Europol: Seven REvil/GandCrab ransomware affiliates were arrested in 2021
Europol has announced today the arrests of seven suspects who worked as "affiliates" (partners) for a major ransomware cartel and have helped carry out more than 7,000 attacks since early 2019.
The suspects worked part of the REvil (Sodinokibi) and GandCrab Ransomware-as-a-Service (RaaS) operations.
Both REvil and GandCrab, believed to be operated by the same individuals, created ransomware code that they offered to other cybercriminals for rent.
These renting groups, more commonly known as "affliates," would orchestrate intrusions into companies, deploy the ransomware, ask for a ransom, and then split the profits with the REvil/GandCrab coders.
Europol says that since 2019, the seven suspects carried out attacks in which they collectively asked for more than €200 million ($230 million) in ransom demands.
Since February this year, Europol said it's been working with law enforcement agencies and security firms such as Bitdefender, KPN, and McAfee, to apprehend some of these affiliate groups. According to Europol, arrests have been made in:
- February, April, October - three REvil and GandCrab affiliates arrested in South Korea
- October - one REvil affiliate arrested in Poland (charged for the Kaseya REvil attacks)
- November 4 - two REvil affiliates arrested in Constanta, Romania
- November 4 - one GandCrab affiliate arrested in Kuwait
The arrests come after western countries, led by the US, promised to crack down on ransomware gangs earlier this summer.
The decision to go after ransomware operators comes after ransomware attacks hit their peak this year, with groups launching attacks that crippled industry sectors for days — such as the attack on Colonial Pipeline this May, which stopped 45% of all fuel supply to the US East Coast.
Bitdefender, which participated in the Europol-led crackdown against the GandCrab/REvil gang, also released a universal decrypter for past REvil victims on September 16. The Romanian company also released free decrypters for the GandCrab version, all of which can be downloaded from the NoMoreRansom portal.
An eight GangCrab affiliate was detained in Belarus, in August 2020, but the arrest was not part of the Europol joint investigation.
A video of the arrests that took place in Romania is below, via DIICOT: pic.twitter.com/RUmTTbNj6s
— Catalin Cimpanu (@campuscodi) November 8, 2021
A short history of the GandCrab and REvil operations
First advertised in January 2018, the GandCrab RaaS was initially a run-of-the-mill group who rented its code to cybercrime groups who used spam emails laced with malicious file attachments to infect users.
The group shifted its targeting at the start of 2019, when they began working with a small group of affiliates to target managed service providers in attacks aimed at corporate organizations, hoping to shift from the small ransom demands they could extract from small home users to the larger ransoms they could demand from companies whose networks they crippled.
As this new method of attack started yielding greater profits, the group shut down their GandCrab operation in May 2019, and released a rebranded and improved version of their ransomware a month later, in June 2020.
Known as REvil or Sodinokibi, this new RaaS portal only worked with affiliates who were willing to attack larger companies. Across the years, the REvil RaaS and its affiliates have been linked to some pretty large attacks against companies such as Apple, Acer, Telecom Argentina, and many more.
According to an IBM report published in February 2021, the REvil operation is believed to have earned around $123 million in 2020 alone.
However, two attacks, against JBS Foods and Kaseya servers, in May and July this year, respectively, crossed the line in what the US government was willing to take. The JBS Foods attack caused massive distruptions to meat supply across the US, while the attack on Kaseya servers caused thousands of IT networks to go down across the world on the July 4 holiday.
The group shut down a week later, without any kind of explanation, with the group's leader, an individual going by the name of Unknown, seemingly disappearing from underground forums.
Some of the REvil coders tried to resuscitate the operation in September, but they shut down after a month, after an unknown third party had hijacked their Tor server infrastructure.
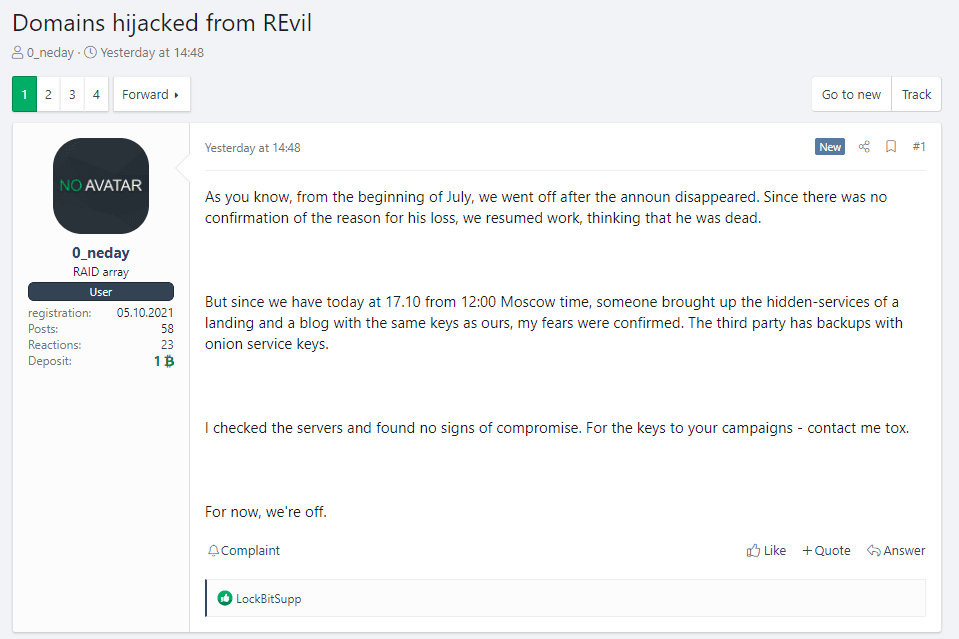
Reports from Reuters and the Washington Post later revealed that by July, the group's servers were already hacked and backdoored by a foreign law enforcement agency, which had been keeping an eye on the group's operations.
When the group made a comeback in September, it was US Cyber Command that hijacked its servers, not knowing of the law enforcement operation. However, this hijack spooked the REvil gang into what appears to be a final retirement, and possibly the reason why Europol and the other law enforcement groups are moving in on the GandCrab/REvil affiliates they managed to identify so far.
REvil shut down last month after CyberCom hijacked its site and the group discovered it had been hacked (by a foreign govt). Was not a take-down, but the pair of actions spooked REvil, officials & analysts say. My latest w/ @DDaltonBennett https://t.co/MR5IdxDUBD
— Ellen Nakashima (@nakashimae) November 3, 2021
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



