Dutch man gets two years in prison for hijacking 13,762 online store accounts
A Dutch man was sentenced last week to 27 months in prison and a €10,000 ($11,800) fine for breaking into 13,762 accounts at Dutch online stores.
The man, a 27-year-old from the Dutch city of Arnhem, was found guilty of buying 3.7 million login credentials and using automated tools to test if the logins were still valid.
According to Dutch officials, the man successfully accessed 13,762 accounts where the passwords were still in use.
In case of a successful intrusion, the hacker used any financial details present in the account to buy luxury goods which he later shipped to his home address.
While the Dutch Judiciary did not release the suspect's name or the name of the vandalized shops, the sentencing represents one of the largest of its kind in the Netherlands for any account takeover-related crimes.
In fact, the judge sentenced the man to 27 months in prison, close to the 30-month sentence requested by the prosecution as punishment for the crime's breadth and severity.
ATO attacks in a constant rise for years
These types of intrusions, known as account takeover (ATO) incidents, have grown in number and frequency in recent years, driven by the ever-increasing number of security breaches that often result in the public disclosure of login details.
Furthermore, a flourishing cybercrime black market has also expanded in recent years, making it easier for hackers to sell hacked databases to online fraud groups — via hacking forums, dark web marketplaces, or via Discord and Telegram channels.
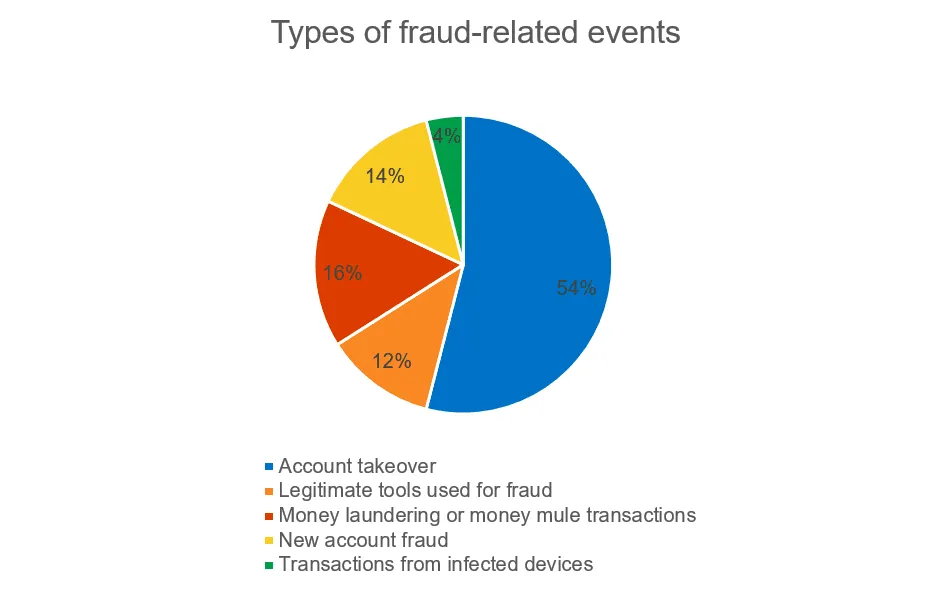
According to statistics gathered by cybersecurity giant Kaspersky, in 2020, every second fraudulent transaction in the finance industry was linked to an account takeover attack.
In addition, the share of ATO incidents in the totality of fraud-related crimes had increased from 34% in 2019 to 54% in 2020, a 20% rise that came during a time when people were more reliant on online shopping due to the ongoing coronavirus (COVID-19) pandemic.
With such crimes now becoming more common, we should expect law enforcement to crack down on the operators of botnets that are often used to carry out ATO, brute-force, dictionary-based, password spraying, or credential stuffing attacks.
Catalin Cimpanu
is a cybersecurity reporter who previously worked at ZDNet and Bleeping Computer, where he became a well-known name in the industry for his constant scoops on new vulnerabilities, cyberattacks, and law enforcement actions against hackers.

