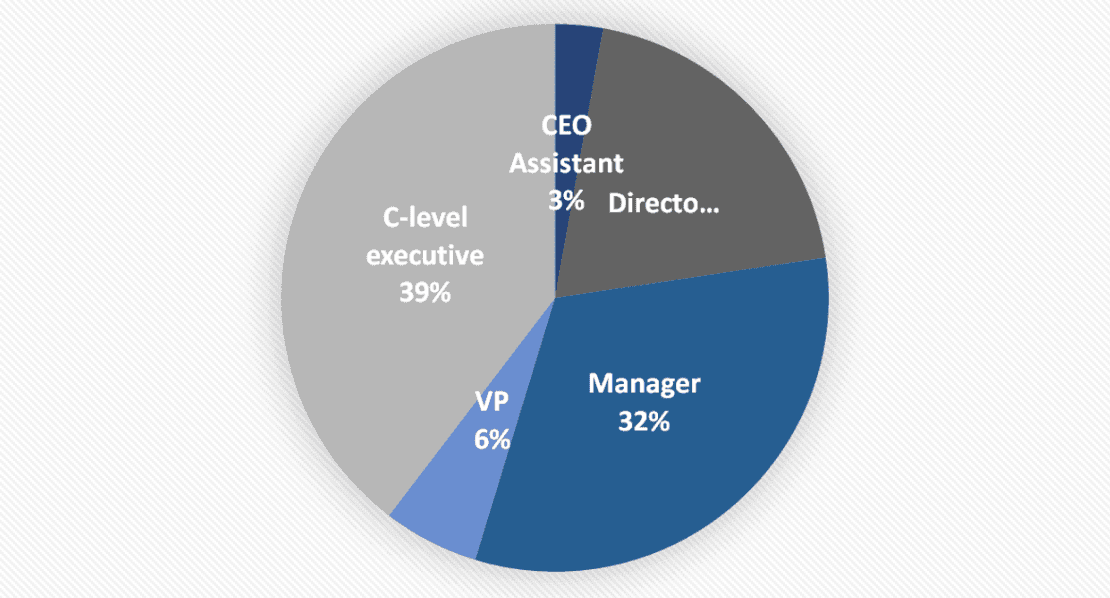 Roles of individuals compromised in the attacks. Image: Proofpoint
Roles of individuals compromised in the attacks. Image: Proofpoint
The EvilProxy kit uses what is known as an adversary-in-the-middle technique, in which communications between a device and websites are intercepted by a bad actor. Between March and June 2023, Proofpoint observed 120,000 phishing emails sent out, usually impersonating brands like Adobe and DocuSign.
When a recipient clicks on the malicious emails, after a series of redirects they are taken to a phishing page that reverse proxies the login page for Microsoft 365. When a victim enters their credentials, the tool steals authentication cookies, allowing the hackers to bypass MFA.
Once they gain access, threat actors attempt to establish persistence on the account, in some cases setting up their own MFA method.
“During those last phases, cyber criminals employ various techniques, including lateral movement and malware proliferation. The attackers have been known to study their target organizations’ culture, hierarchy, and processes, to prepare their attacks and improve success rates,” researchers wrote. “In order to monetize their access, attackers were seen executing financial fraud, performing data exfiltration or partaking in Hacking-as-a-Service (HaaS) transactions, selling access to compromised user accounts.”
The EvilProxy kit was first detected in May 2022, according to the cybersecurity company Resecurity, when its developers posted a video tutorial on its use. As of last fall, the package was available on the dark web for $400.
James Reddick
has worked as a journalist around the world, including in Lebanon and in Cambodia, where he was Deputy Managing Editor of The Phnom Penh Post. He is also a radio and podcast producer for outlets like Snap Judgment.


