European governments targeted by Chinese hackers with a Zimbra webmail zero-day
A new Chinese cyber-espionage group has been seen abusing a zero-day vulnerability in the Zimbra collaboration suite to gain access to the email inboxes of European governments and media agencies.
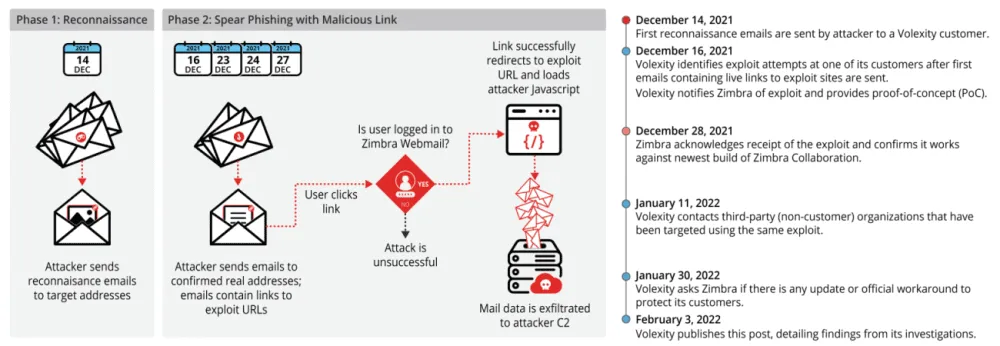
The attacks were spotted last month by security firm Volexity, and even if the security firm notified Zimbra on December 16, the company has not yet released a patch for its product.
Earlier today, Volexity has released a technical report about the attacks in the hopes to raise awareness of this issue and allow organizations that use a Zimbra email server to review if they have been targeted.
Hackers stole cookies to access targeted accounts
According to Volexity, the attackers first began exploiting this zero-day on December 14, when its researchers spotted the initial attacks on some of its customers.
Volexity said the attacks were split into two stages. In the first, the hackers sent a benign email meant to perform reconnaissance and determine if accounts were active and if users would be willing to open strange emails from unknown entities.
The actual attack took place in a second email when the hackers would include a link in the email body. If users accessed the URL, they would land on a remote website where malicious JavaScript code would execute a cross-site scripting (XSS) attack against their organization's Zimbra webmail application.
The Volexity team said this code exploited an issue in Zimbra webmail clients running versions 8.8.15 P29 & P30 and would allow the attackers to steal the Zimbra session cookie files.
These files would then allow the attackers to connect to a Zimbra account, from where they would gain access to emails, send additional phishing messages to a user's contacts, and even prompt users to download malware.
While there are currently more than 33,000 Zimbra servers connected to the internet, Volexity said that the zero-day doesn't work against Zimbra 9.x installs, which are the most recent version of the platform, meaning that the attack surface is not as large as initially thought.
Volexity links hackers to China
The security firm said that based on the attacker's infrastructure used in these attacks, they have not been able to link this threat actor, which they have named TEMP_Heretic, to a previously known group or activity cluster.
Nonetheless, based on the techniques used in the attacks, Volexity said they believe "the attacker is likely Chinese in origin."
The security firm said that based on its visibility, it has seen TEMP_Heretic attacking European governments and media agencies; however, the group is believed to have attacked many more other targets.
IT administrators who run Zimbra email servers and would like to know if they have been targeted are advised to check the Volexity report. The security firm said TEMP_Heretic usually used emails posing as invitations, refunds, warnings, and emails with no subject lines as lures for their attacks.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.



